Secret Trojan Network Superworm Threat
Secret trojan network could produce superworm, a scenario that paints a chilling picture of a sophisticated and devastating cyberattack. This potential threat leverages a hidden network of malicious trojans, designed to assemble and unleash a superworm—a highly contagious and destructive piece of malware capable of widespread system compromise.
The Artikel delves into the mechanics of such a network, from its creation and concealment methods to the potential impacts on individuals, organizations, and the global digital landscape. It also explores the historical precedents and countermeasures that can mitigate the risk.
Defining the “Secret Trojan Network”
A secret trojan network is a clandestine system of compromised computers, often hidden within legitimate networks, that operate under malicious control. These networks are designed for covert activities, ranging from data theft and espionage to sabotage and the propagation of further malware. Their clandestine nature makes them particularly difficult to detect and dismantle.A secret trojan network isn’t simply a collection of infected machines; it’s a carefully orchestrated system.
Its construction and maintenance require meticulous planning and execution, leveraging various methods to evade detection and maintain operational security. These methods often involve sophisticated techniques to obscure the network’s true nature and purpose.
Methods of Creation and Maintenance
The creation and maintenance of a secret trojan network hinges on several methods. These include sophisticated techniques to mask the network’s presence within legitimate systems, thereby evading detection. Initial infection often involves exploiting vulnerabilities in software or through social engineering tactics. Compromised systems are then used to establish and maintain communication channels, enabling the malicious actors to control the network remotely.
- Exploiting Software Vulnerabilities: Malicious actors frequently leverage known software vulnerabilities to gain initial access to systems. These vulnerabilities can be present in operating systems, applications, or even firmware. For example, a vulnerability in a widely used network management tool could allow a malicious actor to gain control over numerous machines within a network.
- Social Engineering: Sophisticated social engineering techniques can trick users into installing malware. This can involve phishing emails, malicious websites, or even seemingly harmless attachments. For instance, a malicious actor could send emails pretending to be from a legitimate company, requesting users to click on a link to update their account information. The link might lead to a website that installs malware on the victim’s machine.
- Compromised Accounts: Compromised credentials, obtained through various methods, can be used to gain access to accounts with elevated privileges. Once inside, the attacker can install trojans and establish backdoors, allowing for remote control and data exfiltration.
Vulnerabilities in Cybersecurity Systems
Current cybersecurity systems often face vulnerabilities that can be exploited to establish a secret trojan network. These vulnerabilities stem from various factors, including inadequate security protocols, outdated software, and a lack of comprehensive threat intelligence.
- Lack of Patching: Failing to apply timely security updates to software leaves systems vulnerable to known exploits. Malicious actors frequently target systems with unpatched vulnerabilities to gain initial access.
- Insufficient Security Awareness Training: Users who lack awareness of phishing techniques or other social engineering tactics are more susceptible to malware infections. A lack of training can lead to a significant security gap within an organization.
- Poor Network Segmentation: Poorly segmented networks can allow malicious actors to move laterally across the network once an initial foothold is gained. If different departments or sections of a network are not adequately separated, it becomes easier for attackers to spread malware across the entire organization.
Types of Trojans Involved
Various types of trojans are employed in a secret trojan network, each designed for specific tasks.
- Remote Access Trojans (RATs): RATs provide malicious actors with remote control over infected machines. These can be used for data theft, keylogging, or even installing additional malware. RATs are frequently used in the establishment and maintenance of a secret trojan network.
- Backdoors: These are programs that create a hidden entry point into a system, bypassing standard security measures. Backdoors allow malicious actors to access and control the system remotely without detection.
- Data Stealers: These trojans are specifically designed to steal sensitive data, such as login credentials, financial information, or intellectual property. These programs can be used to gather information from multiple victims within a network.
Concealment Techniques
Concealing a secret trojan network requires careful planning and execution. The methods used to hide the network often involve advanced techniques to evade detection.
- Stealthy Communication Channels: Utilizing encrypted channels and obfuscated communication protocols makes it harder to detect malicious activity. The use of anonymizing proxies and tunneling protocols can further complicate tracing the source of the communication.
- Network Traffic Masking: Camouflaging malicious network traffic within legitimate traffic patterns can help evade detection by intrusion detection systems. Techniques like traffic shaping and data encryption can obscure malicious activity.
- Evading Anti-Virus Software: Malware is constantly evolving, and some advanced trojans are specifically designed to evade detection by traditional antivirus software. This can involve techniques such as polymorphism, code obfuscation, and self-modification.
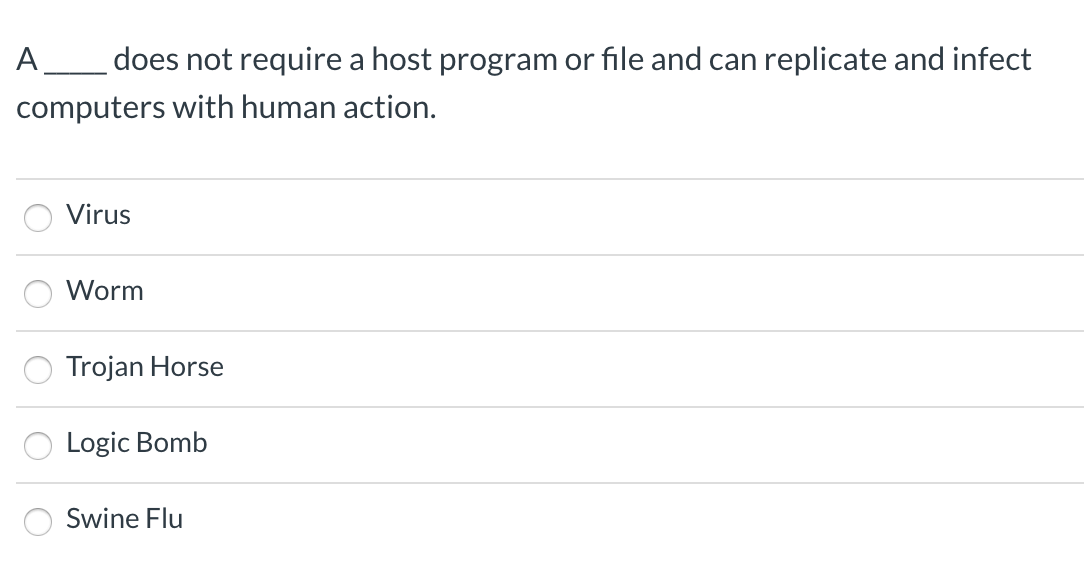
Understanding the “Superworm” Concept: Secret Trojan Network Could Produce Superworm
The concept of a “superworm” in the digital realm evokes images of a highly sophisticated and devastating computer worm, capable of spreading rapidly and inflicting widespread damage across interconnected systems. This differs from more conventional worms, which might focus on a specific network or operating system. A superworm, by design, aims for maximum impact and disruption. Understanding its characteristics and potential ramifications is crucial for anticipating and mitigating future threats.The term “superworm” signifies a highly advanced, self-propagating malware program that can exploit vulnerabilities in a wide array of systems and networks.
Its design prioritizes rapid propagation, potentially overwhelming defenses and causing significant disruption. Unlike simpler worms, a superworm is not merely an exploit but a meticulously crafted tool, potentially capable of adapting and evolving in real-time.
A secret trojan network could potentially spawn a superworm, wreaking havoc on connected devices. This highlights the critical need for robust security measures, especially in high-end routers, where vulnerabilities can be exploited by malicious actors. The challenges remain for high-end router suppliers here to anticipate and mitigate these threats. Ultimately, the threat of a superworm from a secret trojan network remains a serious concern.
Characteristics of a Superworm
A superworm possesses several key characteristics that distinguish it from other malware types. These include an advanced ability to autonomously spread across various systems, utilizing multiple propagation vectors. Furthermore, a superworm may feature sophisticated evasion techniques, rendering traditional security measures ineffective. The worm might also incorporate sophisticated attack strategies, making it harder to contain or eradicate.
Examples of Past Computer Worms and their Impacts
Several computer worms have demonstrated the devastating potential of malicious software. The Code Red worm, for instance, exploited a vulnerability in Microsoft Internet Information Services, causing significant disruption to web servers in 2001. The SQL Slammer worm, exploiting a vulnerability in Microsoft SQL Server, demonstrated the rapid spread and large-scale impact possible when a worm targets a wide range of systems.
These examples highlight the potential damage of worms, but the scale of a superworm would likely be far greater.
Comparison with Other Malware Types
A superworm contrasts with other malware types, such as viruses or Trojans, in its inherent self-propagating nature. Unlike viruses, which require human intervention to spread, a superworm propagates automatically. Moreover, unlike Trojans, which often rely on social engineering or user deception, a superworm exploits vulnerabilities directly. This self-replication and automated spread are central to the superworm’s destructive potential.
Potential Damage a Superworm Could Cause
The potential damage a superworm could inflict is significant and multifaceted. It could cripple critical infrastructure, disrupt financial transactions, and compromise sensitive data. Disruptions to communication networks, power grids, or financial systems could have widespread societal repercussions. Furthermore, the long-term economic costs of a superworm attack could be immense, requiring extensive remediation and recovery efforts.
The shadowy secret trojan network could potentially unleash a superworm, a truly devastating cyber threat. This, coupled with the need for more secure systems, makes recent discussions around a new era of seamless computing, like those highlighted in gates envisions new era of seamless computing , incredibly crucial. Ultimately, this interconnected world demands a proactive approach to security to prevent such a superworm from emerging.
Methods of Propagation a Superworm Could Use
A superworm could utilize various propagation methods to spread rapidly. These include exploiting vulnerabilities in network protocols, such as TCP/IP or DNS, and leveraging vulnerabilities in software applications. Moreover, a superworm might employ social engineering tactics, potentially tricking users into executing malicious code. The choice of method depends on the target environment and vulnerabilities present.
Potential Impacts Across Systems and Networks
The impacts of a superworm could manifest across diverse systems and networks, creating cascading effects. Critical infrastructure, such as power grids and communication networks, could be severely impacted, leading to widespread outages and disruption. Furthermore, financial systems could be compromised, leading to financial losses and economic instability. The potential for widespread panic and social disruption is also a critical concern.
Potential Mechanisms of Creation
Building a secret trojan network capable of spawning a superworm involves a meticulous and multi-layered approach. This intricate process requires careful planning, exploiting specific vulnerabilities, and maintaining stealth throughout the entire operation. The initial stages are crucial in establishing a clandestine infrastructure that can later support the development and deployment of the superworm.The creation of such a network hinges on several key elements: initial infiltration, establishing command and control channels, data exfiltration, and ultimately, the development and deployment of the superworm itself.
This complex process demands significant technical expertise and a deep understanding of the target systems and their vulnerabilities.
Initial Infiltration Techniques
The initial infiltration phase is the cornerstone of the entire operation. Successful infiltration often relies on social engineering tactics, exploiting software vulnerabilities, or leveraging zero-day exploits. Attackers must gain unauthorized access to a network and establish a foothold without raising suspicion.
- Exploiting Known Vulnerabilities: Targeting known software vulnerabilities in operating systems, applications, or network services provides a readily available avenue for initial infiltration. Attackers can leverage publicly available exploits or create their own variations.
- Social Engineering: Deceptive techniques, such as phishing emails or malicious websites, can trick users into installing malware or revealing sensitive information. This approach often targets individuals with limited technical awareness.
- Zero-Day Exploits: Targeting previously unknown vulnerabilities is a highly effective method for achieving initial access. These exploits, if successfully employed, grant attackers an advantage over defenders who lack protective measures against them.
Establishing Command and Control Channels
Once initial access is secured, the attackers need to establish a secure communication channel, or command and control (C&C) server, to maintain control over the compromised systems. These C&C channels are vital for managing the network, updating malicious code, and issuing commands to the affected machines.
- Stealthy Communication Protocols: Using encrypted communication channels, like SSL/TLS, and obfuscating the traffic to evade detection are critical for maintaining the stealthy nature of the operation. The selection of appropriate protocols and servers are essential for masking the communication between the compromised systems and the attacker’s command center.
- Distributed C&C Infrastructure: A distributed network of C&C servers, spread across different locations, enhances resilience and evades detection. This distributed model makes it significantly more challenging for security personnel to locate and shut down the entire network.
Data Exfiltration and Superworm Development
Data exfiltration is critical for the attackers to gain insights into the network’s structure and identify potential vulnerabilities. Once the data is collected, the attackers can utilize it to develop the superworm. The superworm’s design is tailored to exploit specific vulnerabilities.
- Data Exfiltration Techniques: Employing various data exfiltration techniques like covert channels, or manipulating network traffic to send data to a remote server, is critical to gathering intelligence on the target system. This intelligence aids in the development of the superworm.
- Superworm Design: The superworm is designed to leverage identified vulnerabilities within the target systems. Its design should be modular and adaptable, allowing it to exploit diverse vulnerabilities, potentially spanning different operating systems or applications. This adaptability makes the superworm exceptionally potent and difficult to defend against.
Potential Attack Vectors
Attack vectors represent the specific pathways an attacker uses to exploit a vulnerability. They are the avenues through which the malware enters and spreads.
- Network Protocols: Exploiting vulnerabilities in network protocols, such as TCP/IP, or misconfigurations in firewalls, can be utilized for gaining access to a network.
- Software Vulnerabilities: Known and unknown vulnerabilities in applications or operating systems provide entry points for the malware.
- Operating System Weaknesses: Weaknesses in the operating system’s core functionalities can be exploited to gain unauthorized access and spread the malware throughout the network.
Code Snippets (Illustrative Purposes Only)
Illustrative examples of code snippets (not executable):
// Example of a function to exploit a buffer overflow vulnerability void exploit_buffer_overflow(char* target_buffer, char* payload) // ... code to manipulate the target buffer and execute the payload
// Example of a covert channel using network packets void send_data_covertly(char* data, int data_length) // ... code to embed data within network packets
Impact and Consequences

A successful deployment of a superworm, a highly sophisticated and self-replicating malware, would have devastating consequences across various sectors.
Its potential to rapidly spread and compromise systems poses a significant threat to global infrastructure and digital security. Understanding the potential ramifications is crucial for developing effective countermeasures and mitigation strategies.
The consequences of a superworm attack extend far beyond the initial infection. The multifaceted nature of the attack can disrupt essential services, cripple economies, and erode public trust in digital systems. This analysis explores the potential impact on individuals, organizations, and society as a whole.
Potential Economic Losses
The economic fallout from a superworm attack could be catastrophic. Massive disruption of critical infrastructure, such as financial institutions, power grids, and communication networks, would lead to significant financial losses. Supply chains would be severely impacted, potentially leading to widespread shortages and price hikes. The cost of recovery and remediation would be astronomical, encompassing the expense of system restoration, data recovery, and legal proceedings.
Companies could face substantial losses due to lost productivity, decreased customer confidence, and reputational damage. Examples of past cyberattacks highlight the potential for billions of dollars in damages.
A secret trojan network could potentially unleash a superworm, wreaking havoc on digital systems. This raises concerns about the security vulnerabilities across different operating systems, including Apple, Linux, and BSD, the other platforms that we often overlook. Understanding the intricacies of these operating systems, like those discussed in apple linux and bsd the other platforms , is crucial to fortifying our defenses against such threats.
Ultimately, a comprehensive approach to cybersecurity is vital to prevent a superworm from devastating the digital landscape.
Societal Impacts
A successful superworm attack could have profound societal impacts. Widespread disruption of essential services, such as healthcare, education, and transportation, would have far-reaching consequences. Public trust in digital systems could be severely eroded, leading to decreased adoption of online services and potentially hindering societal progress. The attack could exacerbate existing social inequalities, as vulnerable populations may be disproportionately affected.
The potential for chaos and panic could create widespread societal instability.
Impact on Individual Users and Organizations
Individual users could face significant personal losses, including compromised financial accounts, identity theft, and the loss of sensitive personal data. Organizations would experience severe disruptions to operations, including loss of data, system downtime, and reputational damage. The attack could also lead to legal liabilities, as organizations may face lawsuits from affected individuals and clients. The potential for identity theft and financial fraud could be particularly damaging to individuals and organizations.
Long-Term Effects
The long-term effects of a superworm attack could be lasting and far-reaching. The attack could lead to a heightened awareness of cybersecurity risks and the need for robust security measures. However, it could also lead to a decline in public trust and a reluctance to adopt new technologies. The cost of implementing improved security protocols and developing advanced detection and response mechanisms could be substantial.
The long-term effects would depend on the speed and effectiveness of recovery efforts and the development of more robust cybersecurity strategies. Recovery and remediation efforts could take years to fully restore systems and rebuild trust. A critical component of long-term effects is the development of a more secure and resilient digital infrastructure.
Countermeasures and Mitigation Strategies
The creation of a secret Trojan network, capable of evolving into a superworm, poses a significant threat to global digital infrastructure. Effective countermeasures are crucial to mitigate the potential damage and disruption such a network could cause. Proactive measures, robust security protocols, and vigilant monitoring are essential to prevent and contain such an attack.
Comprehensive security strategies must be implemented across all layers of the digital ecosystem, from individual users to large-scale corporate networks. These strategies must be adaptable and dynamic, able to respond to emerging threats and vulnerabilities. By understanding the potential mechanisms and focusing on preventative measures, we can enhance the resilience of our digital world against such malicious actors.
Preventative Measures
A multi-layered approach is essential to prevent the creation of a secret Trojan network. Implementing strict access controls, regular security audits, and comprehensive vulnerability assessments are vital first steps. Regularly reviewing and updating security policies, especially those related to user access and data handling, is critical to maintaining a strong defense. Furthermore, encouraging strong passwords, multi-factor authentication, and regular security awareness training for employees is crucial to preventing initial compromise.
- Employing strong access controls: Implementing strict user permissions and access limitations based on the principle of least privilege significantly reduces the potential attack surface. This includes regularly reviewing and updating access rights, restricting administrative privileges, and employing robust user authentication methods.
- Conducting regular security audits and vulnerability assessments: Proactively identifying and addressing potential vulnerabilities in systems and applications is crucial. Regular security audits, performed by qualified professionals, can uncover weaknesses that malicious actors might exploit. This also includes conducting vulnerability assessments to identify and address potential flaws in software, hardware, and network configurations.
- Enforcing robust security protocols and practices: Establish and maintain strict adherence to security protocols across the entire organization. This involves creating and implementing a comprehensive security policy, training employees on security best practices, and continuously monitoring compliance.
Robust Security Protocols and Practices
Robust security protocols and practices are not just reactive measures; they are fundamental to a proactive security posture. This involves establishing clear security policies, implementing strong encryption techniques, and continuously monitoring network traffic for suspicious activities. Maintaining up-to-date security software and hardware is equally important.
- Implementing strong encryption: Employing strong encryption protocols for data transmission and storage is crucial to protect sensitive information from unauthorized access. Modern encryption algorithms, such as AES-256, are essential for safeguarding sensitive data.
- Regular software updates and patches: Maintaining up-to-date software and operating systems is critical to address known vulnerabilities. Proactively installing security patches and updates helps to mitigate the risk of exploitation by malicious actors.
- Using intrusion detection and prevention systems (IDPS): Implementing IDPS to monitor network traffic and identify suspicious activities is crucial. These systems can alert security personnel to potential threats in real-time, enabling swift response and mitigation.
Continuous Monitoring and Threat Detection Systems
Continuous monitoring and proactive threat detection systems are essential to detect and respond to emerging threats in a timely manner. These systems must be adaptive and able to learn from new attack patterns and tactics. Monitoring tools and systems should be configured to detect anomalies and unusual behavior, providing early warning of potential intrusions.
- Implementing security information and event management (SIEM) systems: SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events. This allows for better threat detection and incident response.
- Utilizing threat intelligence feeds: Staying informed about emerging threats and vulnerabilities is crucial. Subscribing to threat intelligence feeds from reputable sources helps to proactively identify and respond to potential attacks.
Timely Patching and Updates
Timely patching and updates are crucial to maintaining a strong security posture. Delaying updates leaves systems vulnerable to known exploits, making them an easy target for malicious actors. Effective patch management processes and procedures are vital for timely and accurate implementation.
- Establishing a robust patch management process: This involves identifying vulnerable systems, prioritizing patches, testing patches in a controlled environment, and deploying patches in a phased or prioritized manner.
- Automating patch deployment: Automating the deployment of patches reduces manual errors and ensures that systems are updated quickly and efficiently.
Incident Response and Recovery Strategy
A well-defined incident response and recovery strategy is crucial for minimizing the impact of a successful attack. This strategy should include procedures for containment, eradication, recovery, and lessons learned.
- Developing a comprehensive incident response plan: This plan should Artikel the roles and responsibilities of individuals and teams during an incident. It should also include detailed procedures for containment, eradication, and recovery.
- Establishing a dedicated incident response team: This team should be trained and equipped to handle security incidents effectively and efficiently. Regular drills and exercises should be conducted to maintain readiness.
Illustrative Scenarios
A secret Trojan network, designed to exploit vulnerabilities and propagate rapidly, can evolve into a devastating “superworm” capable of widespread damage. Understanding potential scenarios is crucial for developing effective countermeasures. These scenarios highlight the diverse ways a covert network can escalate, emphasizing the importance of proactive security measures.
Scenario Table
The following table Artikels potential scenarios, their descriptions, potential impact, and corresponding countermeasures to mitigate the threats.
| Scenario | Description | Impact | Countermeasure |
|---|---|---|---|
| Scenario 1: Targeted Infrastructure Compromise | A sophisticated actor compromises critical infrastructure components (e.g., power grids, financial institutions) through a stealthy Trojan. The Trojan network then leverages vulnerabilities within the compromised systems to spread further. | Widespread disruption of essential services, economic damage, potential loss of life, and societal instability. | Robust network segmentation, intrusion detection systems with advanced anomaly detection capabilities, and regular security audits of critical infrastructure. |
| Scenario 2: Supply Chain Exploitation | A malicious actor infiltrates a trusted software or hardware supply chain. The Trojan is embedded within seemingly legitimate products, spreading rapidly across a large number of systems. | Extensive system compromise across multiple organizations, data breaches, financial losses, and reputational damage. | Stricter supply chain security protocols, rigorous vendor vetting, and advanced code analysis for software and hardware components. |
| Scenario 3: Social Engineering Campaign | A covert Trojan is disseminated through a targeted social engineering campaign, tricking users into installing the malicious software. The Trojan network subsequently exploits user interactions and system vulnerabilities. | Data breaches, financial fraud, and potential disruption of operational processes within multiple organizations, including government agencies and businesses. | Comprehensive security awareness training for employees, robust email filtering and anti-phishing mechanisms, and multi-factor authentication protocols. |
| Scenario 4: IoT Device Exploitation | A large-scale network of compromised Internet of Things (IoT) devices, infected by a Trojan, acts as a distributed network to facilitate the propagation of the superworm. These devices are used to overwhelm targets with traffic or launch coordinated attacks. | Massive denial-of-service (DoS) attacks, widespread network disruption, and potential physical damage to critical infrastructure. | Secure configuration of IoT devices, regular firmware updates, network segmentation, and advanced threat detection systems capable of identifying and mitigating IoT-based threats. |
Technical Aspects of Network Concealment
Crafting a clandestine trojan network necessitates sophisticated techniques to mask its presence from detection. This involves a multi-layered approach, employing methods to obscure communication paths, evade intrusion detection systems, and circumvent security measures. The challenge lies in creating a system that’s both effective and resilient to evolving countermeasures.Understanding the methods used to conceal a trojan network is crucial for developing effective defensive strategies.
By examining the techniques employed, we can better anticipate and thwart these insidious operations. This section delves into the intricate technical aspects of network concealment, providing insight into the tactics used to maintain stealth and evade detection.
Techniques for Hiding the Secret Trojan Network, Secret trojan network could produce superworm
The success of a clandestine trojan network hinges on its ability to remain hidden. Various techniques are employed to achieve this, ranging from encrypting communication channels to employing proxy servers. These techniques aim to obscure the network’s activity from scrutiny.
- Encryption: Encrypting communication channels between compromised systems and the command and control (C&C) server significantly obscures the nature of the traffic. This encryption makes it difficult for intrusion detection systems (IDS) to analyze the data and identify malicious activity. Advanced encryption algorithms like AES-256 further enhance the security and complexity of the communication, making it extremely difficult to decipher without the decryption key.
- Proxy Servers and Tunneling: Employing proxy servers and various tunneling protocols can mask the origin and destination of traffic. This makes it harder to trace the communication back to the compromised systems and their operators. Using anonymization techniques like Tor further complicates the identification process.
- Steganography: This technique involves concealing data within seemingly innocuous files or communication channels. This makes it challenging for detection mechanisms to pinpoint malicious activity, blending the covert network traffic with normal network activity. An example might be hiding encrypted commands within seemingly benign images or audio files. The challenge lies in avoiding suspicion by using realistic-looking data that is not obviously malicious.
Evading Intrusion Detection Systems (IDS)
IDSs are critical security tools designed to identify malicious activity on a network. A sophisticated trojan network must adapt to circumvent these systems.
- Using Least Privileged Accounts: Restricting access to minimal necessary privileges for the trojan agents can significantly reduce the likelihood of triggering an alert. This limits the scope of the actions the agents can perform and reduces the visibility of the malicious activity. This method makes it harder for an IDS to identify suspicious patterns of activity.
- Obfuscation Techniques: Using obfuscation techniques on the malware code makes it more difficult for security analysis tools to recognize the malicious intent. This can involve using complex code structures, polymorphism, or other methods to obscure the malicious code.
- Adapting to IDS Signatures: Regularly updating the malicious code and techniques employed by the trojan network can help it evade detection by constantly evolving its signature. This is a dynamic process, demanding continuous research and development.
Anonymization Techniques
Anonymization techniques aim to mask the identity of the actors involved in the network.
- Dynamic IP Addresses: Employing dynamic IP addresses or VPNs (Virtual Private Networks) can make it harder to trace back the network to a specific location or individual. This method of hiding the source of the traffic is frequently employed.
- Tor Network: The Tor network is a decentralized network that routes traffic through multiple relays, making it extremely difficult to trace the origin and destination of the traffic. It’s often used by individuals seeking anonymity, but also by malicious actors for covert communication.
Limitations of Concealment Methods
Despite the sophistication of concealment techniques, there are inherent limitations.
- Complexity and Resource Demands: Implementing and maintaining complex concealment techniques requires significant resources and expertise. This creates a potential vulnerability in the operation.
- Evolving Detection Methods: IDSs and security tools are constantly evolving, leading to the eventual detection of even the most sophisticated concealment methods. Security researchers and organizations are constantly developing new ways to identify malicious activities.
- Human Error: Human error can still lead to the exposure of the network. This can include misconfigurations, leaked information, or even mistakes made during the implementation of the concealment methods.
Bypassing Firewalls and Security Measures
Overcoming firewall and security measures requires a detailed understanding of the target systems.
- Exploiting Known Vulnerabilities: Identifying and exploiting vulnerabilities in software or operating systems can allow malicious actors to bypass firewalls and access systems. This can involve using known exploits to gain access to the network or systems. A good example is exploiting a known vulnerability in a web server to gain unauthorized access.
- Social Engineering: Manipulating individuals to grant access or bypass security measures is a crucial aspect of network infiltration. Social engineering can be very effective, leading to the compromise of the network or individual systems.
- Denial-of-Service (DoS) Attacks: Overloading a network or system with traffic can overwhelm its defenses, allowing for temporary access or compromise. This can disrupt network operations and allow for temporary access.
Analysis of Historical Threats
The historical record offers invaluable insights into the evolution of malware and the potential impact of a superworm. Studying past outbreaks reveals recurring patterns in attacker tactics and provides a framework for understanding the risks associated with this novel threat. Examining successful attacks and their outcomes allows for the identification of vulnerabilities and potential mitigation strategies. Understanding how past threats developed, spread, and were countered is crucial to anticipating and preparing for the emergence of new, more sophisticated threats.Historical malware outbreaks provide a critical lens through which to assess the potential consequences of a superworm.
Analyzing past campaigns allows us to identify potential weaknesses in current defenses, enabling proactive measures to be implemented. This analysis is not just about historical events, but a crucial step towards future preparedness.
Past Malware Outbreaks and Their Relation to the Superworm Threat
Numerous malware outbreaks throughout history share common characteristics that are relevant to understanding the potential impact of a superworm. The Code Red worm, for instance, exploited a vulnerability in Microsoft IIS servers, rapidly spreading across the internet. The MyDoom worm utilized email spam and other social engineering techniques for propagation. These examples demonstrate the ability of malware to leverage vulnerabilities and social engineering to spread rapidly, causing widespread disruption.
The potential for a superworm to exploit multiple vulnerabilities simultaneously, combined with its self-replicating nature, suggests a far more extensive and devastating impact than previous outbreaks.
Comparison of Past Threats and Potential Superworm Impact
| Threat | Impact | Spread Method |
|---|---|---|
| Code Red Worm | Widespread disruption of web services, significant downtime for affected systems. | Exploiting vulnerabilities in Microsoft IIS servers. |
| MyDoom Worm | Massive email spam, significant network congestion, and denial-of-service attacks. | Spam emails and social engineering. |
| Superworm (Potential) | Potentially catastrophic disruption to global networks, widespread data breaches, significant financial losses. | Exploiting multiple vulnerabilities, self-replication across diverse systems. |
The potential impact of a superworm significantly surpasses that of previous outbreaks. Its self-replicating nature and ability to exploit multiple vulnerabilities simultaneously would likely lead to far greater disruption and damage to critical infrastructure.
Common Patterns in Previous Attacks
A recurring pattern in past attacks is the exploitation of known vulnerabilities. Attackers often target systems with known weaknesses, leveraging automated tools to identify and exploit these vulnerabilities. Another common pattern is the use of social engineering techniques to trick users into executing malicious code or providing sensitive information. This illustrates the importance of robust security measures across all aspects of a system, including user education and secure coding practices.
Learning Points from Historical Data
Historical data reveals the importance of proactive vulnerability management. Regular patching and security updates are crucial in mitigating the impact of known vulnerabilities. Furthermore, robust incident response plans are essential to quickly contain and mitigate the damage caused by an outbreak. The ability to learn from past errors and adapt security strategies is critical in preventing future incidents.
Evolving Tactics and Techniques of Attackers
Attackers are constantly adapting their tactics and techniques. They are leveraging new technologies and exploiting emerging vulnerabilities. Advanced persistent threats (APTs) often employ sophisticated techniques to gain access to systems and maintain persistent presence. The constant evolution of attacker methods emphasizes the importance of continuous learning and adaptation in the realm of cybersecurity.
Wrap-Up
In conclusion, the potential for a secret trojan network to unleash a superworm highlights the critical need for proactive cybersecurity measures. The intricate details revealed in the Artikel underscore the evolving sophistication of cyber threats and the urgent necessity for robust defenses, vigilance, and preparedness. The analysis of historical threats and potential mitigation strategies provides a roadmap for protecting against this looming cyber danger.