Phileas Project Bots vs. Spyware
Phileas project uses bots to ferret out spyware, a groundbreaking initiative designed to proactively identify and neutralize malicious software. This project delves into the intricate world of cybersecurity, exploring how automated systems are employed to detect and analyze various forms of spyware. The project’s comprehensive approach, encompassing bot deployment strategies, spyware detection methods, data analysis, and ethical considerations, paints a detailed picture of the modern fight against cyber threats.
The project’s core mission is to safeguard digital environments from harmful intrusions. It employs a multi-faceted strategy, leveraging automated tools to swiftly identify spyware across diverse platforms. The Phileas Project’s focus extends beyond mere detection, aiming to provide detailed insights into spyware techniques and vulnerabilities, enabling better security practices in the future.
Project Overview
The Phileas Project is a comprehensive initiative dedicated to combating the insidious threat of spyware. Its core mission is to proactively identify, analyze, and neutralize spyware across various digital platforms. This includes a wide range of methods, from sophisticated algorithms to human-led investigations. The ultimate goal is to create a safer digital environment for individuals and organizations worldwide.The project employs a multi-faceted approach to security.
The Phileas Project’s use of bots to sniff out spyware is fascinating, especially when you consider the broader context of the insane world of home electronics and media distribution. The insane world of home electronics 2 media distribution is a wild place, packed with devices constantly exchanging data, which makes it all the more crucial to understand how to protect against potential threats like spyware.
Ultimately, the Phileas Project’s efforts in uncovering these threats are incredibly important for keeping our personal data safe in this increasingly interconnected digital landscape.
This involves advanced machine learning models for automated detection, coupled with a dedicated team of security analysts who conduct in-depth investigations into identified threats. The methodology prioritizes open-source intelligence and collaboration with security researchers, fostering a dynamic and ever-evolving strategy to counteract evolving spyware techniques.
Types of Spyware Targeted
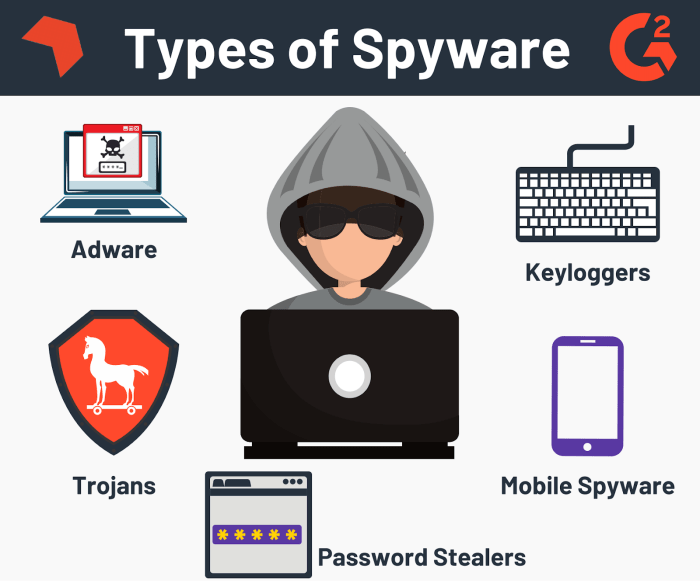
The Phileas Project targets a broad spectrum of spyware, encompassing various malicious functionalities. This includes keyloggers, which record keystrokes, allowing access to sensitive information such as passwords and credit card details. Additionally, the project targets screen recorders, capable of capturing video and audio from the user’s screen, potentially recording confidential conversations or activities. Other targets include data stealers, designed to exfiltrate personal and sensitive data from infected systems.
The project also addresses mobile spyware, often used for tracking and monitoring users on smartphones and tablets. Finally, the project is equipped to address rootkits, which can gain administrative control over a system, often enabling persistent and undetectable malicious activities.
The Phileas Project’s use of bots to sniff out spyware is fascinating, but it also highlights the broader need for robust cybersecurity solutions. This sort of proactive approach, combined with developments like the recent microsoft citrix seal terminal server deal , could revolutionize how we approach protecting sensitive data. Ultimately, the Phileas Project’s innovative methods underscore the importance of continuous vigilance in the ever-evolving digital landscape.
Real-World Spyware Scenarios
Spyware has been used in numerous malicious activities across diverse industries. For example, in political campaigns, spyware has been deployed to gather intelligence on opponents, potentially influencing election outcomes. In corporate espionage, spyware has been utilized to steal trade secrets and intellectual property, leading to significant financial losses. Additionally, spyware is employed in criminal activities, such as tracking victims or monitoring financial transactions.
A significant concern lies in the use of spyware for targeted harassment and stalking, enabling the perpetrator to monitor and control the victim’s activities.
Phases of the Phileas Project
The Phileas Project is structured into distinct phases, each with specific timelines and responsibilities. This structured approach ensures a systematic and effective implementation of the project’s goals.
| Phase | Timeline | Responsibilities |
|---|---|---|
| Phase 1: Infrastructure Development | Q1 2024 | Establishing the necessary infrastructure, including servers, data storage, and security systems. Development and testing of core algorithms. |
| Phase 2: Data Acquisition and Analysis | Q2 2024 | Gathering and analyzing data on existing spyware threats and attack vectors. This includes examining malware samples, open-source intelligence, and community reports. |
| Phase 3: Model Training and Refinement | Q3 2024 | Training and refining machine learning models for automated detection and analysis. Integration of expert human analysis into the detection process. |
| Phase 4: Public Release and Collaboration | Q4 2024 | Launching the Phileas Project’s detection tools and services to the public. Fostering collaboration with researchers and organizations to enhance the project’s capabilities. |
Bot Deployment Strategies
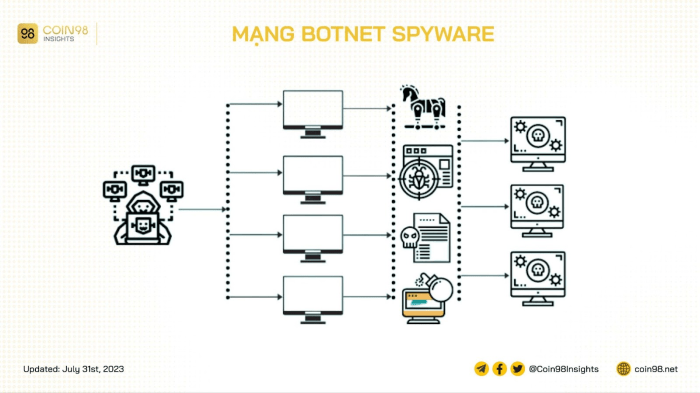
The Phileas Project leverages sophisticated bot deployment strategies to effectively identify and analyze spyware, a critical task in today’s digital landscape. These bots act as digital sentinels, tirelessly scanning for malicious code and patterns, safeguarding users from potential threats. The intricate network of bots enables a multifaceted approach to threat detection, from initial reconnaissance to in-depth analysis.The core of the Phileas Project’s strategy is a distributed bot network.
This architecture allows for rapid scalability and resilience, enabling the system to adapt to evolving threats. This approach distributes the workload across numerous bots, each performing specific tasks within a unified framework. This decentralization also contributes to the project’s overall security by minimizing the impact of a potential compromise on any single node.
Bot Deployment Methods
The Phileas Project utilizes a combination of deployment methods to maximize its effectiveness. These include targeted deployments to specific networks known to be at risk, as well as passive monitoring of publicly available resources. This dual approach allows for both proactive and reactive responses to potential threats. Additionally, the system adapts dynamically, adjusting its deployment strategy based on real-time threat intelligence and observed patterns.
Technical Specifications
The Phileas Project’s bots are built using a combination of cutting-edge technologies. Key programming languages include Python and Go, leveraging their strengths in scripting and performance, respectively. Modern frameworks like TensorFlow and PyTorch are incorporated for advanced machine learning tasks, such as pattern recognition and anomaly detection. The bots’ architectures are modular, enabling easy maintenance and updates. This modularity also allows for customization of specific bots for particular tasks, such as network traffic analysis or file system scanning.
Capacity for Analysis and Data Collection
These bots possess a significant capacity for analysis and data collection. They are equipped to collect vast amounts of data from various sources, including network traffic, system logs, and file metadata. This data is processed through a sophisticated pipeline, filtering out irrelevant information and highlighting potential threats. The project utilizes machine learning algorithms to identify patterns and anomalies that may indicate the presence of spyware.
These algorithms are continuously updated to adapt to new techniques employed by malicious actors. Sophisticated data normalization techniques ensure consistency and accuracy in the analysis process.
Security Considerations and Risks
Deploying bots carries inherent security risks. A primary concern is the potential for misuse or unauthorized access to the bot network. Rigorous security measures, including secure communication channels and access controls, are implemented to mitigate these risks. Furthermore, the bots’ ability to collect and analyze vast amounts of data necessitates stringent data privacy protocols and compliance with relevant regulations.
Comparison of Bot Architectures
| Bot Architecture | Strengths | Weaknesses |
|---|---|---|
| Centralized | Simplified management, easier debugging | Single point of failure, potential bottleneck |
| Decentralized | High resilience, scalable, distributed workload | Complex management, potential inconsistencies in data collection |
| Hybrid | Combines benefits of both centralized and decentralized | More complex to implement and maintain |
Spyware Detection Methods: Phileas Project Uses Bots To Ferret Out Spyware
The Phileas Project employs a multi-layered approach to spyware detection, combining static analysis of code with dynamic monitoring of system behavior. This multifaceted strategy significantly enhances the accuracy and comprehensiveness of the detection process. By combining various techniques, the project is better equipped to identify and neutralize diverse spyware threats, protecting user systems from harm.The Phileas Project’s spyware detection process leverages a combination of signature-based detection, anomaly detection, and behavioral analysis.
These methods work together to identify malicious code patterns and distinguish between legitimate and malicious software. The core principle is to identify deviations from normal system behavior, flagged as potential spyware.
Signature-Based Detection
This method relies on identifying known malicious code patterns, or “signatures.” These signatures are essentially digital fingerprints of specific spyware programs. The project maintains a constantly updated database of these signatures, allowing for rapid identification of known threats. The process involves comparing the code of suspected files against the database of signatures. A match indicates the presence of spyware.
This method is effective against well-known spyware but can be less effective against newly emerging or polymorphic threats.
Anomaly Detection
This approach focuses on identifying deviations from expected system behavior. The Phileas Project monitors system resources (CPU usage, memory consumption, network activity, file access) and looks for unusual patterns that might indicate spyware activity. For example, a sudden and significant spike in network traffic or a program accessing sensitive system files without authorization could trigger an alert. This method helps detect previously unknown or evolving spyware by recognizing atypical behaviors.
Behavioral Analysis
This method goes beyond static code analysis and examines the dynamic behavior of the software. The Phileas Project analyzes how the software interacts with the operating system, other applications, and network resources. Malicious software often exhibits specific behavioral patterns, such as attempting to steal passwords, logging keystrokes, or modifying system settings. By observing these actions, the project can identify potentially malicious software.
This method is particularly valuable for detecting polymorphic and zero-day spyware.
Identifying Malicious Code Patterns
The Phileas Project utilizes sophisticated algorithms to analyze code for patterns indicative of malicious intent. This includes looking for code that attempts to evade detection mechanisms, access restricted system resources, or communicate with known malicious servers. These algorithms are continually refined to identify new and emerging patterns, keeping pace with evolving threats.
Examples of Spyware Techniques and Detection
One common technique is “rootkits,” which hide malicious code by modifying the operating system. The Phileas Project detects rootkits by monitoring system calls and file access patterns. Keyloggers are another example, designed to record keystrokes. The project detects keyloggers by analyzing the behavior of the software, looking for unusual activity related to keystroke capture. Other examples include adware and spyware that monitor browsing habits.
These are detected through the project’s analysis of web traffic and resource usage.
Differentiating Between Legitimate and Malicious Software
The Phileas Project distinguishes between legitimate and malicious software through a combination of static and dynamic analysis. It compares the software’s code to a database of known legitimate programs and looks for suspicious behaviors. Contextual analysis is also crucial, considering the source of the software and its behavior within the system. A legitimate program would not, for instance, attempt to access sensitive files without authorization or attempt to conceal its activity.
Spyware Categories and Detection Techniques
| Spyware Category | Detection Technique(s) |
|---|---|
| Rootkits | Monitoring system calls, file access patterns, behavioral analysis |
| Keyloggers | Behavioral analysis, monitoring input/output events |
| Adware | Analysis of web traffic, resource usage, and program behavior |
| Trojans | Signature-based, behavioral analysis, anomaly detection |
| Malware | Signature-based, behavioral analysis, anomaly detection |
Data Analysis and Reporting
The Phileas Project relies heavily on the data collected by its bots to identify and analyze spyware threats effectively. This crucial step involves processing vast amounts of information, transforming raw data into actionable intelligence, and presenting it in a digestible format for analysts and stakeholders. The data analysis process is not just about finding patterns; it’s about understanding the context behind those patterns and using them to proactively mitigate potential risks.The analysis process goes beyond simple identification.
It delves into the intricacies of the collected data to understand the tactics, techniques, and procedures (TTPs) employed by spyware developers. By studying these patterns, the project can anticipate future threats and proactively adapt its detection strategies.
Data Analysis Processes
The data collected by the Phileas Project bots is initially stored in a secure, centralized database. This database is structured to allow for efficient querying and analysis. Sophisticated algorithms are used to identify anomalies, patterns, and correlations within the data. These algorithms are continuously refined based on the evolving landscape of spyware threats. The primary processes involved are:
- Data Cleaning and Preprocessing: Raw data collected from various sources is meticulously cleaned to remove errors, inconsistencies, and irrelevant information. This ensures the accuracy and reliability of subsequent analyses. This step is crucial, as inaccurate or incomplete data can lead to flawed conclusions.
- Feature Extraction and Selection: Relevant features are extracted from the cleaned data, and less important or redundant data points are filtered out. This step focuses on isolating the most informative elements for analysis, ensuring that resources are directed toward the most crucial aspects of the data. This optimizes the efficiency of the analysis process.
- Pattern Recognition and Correlation Analysis: Advanced algorithms are applied to detect patterns and correlations between different data points. This helps identify potential indicators of spyware presence or activity, such as unusual network traffic, suspicious file modifications, or anomalous system behavior. The identification of these correlations is critical to determining whether suspicious activity is truly malicious or a false positive.
- Anomaly Detection: Algorithms are used to identify deviations from normal behavior. This process helps to highlight potential spyware instances that might not fit easily into pre-defined patterns.
Types of Reports Generated
The Phileas Project generates various reports to effectively communicate the findings to stakeholders. These reports vary in detail and purpose, ensuring that information is presented in a manner that is both understandable and actionable.
The Phileas Project’s use of bots to sniff out spyware is a fascinating development, especially considering the recent cancellation of COMDEX, which signaled the end of an era in the tech industry. COMDEX cancellation marks end of era highlights how quickly the landscape changes, and it’s a reminder of how important proactive security measures like those employed by the Phileas Project are becoming in today’s digital world.
This project’s innovative approach to combating spyware is truly noteworthy.
- Daily Summary Reports: These reports provide an overview of the significant activities detected by the bots during the previous 24 hours. These reports highlight potential threats and provide a quick snapshot of the security landscape.
- Weekly Trend Reports: These reports provide a deeper analysis of trends observed over the past week, identifying emerging patterns and potential threat vectors. They also track the prevalence of specific types of spyware.
- Monthly Security Assessments: These reports offer a comprehensive review of the security landscape over the month, highlighting emerging threats, vulnerabilities, and the overall security posture. They provide valuable context and insight into the evolution of the threat landscape.
- Custom Reports: The project can generate tailored reports to address specific security concerns or inquiries from stakeholders, offering insights into specific types of spyware or vulnerabilities.
Data Visualization and Presentation
Visual representations of data are used to enhance understanding and comprehension. Charts and graphs are employed to present complex data in a readily understandable format.
- Bar Charts: Bar charts are used to compare the frequency of different types of spyware detected over time.
- Line Graphs: Line graphs display the trends of specific spyware detections over time, revealing potential patterns and helping analysts identify emerging threats.
- Heatmaps: Heatmaps visualize the correlation between various data points, highlighting areas of high activity or risk.
- Interactive Dashboards: Interactive dashboards allow users to explore data in greater detail, drill down into specific data points, and customize views.
Data Collection and Analysis Methodology
This table illustrates the different data points collected by the bots and the corresponding analysis methods applied.
| Data Point | Analysis Method |
|---|---|
| Network Traffic Patterns | Anomaly detection, correlation analysis |
| File System Modifications | Pattern recognition, anomaly detection |
| Registry Key Changes | Pattern recognition, anomaly detection |
| System Calls | Pattern recognition, anomaly detection |
| Process Behavior | Anomaly detection, behavioral analysis |
Data Security Measures
The security of the data collected by the bots is paramount. Robust security measures are in place to protect sensitive information.
- Encryption: Data is encrypted both in transit and at rest using industry-standard encryption protocols.
- Access Control: Strict access controls limit access to the data to authorized personnel only.
- Data Masking: Sensitive data is masked or anonymized to protect privacy and confidentiality.
- Regular Audits: Regular security audits are conducted to identify and address potential vulnerabilities.
Ethical Considerations
The Phileas Project, with its innovative use of bots for spyware detection, raises critical ethical questions. Balancing the potential benefits of enhanced cybersecurity with the inherent risks of privacy intrusion and potential misuse is paramount. This section explores the ethical implications of this technology, outlining potential pitfalls, and proposing safeguards for responsible deployment.
Potential for Misuse and Unintended Consequences
The power to automatically identify and analyze potential spyware is a double-edged sword. Misuse could lead to unwarranted surveillance of individuals or organizations. Automated systems, without appropriate safeguards, might misclassify legitimate software as spyware, resulting in false positives and unwarranted disruptions. A lack of transparency in the analysis process could erode public trust and invite accusations of bias.
Historical examples of surveillance technologies being used for oppressive purposes highlight the necessity of stringent ethical guidelines.
Necessary Safeguards for Responsible Use
Robust safeguards are essential to ensure the Phileas Project is used responsibly. These safeguards must include:
- Strict data minimization: Only collect and process the minimum amount of data necessary for spyware detection. This principle is crucial to limit the scope of potential privacy violations. Excessively broad data collection practices could encompass harmless information, leading to needless intrusion.
- Explicit user consent: Ensure users understand how their data is being used and obtain their explicit consent before employing the bot system for analysis on their systems.
- Independent oversight: Establish an independent review board to scrutinize the bot’s actions and ensure compliance with ethical guidelines. This board could include experts in cybersecurity, privacy, and legal affairs.
- Transparency and accountability: Provide clear and accessible information about the bot’s functionality and limitations. Establish clear lines of accountability for any misuse or unintended consequences.
Examples of Ethical Concerns in Similar Projects
The development of similar technologies in the past has encountered various ethical challenges. For instance, the use of facial recognition software has raised concerns about privacy and potential discrimination. Similarly, the deployment of automated surveillance systems has triggered debates about the balance between security and individual freedoms. These past examples underscore the importance of proactively addressing potential ethical issues during the development and implementation of the Phileas Project.
Ethical Principles and Guidelines for the Phileas Project, Phileas project uses bots to ferret out spyware
This table Artikels the key ethical principles and guidelines that will govern the Phileas Project.
| Ethical Principle | Specific Guideline |
|---|---|
| Data Minimization | Collect only the data necessary for spyware detection and analysis, and implement robust data anonymization techniques where appropriate. |
| Transparency | Clearly communicate the project’s goals, methods, and limitations to all stakeholders. |
| Accountability | Establish a system for tracking and addressing any instances of misuse or unintended consequences. |
| User Consent | Obtain explicit and informed consent from users before deploying the bot system on their systems. |
| Independent Review | Establish an independent review board to assess the ethical implications of the project and ensure compliance with established guidelines. |
Future Directions
The Phileas Project, in its current iteration, has demonstrated a strong foundation for detecting and mitigating spyware threats. Moving forward, the project needs to adapt to the ever-evolving landscape of malicious software and explore new avenues for enhanced effectiveness. This involves proactive research, strategic partnerships, and a commitment to staying ahead of emerging threats.
Potential Future Enhancements and Expansions
The Phileas Project’s efficacy hinges on its ability to continuously adapt and improve. Potential future enhancements include expanding the scope of monitored platforms to encompass emerging technologies like IoT devices and cloud-based applications. This broadened approach would reflect the growing attack surface in today’s digital ecosystem. Furthermore, enhancing the project’s machine learning algorithms to detect more sophisticated and obfuscated spyware techniques is critical.
This can be achieved by incorporating techniques such as anomaly detection and deep learning models.
New Approaches to Spyware Detection and Prevention
The methods for spyware detection are constantly evolving. One promising area for exploration is the development of behavioral-based detection models. These models would focus on identifying patterns of suspicious activity within a system, rather than simply looking for known signatures. A key element of this approach is the use of sandbox environments for analyzing unknown threats. This isolates the suspicious software from the user’s system and allows for a controlled environment to observe its behavior.
Another novel approach is to focus on the communication patterns of spyware. By analyzing the network traffic generated by the software, it’s possible to identify and block malicious communication channels before they can compromise the system.
Adaptation to Emerging Threats
The threat landscape is constantly changing. Emerging threats like polymorphic malware, which constantly changes its code to evade detection, pose a significant challenge. Developing techniques for dynamic analysis of these threats, along with continuous monitoring of open-source intelligence (OSINT) feeds to identify new attack vectors, is vital. Understanding how these emerging threats exploit vulnerabilities in operating systems and applications is paramount for proactive defense mechanisms.
Potential Areas for Collaboration and Partnerships
Collaboration with security researchers and industry experts can significantly accelerate the project’s progress. Partnering with cybersecurity firms can bring valuable expertise in threat analysis and incident response. Furthermore, collaborations with academic institutions can facilitate the development of cutting-edge detection techniques. Open-source community involvement could also be crucial for the continuous improvement of detection tools and algorithms. This collaborative environment would allow for the rapid sharing of knowledge and resources.
Potential Future Research Directions
| Research Direction | Potential Impact ||—|—|| Development of a unified threat intelligence platform | Enhanced threat detection and proactive response capabilities || Integration of blockchain technology for secure data management | Improved data integrity and traceability of actions, creating a secure and trustworthy platform || Exploring quantum-resistant cryptographic algorithms | Ensuring the longevity and security of the project’s algorithms against future quantum computing threats || Developing AI-driven automated response systems | Reduction in response time to malicious activities and improved efficiency of threat handling || Creation of a comprehensive knowledge base for threat actors and their tactics | Enabling faster identification of emerging attack patterns and improving the overall detection accuracy |
Summary
In conclusion, the Phileas Project’s innovative use of bots for spyware detection showcases a crucial step forward in cybersecurity. The project’s meticulous approach to bot deployment, spyware identification, and data analysis demonstrates a commitment to robust and proactive defense against evolving cyber threats. Future advancements and ethical considerations will be key to the project’s continued success in the ever-changing landscape of digital security.