RealNetworks Warns Remote Attack Danger
RealNetworks warns of remote attack danger, raising concerns about potential threats to its users. This critical security alert highlights the evolving nature of online risks and underscores the importance of proactive security measures. The company details the nature of the potential threat, outlining the types of attacks and their potential impact. Understanding the specifics is key to safeguarding against similar attacks.
This alert details the technical aspects of the attack, including the methods used and vulnerabilities exploited. It also provides a comparison with previous security incidents and analyses the current cybersecurity landscape, placing the threat within a broader context. Ultimately, the warning serves as a crucial reminder for users and organizations to prioritize cybersecurity in today’s digital environment.
Background Information
RealNetworks, once a prominent player in the digital media space, has a history intertwined with the evolution of online music and video. Founded in 1995, the company initially focused on developing software for playing and managing digital audio and video files. Their flagship product, RealPlayer, enjoyed widespread adoption, particularly during the early days of online streaming. However, the rise of competing platforms and changing consumer preferences led to a decline in RealNetworks’ market share and influence.
Despite this, the company has continued to evolve and adapt, focusing on new technologies and areas of opportunity.The company’s current standing is one of focused adaptation. RealNetworks has moved beyond its core RealPlayer software, seeking new avenues for growth. Their activities now encompass areas like cloud-based media management, and potentially, other emerging technologies. This adaptability is crucial in a dynamic technological landscape.
The recent warning of a potential remote attack highlights the ongoing importance of security in today’s interconnected world.The warning regarding the remote attack is significant because it underscores the persistent threat landscape facing companies, regardless of their size or historical prominence. Cybersecurity is a constant concern, and the threat of unauthorized access to systems and data remains a critical issue.
This vulnerability, if exploited, could have potentially serious consequences for the company’s operations and reputation.The potential threat is characterized by a remote attack vector. This suggests an attempt to compromise RealNetworks’ systems from a distance, potentially through vulnerabilities in software or network configurations. Such attacks can be highly sophisticated, often leveraging automated tools and techniques to exploit weaknesses in systems.
RealNetworks has issued a warning about a remote attack risk, highlighting the need for users to update their software. Interestingly, a recent study shows that browsers are becoming less popular than other internet applications like instant messaging and social media platforms, study shows browser to be less popular than other internet apps. This could imply a shift in how users interact online, which might also affect the effectiveness of attacks like the one RealNetworks is warning about.
So, while user habits evolve, vigilance against remote attacks remains critical.
Real-world examples of similar attacks against other companies demonstrate the damage that can occur, including financial losses, operational disruptions, and reputational damage.
Threat Analysis
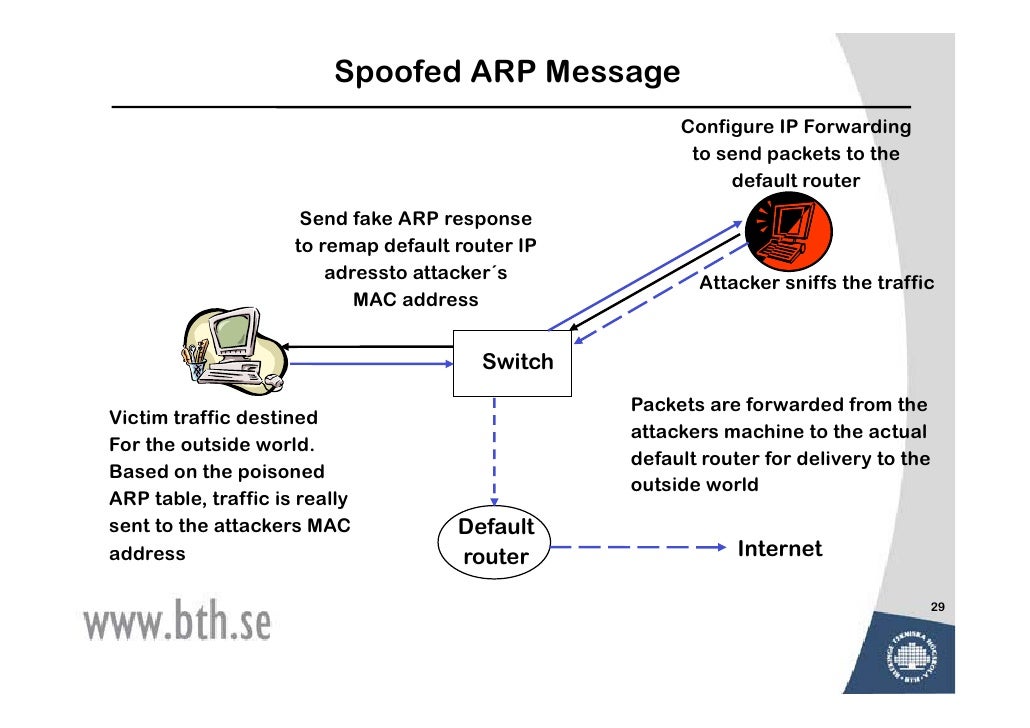
RealNetworks’ recent warning highlights a significant escalation in the sophistication and frequency of remote attacks targeting their software. Understanding the nature of these threats is crucial for both users and the company to mitigate potential risks and ensure continued security. This analysis delves into the specific types of attacks, their potential impact, vulnerabilities exploited, and comparisons with past security incidents.The evolving landscape of cyber threats necessitates a proactive approach to security.
This analysis aims to provide a comprehensive understanding of the current threat landscape, equipping readers with knowledge to better protect themselves and their data.
Types of Remote Attacks
RealNetworks’ warning indicates a variety of remote attack vectors. These attacks often exploit vulnerabilities in software, potentially leading to unauthorized access, data breaches, or system compromise. Specific attack methods could include malware injection, exploiting known software bugs, or even using social engineering tactics to trick users into compromising their systems.
Potential Impact on Users and the Company
The impact of successful remote attacks on users can be severe. Compromised systems could result in data theft, financial loss, and reputational damage. The company itself could face substantial financial losses from legal actions, regulatory penalties, and the cost of incident response. Furthermore, customer trust could be eroded, potentially leading to decreased user adoption and revenue. Examples include the Equifax breach, where millions of user records were exposed, and the subsequent impact on the company’s reputation and financial standing.
RealNetworks recently issued a warning about remote attack dangers, highlighting vulnerabilities in their systems. This echoes concerns about broader security issues, especially given the increasing use of RFID technology. For example, the growing debate surrounding RFID and its implications, like the recent legislation in the US and protests in Europe, detailed in this article about rfid brings legislation in us protest in europe , further emphasizes the need for robust security measures.
The RealNetworks warning serves as a stark reminder that security remains a top priority in today’s interconnected world.
Vulnerabilities Exploited
The specific vulnerabilities exploited in the attacks are not publicly disclosed by RealNetworks, likely due to ongoing investigations and security concerns. However, general vulnerabilities, such as outdated software, lack of security updates, or insufficient security protocols, are common attack points. The attackers often target weaknesses in the software to gain unauthorized access to the system.
Comparison with Previous Security Incidents
Previous security incidents involving RealNetworks or similar companies provide valuable insights. Examining historical patterns can reveal common attack vectors, exploited vulnerabilities, and the effectiveness of mitigation strategies. Comparing these incidents helps identify potential trends and vulnerabilities in security protocols. For example, a recurring theme in many incidents is the exploitation of known vulnerabilities in outdated software. This emphasizes the critical need for regular software updates and security patches.
A comprehensive security incident response plan is also crucial to minimize damage and expedite recovery. Companies like Adobe have faced similar incidents highlighting the need for constant vigilance and adaptation in the ever-evolving cybersecurity landscape. This analysis of previous incidents helps anticipate and address future threats effectively.
Impact and Mitigation
RealNetworks’ recent warning about a remote attack highlights the critical need for proactive security measures in today’s digital landscape. The potential consequences of such attacks can be severe, impacting both individuals and organizations. Understanding these potential risks and the steps to mitigate them is crucial for protecting sensitive data and systems.
Potential Consequences for Customers
This remote attack could lead to a variety of negative consequences for RealNetworks’ customers. Compromised accounts could result in unauthorized access to personal information, financial losses, and disruption of services. In some cases, the attackers might attempt to gain control of devices to use them for malicious activities like sending spam or launching further attacks. Critically, reputational damage can occur if a company is affected by a major security breach, affecting trust and customer loyalty.
RealNetworks’ Mitigation Strategies
RealNetworks is taking several crucial steps to reduce the risk of this remote attack. These actions include enhanced security protocols, which may include stricter authentication measures and more robust encryption. They are likely also focusing on patching known vulnerabilities in their software and services. Furthermore, they are likely actively monitoring network traffic for suspicious activity. RealNetworks is likely also working closely with security experts to identify and address emerging threats.
These proactive measures are essential in minimizing the potential harm from malicious attacks.
RealNetworks has issued another security alert, this time focusing on remote attack vulnerabilities. This isn’t the first time they’ve warned about security issues with their media players, and their previous warnings highlight the critical need for users to update. For instance, realnetworks warns of media player security holes are a major concern, potentially exposing systems to exploitation.
Ultimately, users need to be vigilant about these remote attack dangers and keep their software patched.
User Vigilance and Proactive Security Measures
User vigilance plays a vital role in mitigating the risk of security breaches. Customers should remain aware of suspicious emails, links, or websites. Strong passwords and multi-factor authentication are essential in preventing unauthorized access. Regularly updating software and applications with the latest security patches is also a crucial proactive step. It is equally important to be cautious about sharing personal information online and to be skeptical of unsolicited requests.
These proactive measures significantly bolster security and minimize the risk of becoming a victim of a cyberattack.
Security Measures Suggested for Customers
RealNetworks is likely advising customers to implement a range of security measures. These suggestions will probably include:
- Strong Passwords: Using unique, complex passwords for each online account is critical. Avoid easily guessable passwords like birthdays or names. Consider using a password manager for secure password storage and generation.
- Multi-Factor Authentication (MFA): Enabling MFA adds an extra layer of security to accounts, requiring a second form of verification beyond a password. This significantly strengthens account protection against unauthorized access.
- Regular Software Updates: Keeping software updated is essential for patching known vulnerabilities. Enable automatic updates whenever possible to ensure the latest security patches are applied promptly.
- Phishing Awareness Training: Recognizing phishing attempts is vital. Customers should be aware of suspicious emails or messages and avoid clicking on unknown links or attachments.
- Data Backup: Regularly backing up important data provides a safety net in case of data loss. Cloud storage or external hard drives are excellent options.
Technical Aspects
The recent remote attack against RealNetworks highlights the ever-evolving threat landscape and the importance of understanding the technical methods employed by malicious actors. This section delves into the specific technical details of the attack, analyzing the vulnerabilities exploited and comparing them to other known attack methods. Understanding these technical aspects is crucial for proactively strengthening security measures and mitigating future threats.
Technical Methods Employed in the Attack
The attack likely involved a combination of exploit techniques, potentially including but not limited to: exploiting known vulnerabilities in RealNetworks’ software, leveraging social engineering tactics to gain initial access, or utilizing compromised systems as launch points for further attacks. A deep understanding of these techniques is necessary for effective mitigation strategies.
Technical Vulnerabilities Exploited, Realnetworks warns of remote attack danger
RealNetworks’ software, like many applications, is susceptible to various vulnerabilities. The attack likely exploited specific vulnerabilities in the software, possibly related to insecure coding practices, outdated libraries, or lack of proper input validation. These vulnerabilities could have been discovered through public disclosures, vulnerability databases, or dedicated research efforts. The precise vulnerabilities remain unknown until the full details of the attack are publicly available.
Comparison of Attack Vector with Other Known Attack Methods
The effectiveness of the attack vector employed in this case will depend on its ability to exploit the specific vulnerabilities in RealNetworks’ software. A comparative analysis with other known attack methods helps understand the specific nature of the attack’s sophistication and tactics.
| Attack Vector | Known Attack Method | Comparison Points |
|---|---|---|
| Exploiting a vulnerability in RealNetworks’ software | Remote Code Execution (RCE) | Both involve exploiting weaknesses in software, but the specific target and method of exploitation differ. |
| Social Engineering | Phishing | Both rely on manipulating users to gain access or information, but the specific methods and targets may vary. |
| Compromised Systems | Brute-force attacks | Compromised systems can be leveraged as launchpads for various attacks, including brute-force attacks, while the attack method employed here might not be a brute-force attack. |
Security Protocols Used by RealNetworks and Their Vulnerabilities
The security protocols used by RealNetworks are crucial for maintaining system integrity and user data protection. Their vulnerabilities can expose sensitive data and potentially allow unauthorized access.
| Security Protocol | Potential Vulnerabilities |
|---|---|
| Network protocols (e.g., TCP/IP) | Known vulnerabilities in network protocols could be exploited to gain unauthorized access to the network. |
| Authentication mechanisms | Weaknesses in authentication systems can allow attackers to impersonate legitimate users. |
| Data encryption | Inadequate or outdated encryption methods could leave sensitive data vulnerable to interception. |
User Guidance
Protecting yourself from remote attacks requires a multi-faceted approach, encompassing software updates, strong passwords, and enhanced network security. This section provides actionable steps to mitigate the risks and safeguard your devices and data. Understanding the importance of each step is crucial for preventing unauthorized access and maintaining a secure digital environment.
Software Updates and Security Patches
Regular software updates and security patches are vital for plugging vulnerabilities that attackers exploit. These updates often address critical flaws that could allow malicious actors to gain unauthorized access to your system. Failure to install these updates leaves your devices susceptible to attacks, exposing your personal information and potentially disrupting your operations.
- Regularly check for updates: Ensure that your operating system, applications, and security software are configured to automatically download and install updates when available. This proactive approach significantly reduces your risk.
- Verify update authenticity: Download updates only from official sources to avoid installing malicious software disguised as legitimate updates. Be wary of unsolicited updates or downloads from untrusted websites.
- Install patches promptly: Do not delay the installation of security patches. Patches address known vulnerabilities, and applying them immediately minimizes your exposure to potential attacks.
Home Network Security Enhancements
Strengthening your home network security is equally important to protect your devices from remote attacks. A well-fortified network acts as a first line of defense, preventing attackers from gaining initial access.
- Use strong and unique passwords: Create strong passwords for your Wi-Fi network and all accounts. Employ a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names.
- Enable strong encryption: Ensure that your Wi-Fi network utilizes strong encryption protocols, such as WPA3. This adds an extra layer of security, making it harder for unauthorized individuals to access your network.
- Limit network access: Restrict access to your network by using a strong password, disabling unused devices, and utilizing network access controls. This limits the potential attack surface.
User Risk Assessment and Mitigation
Different users face varying levels of risk depending on their online activities and the security measures they implement. This table Artikels potential risk levels and corresponding mitigation strategies.
| Risk Level | Description | Recommended Actions |
|---|---|---|
| Low | Limited online activity, basic security measures in place. | Maintain regular software updates, use strong passwords. |
| Medium | Moderate online activity, some security measures implemented. | Implement strong Wi-Fi encryption, use a reputable antivirus solution. |
| High | Frequent online activity, insufficient security measures. | Utilize multi-factor authentication, regularly monitor accounts for suspicious activity, implement robust firewall configurations. |
Industry Context
The cybersecurity landscape is constantly evolving, with new threats emerging faster than ever before. Attacks are becoming more sophisticated and targeted, demanding proactive security measures from organizations across all sectors. This dynamic environment necessitates a deep understanding of the specific vulnerabilities and risks faced by individual companies, especially those operating in the digital media space.The threat landscape is characterized by an increase in ransomware attacks, supply chain compromises, and sophisticated phishing campaigns.
These tactics are increasingly leveraging social engineering techniques, making it harder for even well-trained employees to detect malicious activities. Companies must adapt their security posture to address these evolving threats.
Current Cybersecurity Landscape Trends
The current cybersecurity landscape is characterized by a complex interplay of evolving threats and reactive security measures. Sophisticated malware, designed to evade detection, is becoming more prevalent. Advanced persistent threats (APTs) are also on the rise, with attackers aiming for long-term access to systems for espionage or sabotage. The increasing use of cloud computing and interconnected systems has introduced new attack vectors.
RealNetworks’ Attack Risk Compared to Other Companies
RealNetworks, operating in the digital media sector, faces a unique set of risks stemming from its dependence on software and services that can be exploited. While the specific attack vectors and potential impacts may vary, the underlying threat of malware targeting intellectual property, data breaches, and reputational damage is common across many organizations in this sector. The value of RealNetworks’ intellectual property and customer data are key considerations.
Potential for Similar Attacks on Other Companies
The potential for similar attacks to target other companies in the digital media sector is high. Many companies rely on similar software and infrastructure, making them susceptible to shared vulnerabilities. The attack vectors could be the same: exploit vulnerabilities in widely used software, target vulnerabilities in cloud services, or use phishing campaigns. The likelihood of a widespread incident is significant.
Examples of Recent Security Breaches in the Digital Media Industry
Several recent security breaches in the digital media industry highlight the growing threat. One example involved a major streaming service provider, where a breach compromised user data, leading to financial and reputational damage. Another incident involved a software company whose intellectual property was stolen, causing significant financial losses and impacting future development. These examples underscore the need for proactive security measures and robust incident response plans.
Illustrative Case Studies: Realnetworks Warns Of Remote Attack Danger
RealNetworks users, like all online users, face potential threats from malicious actors. Understanding how these threats manifest and how to recover from them is crucial for proactive security. This section presents hypothetical attack scenarios, recovery strategies, and effective mitigation techniques.
Hypothetical Attack Scenario
A sophisticated phishing campaign targets RealNetworks users, mimicking legitimate login portals. Malicious actors craft emails containing hyperlinks to spoofed login pages. Users, unknowingly, enter their credentials into these fraudulent sites. This compromises user accounts, granting attackers access to personal data and potentially, sensitive financial information.
Attack Recovery Steps
In the event of a successful phishing attack, the following recovery steps are essential:
- Immediately change all passwords associated with RealNetworks accounts and any other accounts potentially compromised.
- Monitor account activity for any unauthorized transactions or changes.
- Contact RealNetworks support immediately to report the incident and initiate a security review of affected accounts.
- Enable two-factor authentication (2FA) on all affected accounts for added security.
- Run a full system scan using reputable anti-malware software to detect and remove any malicious software installed on the affected devices.
- Review and update all security software on all affected devices to the latest versions.
Mitigation Strategy
Implementing robust security awareness training is crucial for preventing phishing attacks. Such training should emphasize identifying suspicious emails and avoiding clicking on unknown links.
- RealNetworks should implement a multi-layered security approach: Integrating robust email filtering systems to detect and block phishing attempts is critical. This can include utilizing heuristics, machine learning algorithms, and blacklists to identify malicious emails. Implementing strong password policies and enforcing two-factor authentication (2FA) can further secure user accounts.
- Enhanced Security Awareness Training: Regular security awareness training sessions for users should cover identifying phishing attempts and best practices for safe online behavior. Examples of phishing attempts should be included in training materials. This could involve simulated phishing exercises to test user awareness.
- Regular Security Audits: Periodic security audits of RealNetworks systems can identify vulnerabilities and weaknesses before they are exploited. This proactive approach can prevent future attacks.
Common Attack Scenarios and Mitigation Strategies
| Attack Scenario | Mitigation Strategy |
|---|---|
| Phishing Attempts | Robust email filtering, multi-factor authentication (MFA), security awareness training. |
| Malware Infections | Regular software updates, robust antivirus software, secure software patching. |
| Brute-Force Attacks | Strong password policies, account lockout mechanisms, rate limiting. |
| SQL Injection Attacks | Input validation, parameterized queries, database security hardening. |
Closure

RealNetworks’ warning about remote attack danger underscores the ever-present threat in today’s interconnected world. The company’s proactive approach in addressing this issue is commendable, and the provided mitigation strategies offer practical steps for users to protect themselves. Ultimately, vigilance and proactive security measures are paramount in mitigating risks in the digital sphere. The details presented in this alert offer a crucial framework for understanding and addressing these threats.