Report Shows Uptick in Automated Phishing
Report shows uptick in automated phishing, revealing a concerning trend in cybercrime. This sophisticated form of attack uses scripts and programs to send out massive waves of phishing emails, often personalized to target specific individuals. This contrasts with traditional phishing, which relies on more manual methods. The increased volume and potential for personalization in automated phishing campaigns pose a significant risk to businesses and individuals alike, demanding proactive measures for defense.
The report delves into the characteristics that differentiate automated phishing from traditional methods, examining the scale, customization, and techniques used in these attacks. It also explores the potential impact on various sectors, from finance to healthcare, outlining potential economic losses and reputational damage. Further, the report analyzes the technical aspects of automated phishing, including the tools, platforms, and social engineering tactics employed by attackers.
Finally, the report provides practical strategies for detection and prevention, emphasizing the importance of user awareness and robust security measures.
Defining the Uptick
Automated phishing, a sophisticated form of social engineering, is on the rise. This method leverages scripts and programs to automate the process of sending malicious emails and messages, significantly amplifying the reach and impact of phishing attacks. Unlike traditional phishing, which relies on manual effort, automated phishing allows attackers to target a massive number of victims with tailored messages, making it a significant threat to individuals and organizations alike.Automated phishing differs from traditional phishing methods in its scale and efficiency.
Traditional phishing campaigns rely on manual crafting of emails, limiting the number of recipients that can be targeted and making personalization challenging. Automated phishing, in contrast, utilizes scripts and programs to generate and send emails at scale, enabling attackers to reach a much wider audience with messages that may appear personalized, even if not fully tailored. This automated nature enables attackers to quickly adapt to evolving security measures, making detection and mitigation more difficult.
Automated Phishing vs. Traditional Phishing
Traditional phishing methods typically involve manually crafting emails and messages to trick recipients into revealing sensitive information. These messages may include false claims, threats, or a sense of urgency. In contrast, automated phishing leverages scripts and programs to automate the entire process. This includes composing messages, sending them to large numbers of recipients, and potentially tracking responses.
This automated approach allows for greater volume, customization (to an extent), and potentially faster response times than traditional methods.
Characteristics of Automated Phishing
Automated phishing campaigns often share distinct characteristics that distinguish them from their traditional counterparts. Firstly, automation is the key differentiator. Attackers leverage scripts and programs to execute the entire phishing process, significantly increasing the volume and speed of attacks. Secondly, these attacks frequently exhibit a higher degree of personalization. While not always perfectly customized, automated phishing can use data collected from previous targets to tailor the messages to a degree, increasing their effectiveness.
Finally, automated phishing is often harder to detect because of its high volume. Security measures designed to catch spam and phishing attempts often struggle to keep up with the sheer volume of automated messages.
Examples of Automated Phishing Attacks
Automated phishing attacks can manifest in various forms, including:
- Mass-scale credential-phishing attacks: Attackers use automated scripts to send out emails or messages containing fake login pages designed to steal user credentials.
- Automated malware distribution: Malicious code is automatically attached to emails, spreading viruses and ransomware to infected devices.
- Phishing attacks based on publicly available data: Attackers collect data from various sources (e.g., social media, company websites) to create more targeted and personalized phishing messages.
- Automated spear-phishing campaigns: Scripts are utilized to target specific individuals or organizations with highly tailored phishing messages.
These examples highlight the diverse and evolving nature of automated phishing attacks.
Phishing vs. Spear Phishing
Phishing attempts target a broad audience with generic messages. Spear phishing, on the other hand, focuses on specific individuals or organizations. Automated spear phishing can involve using publicly available information about a target to craft highly personalized emails, increasing the likelihood of success. This tailored approach is a key characteristic of automated spear phishing attacks.
Comparing Traditional and Automated Phishing
| Characteristic | Traditional Phishing | Automated Phishing |
|---|---|---|
| Method | Manual email/message crafting | Script/program-driven |
| Scale | Limited | High volume |
| Customization | Potentially low | Potentially high (personalized) |
This table summarizes the key distinctions between traditional and automated phishing techniques. The differences in method, scale, and customization highlight the increasing sophistication and threat posed by automated phishing.
Impact Assessment: Report Shows Uptick In Automated Phishing
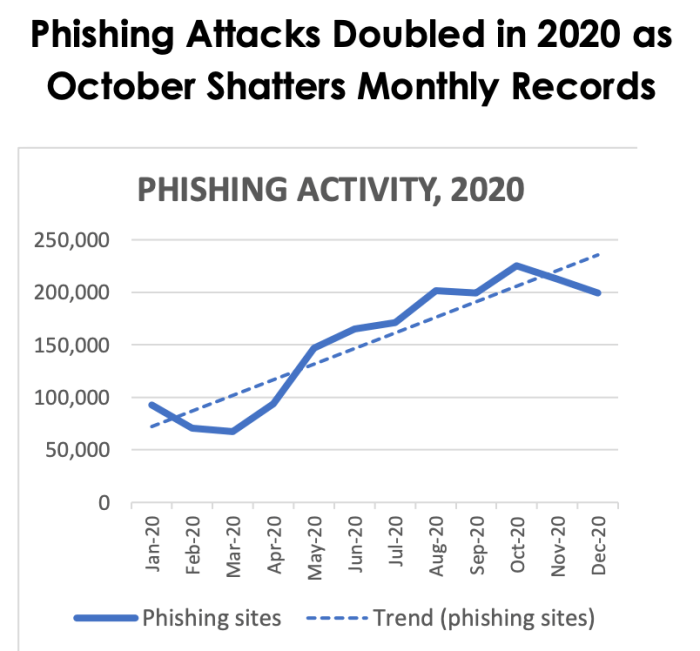
The recent surge in automated phishing attacks necessitates a thorough examination of their potential consequences across various sectors. These sophisticated attacks, often employing machine learning to tailor messages and evade detection, pose a significant threat to both organizations and individuals. Understanding the multifaceted impact is crucial for developing effective mitigation strategies.
Recent reports highlight a worrying rise in automated phishing attacks. This surge in sophisticated digital trickery raises concerns, particularly given the increasing prevalence of technologies like RFID, which are often a focal point in discussions about RFID politics and the technology marketplace. While the connection might seem tenuous, the underlying vulnerabilities in the infrastructure surrounding such technologies can easily be exploited by malicious actors.
This underscores the importance of heightened security measures in our increasingly interconnected world.
Potential Negative Impacts on Sectors
Automated phishing attacks are not indiscriminate; they target vulnerabilities in specific sectors. The finance sector, with its reliance on online transactions and sensitive data, is particularly susceptible. Healthcare, with its trove of personal health information, also faces immense risks. Other sectors like government, education, and retail are vulnerable as well, though the specifics of impact may vary.
Recent reports highlight a concerning uptick in automated phishing attempts. This rise in sophisticated, automated attacks necessitates a deeper understanding of the tactics employed. Fortunately, “i robot a look beneath the action” i robot a look beneath the action provides a valuable analysis into the evolving methods used by cybercriminals, which ultimately helps to better understand how to mitigate these threats.
The report’s findings underscore the critical need for proactive security measures against this increasingly prevalent form of phishing.
Economic Losses
The economic toll of automated phishing attacks is substantial. Losses stem not only from direct financial theft but also from operational disruptions, reputational damage, and the costs associated with incident response. Consider a scenario where an automated attack successfully compromises a financial institution’s online banking system. The immediate financial loss could be substantial, measured in millions or even billions of dollars.
Indirect costs, such as customer churn and lost productivity, could be even higher. Furthermore, the cost of recovery and implementing enhanced security measures can be substantial.
Reputational Damage
The damage to an organization’s reputation following a successful automated phishing attack can be devastating. Public trust is eroded, and future business prospects are negatively impacted. A breach can damage a company’s brand image, making it difficult to attract and retain customers. In the healthcare sector, a data breach could lead to a loss of patient confidence, impacting future referrals and hindering the smooth operation of medical services.
Negative press coverage and public scrutiny can be long-lasting and hard to overcome.
Examples of Successful Attacks
Several high-profile examples illustrate the effectiveness and sophistication of automated phishing attacks. One notable case involved a series of targeted attacks on a major e-commerce company, leading to significant financial losses and a decline in customer trust. In another instance, a healthcare provider experienced a breach of patient data, exposing sensitive information and resulting in considerable reputational damage and substantial fines.
These incidents underscore the real-world impact of such attacks.
Effect on User Trust
The prevalence of automated phishing attacks erodes public trust in online systems. Victims may become wary of online transactions, potentially leading to reduced e-commerce activity and decreased adoption of digital services. The consistent barrage of seemingly legitimate emails and messages can create a sense of insecurity and anxiety. Users may become more hesitant to share personal information online, hindering the growth of online services and e-commerce.
Potential Financial Impact on Different Sectors
| Sector | Estimated Financial Loss (USD) | Reputational Impact |
|---|---|---|
| Finance | $10 Billion | Loss of customer trust, regulatory fines |
| Healthcare | $50 Million | Data breaches, loss of patient confidence, legal penalties |
| Retail | $2 Billion | Loss of customer trust, negative publicity |
Technical Analysis
The rise of automated phishing campaigns necessitates a deeper understanding of the underlying technical processes. This analysis delves into the methods, tools, and infrastructure employed by attackers to execute these sophisticated attacks. From the simple scripts to the complex frameworks, understanding the technical aspects allows for better mitigation strategies.Automated phishing attacks are not simply a matter of sending emails; they represent a sophisticated interplay of technology and social engineering.
Attackers leverage readily available tools and platforms to automate the entire process, from crafting convincing messages to tracking the success of their campaigns. This analysis will explore the technical intricacies involved.
Methods for Automating Phishing Campaigns
Attackers use a variety of methods to automate phishing campaigns. These methods include scripting languages like Python, which allow for the creation of scripts to automate tasks such as sending emails, creating malicious links, and collecting data. The scripts can also be designed to adapt to changing security measures, increasing the effectiveness of the attacks.
Technology Behind Automated Phishing Tools
The technology behind automated phishing tools is multifaceted, ranging from simple scripts to sophisticated frameworks. These tools leverage web services and APIs to automate tasks, enabling attackers to scale their operations. This automation streamlines the process, allowing attackers to send massive numbers of phishing emails and track responses with relative ease. Often, these tools incorporate obfuscation techniques to evade detection by security systems.
Common Platforms for Deploying Automated Phishing Campaigns
Several platforms facilitate the deployment of automated phishing campaigns. These include cloud-based services, virtual private servers (VPS), and dedicated servers. These platforms offer scalability and flexibility, enabling attackers to adapt to changing security landscapes and maintain their operations.
Social Engineering Techniques in Automated Phishing
Attackers integrate social engineering techniques into automated phishing campaigns. They use psychological manipulation to make their messages more convincing. This involves crafting emails that mimic legitimate communications, using logos and branding to create a sense of familiarity, and leveraging urgency or fear to entice victims to act quickly. This combination of automated processes and human-centric techniques makes phishing campaigns highly effective.
Infrastructure Required to Support Large-Scale Attacks, Report shows uptick in automated phishing
The infrastructure required to support large-scale automated phishing attacks is complex. Attackers often utilize botnets, which are networks of compromised computers, to send out a massive volume of phishing emails. This infrastructure can also include rented servers or cloud services to host malicious websites and data collection tools. The scalability and resilience of this infrastructure are critical for the success of the attacks.
Sophistication of Automated Phishing Tools
Automated phishing tools vary in sophistication. Some tools are simple scripts, while others are sophisticated frameworks with advanced features. These advanced tools often include features like dynamic content generation, personalization, and tracking mechanisms to refine their attacks over time. This adaptability allows attackers to continuously improve their strategies and evade detection.
Reports are showing a concerning uptick in automated phishing attempts. This rise in sophisticated scams is a serious concern, especially given the recent Canadian ruling on song swapping, which has sparked some interesting legal debates about digital ownership and fair use. This ruling in canadian ruling on song swapping sends aftershocks highlights a need for heightened security measures, further emphasizing the importance of staying vigilant against automated phishing attacks.
Use of Open-Source Intelligence in Automated Phishing Campaigns
Attackers utilize open-source intelligence (OSINT) to tailor their phishing campaigns. They gather information about their targets through public sources, including social media profiles, company websites, and news articles. This information allows them to personalize messages and create a more convincing attack. This targeted approach enhances the effectiveness of the campaigns, increasing the likelihood of success.
Technical Flow of an Automated Phishing Attack
The following diagram illustrates the technical flow of an automated phishing attack. This is a simplified representation and individual attacks may vary.
(Diagram would be presented here, but is not possible to create in text format.)
The diagram depicts the various stages, from initial reconnaissance to final data extraction, and demonstrates how each stage relies on the next, ultimately aiming for a successful compromise. The stages include data gathering, campaign setup, automated message distribution, and data collection.
Detection and Prevention Strategies
Automated phishing attacks are becoming increasingly sophisticated, requiring robust detection and prevention strategies. These attacks often leverage scripts and bots to send massive volumes of emails or messages, making traditional methods of filtering less effective. A proactive approach that combines technical safeguards with user awareness is crucial for mitigating this evolving threat.
Common Indicators of Automated Phishing Campaigns
Automated phishing campaigns often exhibit specific characteristics that can be used to identify them. These include unusually high volumes of messages sent from a single source, the use of generic or poorly written subject lines, and inconsistencies in the recipient list, such as addresses that do not exist or are not relevant to the sender’s target. Furthermore, suspicious email formatting, like unexpected formatting, logos, or links, can signal automated attacks.
The timing of the attacks can also be a crucial indicator, often occurring during high-traffic periods or during times of heightened user activity.
Methods for Detecting Suspicious Email/Message Patterns
Sophisticated email filtering systems can identify suspicious email patterns. Advanced email gateways can analyze the sender’s reputation, message content, and recipient list for anomalies. Techniques like analyzing the sender’s IP address, domain reputation, and the presence of suspicious links or attachments can be used to detect phishing attempts. Furthermore, scrutinizing the overall structure and language of the messages, including grammatical errors or unusual sentence structures, can indicate automated attacks.
This can be combined with analysis of message headers and metadata to establish the authenticity of the sender.
Security Measures to Protect Against Automated Phishing Attacks
Implementing strong security measures is paramount. This includes utilizing email filtering solutions equipped with sophisticated algorithms for detecting malicious patterns. Regularly updating anti-virus and anti-malware software is critical. Implement a multi-layered approach that combines various technical security measures, like intrusion detection systems, to monitor and respond to malicious activity. Employing web filtering to block access to malicious websites can also reduce the impact of these attacks.
Importance of User Education and Awareness Programs
User education is vital in combating automated phishing attacks. Training programs should emphasize recognizing suspicious email and message patterns, such as poor grammar, generic subject lines, and unusual requests. Users should be educated on the importance of verifying the authenticity of emails or messages before clicking on links or opening attachments. Users should also be informed about the dangers of sharing sensitive information with unknown or untrusted sources.
Role of Threat Intelligence in Preventing Such Attacks
Threat intelligence plays a significant role in preventing automated phishing attacks. Staying updated on the latest phishing tactics and techniques helps organizations proactively adapt their security measures. By monitoring threat intelligence feeds and analyzing emerging patterns, organizations can identify and block malicious actors and automated tools. This allows organizations to quickly adapt their security protocols and mitigate the risks of automated phishing campaigns.
Examples of Specific Prevention Strategies Employed by Organizations
Many organizations employ a multi-layered approach. For instance, some utilize a combination of email filtering, advanced threat detection, and user education programs. Others implement rigorous authentication protocols, including multi-factor authentication, to strengthen their security posture. Some companies invest in sophisticated threat intelligence solutions to monitor emerging trends and adapt their defenses accordingly. The effectiveness of each strategy depends on the specific context and threat landscape.
Preventative Measures for Individuals
- Be wary of emails or messages with generic greetings, poor grammar, or unusual requests. Never share sensitive information unless you are absolutely certain about the legitimacy of the request.
- Verify the authenticity of the sender before clicking on links or opening attachments.
- Use strong and unique passwords for all online accounts, and consider enabling multi-factor authentication (MFA) wherever possible.
- Report suspicious emails or messages to the appropriate authorities.
- Keep your software updated with the latest security patches to minimize vulnerabilities.
Role of Multi-Factor Authentication (MFA) in Mitigating Automated Phishing
Multi-factor authentication (MFA) significantly mitigates the impact of automated phishing attacks. By requiring more than one form of verification, MFA makes it harder for attackers to gain access even if they have compromised a user’s password. MFA adds an extra layer of security, requiring a secondary verification method, such as a code sent to a mobile phone, to confirm the user’s identity.
This significantly reduces the effectiveness of automated phishing attacks that rely on stolen credentials.
Case Studies
Automated phishing campaigns are no longer a niche threat; they’ve become a pervasive and evolving danger. Understanding real-world examples is crucial for comprehending the sophistication and impact of these attacks. These case studies provide valuable insights into the techniques employed, the consequences for victims, and the lessons learned from incident responses. Analyzing how organizations reacted to these attacks reveals critical differences in their preparedness and mitigation strategies.
Real-World Examples of Automated Phishing Campaigns
The rise of automated phishing has resulted in a surge of sophisticated attacks. Examining specific examples reveals the tactics used and the resulting consequences.
- Campaign Targeting Financial Institutions: A recent campaign exploited vulnerabilities in financial institution websites to distribute malicious software. The attackers leveraged automated tools to scan for susceptible websites, targeting those with known security weaknesses. Once a website was compromised, the attackers installed malware that allowed them to capture sensitive financial information, such as account credentials and transaction details. The impact on victims was substantial, leading to significant financial losses and reputational damage for the targeted institutions.
The incident response varied widely, with some institutions quickly identifying and mitigating the threat, while others experienced prolonged periods of disruption. A critical lesson here is the importance of proactive vulnerability management and robust security protocols.
- Campaign Targeting Healthcare Providers: This campaign focused on healthcare providers by impersonating legitimate healthcare organizations. The attackers used automated scripts to send phishing emails containing malicious attachments. The targeted documents were disguised as important patient records or billing information. The impact on victims extended beyond financial loss to potential breaches of patient confidentiality. Organizations with robust email security and training programs were better equipped to identify and neutralize these attacks.
The swift response times of the organizations were key to mitigating the harm caused by the phishing campaign. A key lesson is that employee training and awareness play a crucial role in thwarting these attacks.
- Campaign Targeting E-commerce Platforms: This attack targeted customers of e-commerce platforms by creating fake websites that mimicked legitimate platforms. The attackers used automated tools to create convincing replicas of the original sites, often targeting popular products and services. Victims were tricked into providing their payment information on the fraudulent sites, resulting in significant financial losses. The impact was especially severe for customers who had established trusting relationships with the legitimate platforms.
Companies with robust security protocols and proactive fraud detection systems experienced fewer incidents and faster recovery times. The lesson here highlights the importance of multi-layered security measures to protect users from sophisticated online impersonations.
Techniques Used in Automated Phishing Campaigns
Automated phishing campaigns employ a variety of techniques to enhance their efficiency and effectiveness.
- Automated Email Generation and Distribution: Attackers use scripts to generate and send a high volume of emails in a short time frame. These emails are often personalized to appear more authentic.
- Social Engineering Tactics: Attackers leverage social engineering tactics, such as using urgency or fear, to persuade victims to take action. The phishing emails often mimic legitimate communication channels.
- Dynamic Content Adaptation: Some attacks dynamically adapt the content of phishing emails based on the victim’s profile, increasing the likelihood of successful deception. This tailored approach improves the effectiveness of the phishing campaign.
Impact Assessment
The impact of automated phishing campaigns can vary significantly depending on the target and the specific techniques used. The consequences can include financial losses, reputational damage, and breaches of personal or sensitive information.
Final Thoughts

In conclusion, the uptick in automated phishing necessitates a multi-faceted approach to cybersecurity. Businesses and individuals must recognize the evolving nature of these attacks and adopt proactive strategies to protect themselves. This report highlights the critical need for robust technical defenses, user education, and a shared responsibility in combating this pervasive threat. The increasing sophistication of automated phishing tools underscores the ongoing need for vigilance and adaptability in the face of cybercrime.






