VeriSigns Controversial Service Report Due Soon
Report on controversial VeriSign service expected in two weeks sets the stage for a deep dive into the potential implications of this new service. We’ll explore VeriSign’s offerings, highlighting both the promised benefits and the potential pitfalls. This report promises to be a comprehensive look at the controversy surrounding this upcoming service, including stakeholder perspectives and potential solutions.
VeriSign’s new service, slated for launch in two weeks, is already generating buzz and debate. Early indications suggest a complex interplay of potential benefits and risks. This report will analyze the service’s intended functionality, target audience, and the broader market context. A critical examination of the controversial aspects will also be presented, along with an evaluation of the potential impacts on various stakeholders.
Furthermore, the report will discuss potential mitigation strategies and alternative approaches, fostering a nuanced understanding of this anticipated market disruption.
Overview of VeriSign Service
VeriSign, a global leader in internet infrastructure, is poised to launch a new service expected to significantly impact online security and trust in the coming weeks. This service, while still shrouded in some secrecy, promises to enhance the verification and validation of digital identities and certificates, strengthening the overall security posture of the internet ecosystem. Its arrival comes at a crucial time, as the rise of sophisticated cyber threats and evolving online fraud necessitates robust security measures.This service is designed to address vulnerabilities in existing authentication systems, providing a more resilient and reliable approach to digital identification.
The anticipated functionality will encompass enhanced verification protocols, enabling more accurate and comprehensive identification of online entities. This will, in turn, bolster confidence in online transactions and interactions, reducing the risk of fraud and impersonation.
Service Functionality
The service is anticipated to employ advanced cryptographic techniques and blockchain-based validation mechanisms. This sophisticated approach will ensure the integrity and authenticity of digital certificates and identities, enhancing the security posture of online platforms and services. It will potentially streamline the verification process for businesses and individuals, allowing for faster and more secure interactions online. The expected outcomes include reduced fraud rates, improved user trust, and a more secure digital environment.
The VeriSign report, due in two weeks, promises to be pretty controversial. It’s fascinating to see how touch technology is changing the online landscape; check out this insightful piece on touch technology comes of age online. But ultimately, the VeriSign report will be crucial in shaping our understanding of how this technology impacts security and user experience.
Hopefully, it will provide some clarity.
Target Audience
The primary target audience for this service encompasses a broad spectrum of stakeholders, including:
- E-commerce businesses:
- Online service providers:
- Government agencies and institutions:
- Individuals:
E-commerce platforms will benefit from enhanced security, reducing the risk of fraudulent transactions and bolstering customer trust. Examples include online retailers, marketplaces, and payment gateways.
This service will improve the security of online services such as social media platforms, cloud storage providers, and online banking portals. This leads to increased user confidence and reduced security breaches.
Enhanced digital identity verification will facilitate secure online transactions and communication for governmental services, such as tax filing and citizen services.
Individuals will benefit from increased security in online transactions and interactions, such as online banking, e-commerce, and social media.
Market Landscape
The current market landscape is characterized by a growing prevalence of cyber threats and a corresponding need for robust security solutions. The increasing sophistication of cyberattacks necessitates a shift towards more advanced verification and authentication methods. The rise of digital identities and decentralized systems demands secure validation mechanisms, providing trust and security in the digital realm. This trend is driven by the ever-expanding online economy and the increasing reliance on digital services.
Competitive Analysis
| Feature | VeriSign Service | Competitor A | Competitor B |
|---|---|---|---|
| Verification Method | Advanced cryptographic techniques, blockchain-based validation | Traditional certificate authority methods | Decentralized identity solutions |
| Security Level | Enhanced security, reducing fraud | Moderate security | High security, but less widespread adoption |
| Scalability | Scalable architecture to handle high volume | Limited scalability | Potentially scalable, but with implementation challenges |
| Cost | Cost-effective solution for increased security | Variable costs | High initial costs, potential for reduced long-term costs |
This table compares VeriSign’s anticipated service to prominent competitors, highlighting key differences in verification methods, security levels, scalability, and potential costs.
Controversial Aspects of the Service: Report On Controversial Verisign Service Expected In Two Weeks
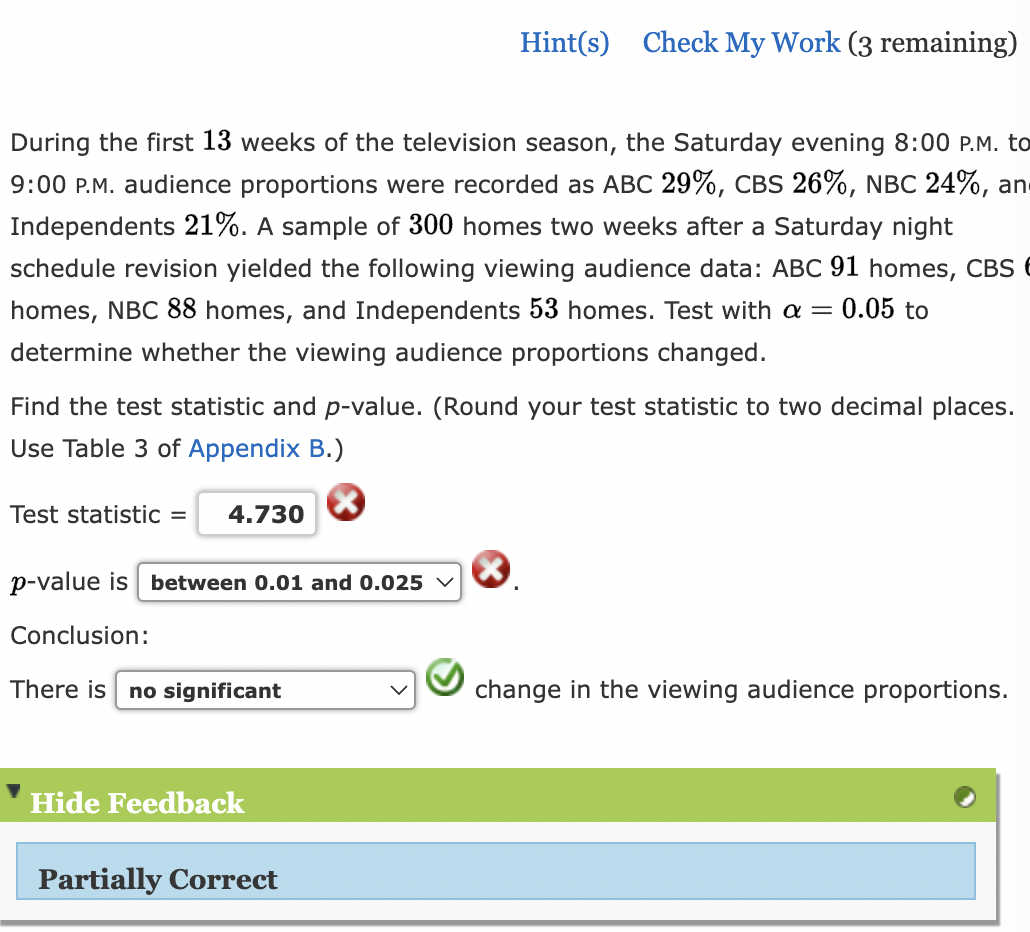
The impending VeriSign service, slated for rollout in two weeks, is already generating significant debate. Concerns range from potential user privacy violations to broader implications for the digital economy. This analysis delves into the controversial aspects, examining potential pitfalls and contrasting them with potential benefits.The new service promises enhanced security and efficiency, but the devil is in the details.
Critics are raising alarms about the potential for misuse and unintended consequences. The scrutiny reflects the delicate balance between technological advancement and societal well-being.
Potential Privacy Concerns
The VeriSign service’s reliance on extensive data collection has raised concerns about user privacy. Users may feel uncomfortable with the potential for their personal information to be used for purposes beyond the stated service functionality. This includes the possibility of data breaches and unauthorized access, potentially exposing sensitive data. The service’s transparency regarding data usage and security protocols is crucial in mitigating these concerns.
Examples of past data breaches highlight the critical importance of robust security measures.
Implications for Businesses
The service’s implementation will significantly impact businesses reliant on digital platforms. Businesses that use the service must carefully consider the financial implications of compliance and adaptation. Potential increases in operational costs and the necessity of retraining staff are important considerations. The service could also influence business strategies and competitive landscapes. Consider the ripple effect of adopting a new technology on supply chains and industry norms.
Ethical Considerations
The ethical implications of the VeriSign service extend beyond privacy concerns. Questions regarding equitable access and potential biases in the service’s algorithms are emerging. These concerns highlight the importance of ethical guidelines and regulatory oversight in ensuring fair implementation. Past instances of discriminatory practices in similar technologies demonstrate the need for proactive measures to prevent such issues.
Benefits Versus Risks
Weighing the potential benefits of enhanced security and efficiency against the potential risks is crucial. The service’s promise of improved security must be balanced against the potential for misuse and data breaches. The service’s value proposition should be clearly articulated and supported by concrete evidence. A careful risk assessment is essential to mitigate potential negative impacts on users and the industry.
Examples of services with initially promising features but ultimately flawed implementation serve as cautionary tales.
Speaking of tech news, a report on the controversial VeriSign service is expected in two weeks. Meanwhile, Samsung is making waves with their latest innovation, unveiling the fastest mobile CPU on the market, samsung unveils fastest mobile cpu on the market. This incredible advancement, however, doesn’t overshadow the anticipated VeriSign report, which promises to be quite interesting.
Comparison with Past Controversies
Several past controversies surrounding similar services offer valuable lessons. The history of online advertising, for instance, is replete with examples of user privacy violations and concerns about data misuse. The emergence of social media platforms has also generated controversies surrounding user data collection and manipulation. These examples highlight the importance of proactive measures and robust ethical frameworks to prevent similar issues from arising with the new VeriSign service.
Expected Impact and Implications
VeriSign’s upcoming service, while promising efficiency gains, faces significant uncertainty regarding market adoption and potential repercussions. Its controversial nature suggests a complex interplay of benefits and drawbacks that need careful consideration, particularly regarding user experience, security, and potential legal challenges. This section delves into the potential short-term and long-term impacts, exploring various scenarios and the possible regulatory landscape.The service’s rollout will undoubtedly create ripples across the digital landscape.
Understanding the potential for widespread adoption, resistance, and the service’s influence on user behavior and security protocols is crucial for stakeholders and the public. The service’s impact on existing infrastructure and the emergence of potential new security vulnerabilities will be closely monitored.
Short-Term Market Effects
The initial period following the service’s launch will likely see a mix of cautious optimism and apprehension. Early adopters, driven by the promise of enhanced efficiency, will likely embrace the new system, while others will remain hesitant, waiting to assess the practical implications. This initial phase will be characterized by significant adjustments in existing workflows and potentially some initial glitches.
A crucial factor in short-term adoption will be the ease of integration with existing systems. The market response will depend heavily on the service’s reliability and the effectiveness of its support mechanisms.
Long-Term Market Impacts
Long-term effects will be profoundly shaped by the service’s adoption rate. If widely embraced, it could lead to significant improvements in industry efficiency and a restructuring of the digital infrastructure. However, widespread resistance could stagnate innovation and potentially create new security vulnerabilities if not adequately addressed. The service’s ability to adapt to evolving user needs and security threats will play a pivotal role in its long-term success.
Examples of similar disruptive technologies, like the shift to cloud computing, offer lessons on the long-term adaptability and integration challenges.
Adoption and Resistance Scenarios
Several scenarios regarding adoption and resistance can be envisioned. One possibility is a rapid and widespread adoption driven by demonstrable efficiency gains and user-friendly implementation. Conversely, significant resistance could emerge if the service faces integration challenges or raises serious security concerns. This could lead to a protracted period of testing and refinement before gaining wider acceptance. The service’s ability to address user concerns and provide adequate support mechanisms will be paramount in shaping its adoption curve.
Impact on User Experience and Security
The service’s impact on user experience will depend heavily on its design and implementation. A user-friendly interface and seamless integration with existing platforms are critical for a positive user experience. Conversely, a complex or poorly designed system could significantly hamper user satisfaction. Regarding security, the service’s potential vulnerabilities must be thoroughly assessed. Implementing robust security measures and transparent security protocols will be essential to avoid any compromises.
The service’s vulnerability to potential attacks will determine its long-term impact on user trust and security practices.
Regulatory and Legal Challenges
Potential regulatory challenges stem from the service’s potential impact on existing legal frameworks, particularly concerning data privacy and security. Compliance with regulations like GDPR or CCPA will be crucial. Legal challenges could arise if the service is deemed to violate existing intellectual property laws or if it introduces new privacy concerns. The need for regulatory clarity and preemptive measures to address potential issues will be critical.
Potential Outcomes Table
| Potential Outcome | Positive Impact | Negative Impact |
|---|---|---|
| Widespread Adoption | Increased efficiency, innovation, and market growth. | Potential for increased competition and market disruption. |
| Limited Adoption | Mitigation of potential risks associated with widespread implementation. | Reduced market growth and potential stagnation in innovation. |
| Regulatory Challenges | Ensuring user safety and compliance with legal frameworks. | Delays in implementation and potential legal battles. |
Stakeholder Perspectives
The upcoming VeriSign service promises significant changes, but its potential impact will vary drastically across different stakeholder groups. Understanding these varied perspectives is crucial for assessing the service’s overall viability and long-term consequences. This section delves into the anticipated reactions of consumers, businesses, investors, and regulators, highlighting potential conflicts and areas of agreement.Different stakeholders will inevitably perceive the VeriSign service through distinct lenses, influenced by their individual needs and priorities.
A thorough analysis of these perspectives is necessary to predict the service’s trajectory and address potential challenges effectively.
Consumer Perspectives
Consumers will likely be most concerned with the service’s cost and ease of use. If the service significantly increases the cost of online transactions or requires complex procedures, adoption could be slow. On the other hand, enhanced security features could attract consumers who prioritize online safety.
- Cost Implications: Consumers may perceive the service as adding an extra layer of cost to online transactions, potentially impacting their budgets. For example, if the service involves mandatory fees or subscription costs, it could deter users, particularly those with limited budgets or low transaction volumes. A gradual increase in fees, in line with the increased security measures, could lead to more acceptance.
While we await the report on VeriSign’s controversial service, expected in two weeks, it’s interesting to note that Orange has announced a new Microsoft-based smartphone, the SPV E200. Orange announces new microsoft based spv e200 smartphone This new device, however, doesn’t necessarily change the core issue of the VeriSign report, which will undoubtedly delve into the service’s potential impact on internet security.
- User Experience: A seamless and intuitive user experience is crucial. If the service adds significant complexity or requires extensive technical knowledge, consumer adoption could be hindered. User-friendly interfaces and simplified processes are essential for widespread adoption.
- Security Benefits: Enhanced security is likely to attract consumers who value online safety and security. Clear communication about the added security features and their tangible benefits will be crucial for fostering consumer confidence and acceptance.
Business Perspectives
Businesses will likely be concerned with the service’s impact on their operations, pricing models, and competitive landscape. Adoption will depend on how well the service integrates with their existing infrastructure and whether it offers tangible benefits in terms of cost savings or revenue generation.
- Operational Integration: Businesses will need to assess how the service aligns with their existing IT infrastructure and processes. Successful implementation will depend on the service’s flexibility and adaptability. Compatibility issues could delay or prevent adoption, potentially leading to significant disruptions in operations.
- Pricing Models: Businesses will scrutinize the pricing models for the service, considering the cost-benefit analysis and how it might affect their bottom line. Flexible pricing tiers that cater to different business sizes and transaction volumes could improve adoption rates.
- Competitive Advantage: The service could provide a competitive edge for businesses that adopt it quickly and effectively. This is especially true if it strengthens security measures or offers a significant improvement in operational efficiency.
Investor Perspectives
Investors will likely assess the service’s potential return on investment, its market size, and the overall market demand. Positive market response and strong financial projections will be crucial for attracting investment and ensuring long-term viability.
- Market Analysis: Investors will closely examine market trends and forecasts for the service, analyzing factors like market size, potential growth, and competitive landscape. Strong market analysis reports are critical for attracting investment capital.
- Financial Projections: Realistic and well-supported financial projections are crucial for attracting investment. Investors will evaluate the service’s potential for profitability and sustainability.
- Regulatory Landscape: The regulatory environment plays a crucial role in shaping investor sentiment. Clear and consistent regulatory frameworks are essential for fostering confidence in the service and attracting investment.
Regulatory Perspectives
Regulators will likely focus on the service’s potential impact on consumer protection, competition, and national security. Compliance with existing regulations and demonstrable benefits to consumers will be paramount.
- Compliance with Regulations: Regulators will scrutinize the service for compliance with existing regulations regarding consumer protection, data privacy, and security. Clear demonstration of compliance with these regulations is essential for gaining regulatory approval.
- Market Impact: Regulators will analyze the potential impact of the service on the market, considering aspects like competition, pricing, and consumer choice. Potential anti-competitive practices need to be carefully evaluated and avoided.
- National Security Implications: Regulators will assess the potential implications for national security and ensure that the service does not pose any risks. Security measures to protect against cyber threats and data breaches will be a key focus.
Stakeholder Reaction Table
| Stakeholder Group | Potential Reaction |
|---|---|
| Consumers | Positive if cost-effective and secure; negative if expensive or complex. |
| Businesses | Positive if integrated seamlessly and improves efficiency; negative if it creates operational challenges or increases costs. |
| Investors | Positive if strong financial projections and market demand; negative if poor financial outlook or regulatory concerns. |
| Regulators | Positive if complies with regulations and enhances consumer protection; negative if it creates market distortions or national security concerns. |
Potential Solutions and Mitigation Strategies
The upcoming VeriSign service, while promising potential benefits, faces considerable controversy. Addressing these concerns requires proactive solutions and mitigation strategies to ensure a smooth rollout and minimize negative impacts. This section explores various approaches, ranging from refining the service itself to fostering open communication with stakeholders.
Addressing Security Concerns
The service’s security implications are a primary concern. Robust security measures are paramount to preventing data breaches and misuse. Implementing multi-factor authentication, rigorous encryption protocols, and regular security audits are crucial steps. Furthermore, independent security assessments by reputable third-party organizations can build trust and demonstrate the service’s commitment to security. Transparency in security protocols and procedures will also alleviate stakeholder anxieties.
Improving Transparency and Accountability
Lack of transparency surrounding the service’s design and implementation has fueled skepticism. Clearer communication about the service’s functionalities, data handling practices, and potential risks is essential. Establishing an independent oversight board composed of technical experts and legal professionals can further enhance accountability. This board could review the service’s operations and provide recommendations for improvement. Publicly accessible documentation outlining the service’s architecture, algorithms, and data flow will also help foster trust and understanding.
Developing Alternative Approaches
Exploring alternative approaches is vital to finding solutions that better address concerns. Open discussions with stakeholders can reveal innovative solutions. Alternative approaches might involve decentralized models, federated systems, or open-source implementations, which can enhance security and transparency. This approach might also reduce the reliance on a single entity, distributing the risk. For example, consider using a distributed ledger technology (DLT) to enhance the security and transparency of the service.
Public Communication and Engagement Plan
A proactive communication plan is critical for managing stakeholder expectations and addressing concerns. Regular updates, Q&A sessions, and town hall meetings can foster dialogue. Utilizing various communication channels, including social media, webinars, and online forums, can broaden the reach and engagement. A dedicated webpage with FAQs, technical details, and contact information will facilitate access to information. The plan should also include mechanisms for receiving and addressing feedback.
Summary of Potential Solutions, Report on controversial verisign service expected in two weeks
| Potential Solution | Benefits | Drawbacks |
|---|---|---|
| Implementing Multi-Factor Authentication and Enhanced Encryption | Increased security, reduced risk of unauthorized access | Potential complexity in implementation, increased cost for users |
| Establishing an Independent Oversight Board | Enhanced accountability, increased transparency | Potential delays in implementation, additional administrative overhead |
| Exploring Decentralized/Federated Models | Reduced reliance on a single entity, enhanced security and resilience | Potential complexity in development, compatibility issues with existing systems |
| Comprehensive Public Communication Plan | Improved stakeholder understanding, reduced misinformation | Requires significant resources and time commitment |
Illustrative Examples

The VeriSign service, poised to launch in two weeks, is sure to generate significant discussion. Understanding the potential controversies surrounding such a service requires examining past examples of similar technologies that have encountered similar challenges. Analyzing these precedents can offer valuable insights into potential pitfalls and effective mitigation strategies.
Historical Parallels in Controversial Services
Numerous services throughout history have faced significant controversy due to their impact on various stakeholders. These controversies often stem from concerns about privacy, security, fairness, and economic implications. Examining these historical parallels provides valuable context for understanding the potential challenges associated with the VeriSign service.
Examples of Similar Controversial Services
Several services, while differing in specifics, have encountered public backlash and regulatory scrutiny. These examples illustrate the potential for unintended consequences and the importance of careful consideration of potential impacts.
- The Rise of Social Media Platforms: Platforms like Facebook and Twitter have faced widespread criticism for issues like data privacy, misinformation, and the spread of harmful content. The ability of these platforms to influence public opinion and manipulate information has generated considerable debate. Concerns about user data collection, algorithm biases, and the potential for censorship have been central to the controversies.
- The Development of Advanced Surveillance Technologies: The increasing use of surveillance technologies, including facial recognition systems and advanced data analytics, has sparked concerns about privacy violations and potential abuses of power. The potential for misuse of such technologies and the lack of transparency in their operation have raised serious ethical concerns.
- The Adoption of Cryptocurrencies: The rapid rise of cryptocurrencies has brought with it a host of controversies, including concerns about volatility, security risks, and environmental impact. The decentralized nature of cryptocurrencies and the lack of regulation have led to concerns about fraud, money laundering, and the potential for misuse by malicious actors.
Factors Contributing to Controversies
Several factors contribute to the controversies surrounding these services. These factors frequently include issues of power imbalances, lack of transparency, and inadequate regulatory frameworks.
- Lack of Transparency and Control: Many of the controversial services mentioned above suffer from a lack of transparency regarding their algorithms, data collection practices, and decision-making processes. This lack of transparency fosters distrust and suspicion among users and stakeholders.
- Potential for Abuse: The inherent potential for abuse plays a significant role in the controversy surrounding many services. For example, the ability of social media platforms to manipulate information and influence public opinion raises concerns about potential abuse of power.
- Inadequate Regulatory Framework: The absence of adequate regulatory frameworks to oversee the development and deployment of these services exacerbates the potential for misuse and harm. This lack of regulation often leaves vulnerable users and stakeholders unprotected.
Outcomes and Lessons Learned
Analyzing the outcomes of past controversies provides valuable lessons for navigating future challenges. These outcomes demonstrate the importance of proactive stakeholder engagement, transparency, and ethical considerations.
- Increased Public Scrutiny: Controversies often lead to increased public scrutiny and demands for accountability. Companies must be prepared to address concerns and demonstrate their commitment to ethical practices.
- Regulatory Reforms: Past controversies have often spurred regulatory reforms to address specific issues. This demonstrates the need for adaptable and responsive regulatory frameworks.
- Enhanced Transparency: A heightened emphasis on transparency and accountability has emerged as a key lesson learned from past controversies. This includes improved communication with stakeholders and increased public disclosure of relevant information.
Historical Precedent and Comparisons
Examining historical precedents and comparisons to past services can provide valuable context for understanding the potential implications of the VeriSign service. The parallels between the service and past services can reveal commonalities and potential pitfalls.
Summary Table
| Service | Controversial Aspects | Factors Contributing | Outcomes |
|---|---|---|---|
| Social Media Platforms | Data privacy, misinformation, censorship | Lack of transparency, power imbalance | Increased public scrutiny, regulatory reforms |
| Advanced Surveillance Technologies | Privacy violations, potential abuse | Lack of transparency, potential for misuse | Public awareness campaigns, ethical guidelines |
| Cryptocurrencies | Volatility, security risks, environmental impact | Decentralized nature, lack of regulation | Increased regulatory scrutiny, enhanced security protocols |
Final Wrap-Up
In conclusion, the upcoming VeriSign service promises a fascinating case study in technological innovation and its societal impact. The report, due in two weeks, will analyze this service from multiple angles, offering insights into potential benefits and drawbacks. This comprehensive analysis will equip readers with the necessary information to form their own opinions and engage in thoughtful discussion surrounding this significant development in the industry.
The service’s future will depend heavily on how the concerns and criticisms are addressed. The coming weeks will be critical in shaping the service’s success and its role in the future of online security.






