Secure Computing CEO McNulty Malware Industry Drivers
Secure computing ceo mcnulty what drives the malware industry – Secure Computing CEO McNulty: What drives the malware industry? This insightful exploration delves into the motivations, methods, and economic forces behind the escalating threat of malicious software. We’ll examine the CEO’s perspective, the impact on businesses, and crucial countermeasures to protect against this evolving digital danger. This is more than just a technical discussion; it’s a look at the human element behind cybercrime.
From the historical context of secure computing to the latest advancements in malware, this deep dive offers a comprehensive overview. We’ll analyze the business models, supply chains, and technical factors that sustain the malware industry. The CEO’s perspective will shed light on the evolving nature of cyber threats and the crucial role secure computing plays in today’s business landscape.
Introduction to Secure Computing
Secure computing is the practice of ensuring confidentiality, integrity, and availability of digital information and systems. In today’s interconnected world, where nearly every aspect of life relies on digital platforms, secure computing is paramount. From protecting sensitive financial data to safeguarding critical infrastructure, robust security measures are essential to mitigate risks and maintain trust in digital interactions.The core tenets of secure computing encompass a multifaceted approach.
It involves not only safeguarding data but also ensuring the security of the systems that manage and process that data. Furthermore, user authentication and access control play a crucial role in preventing unauthorized access and misuse. A strong security posture requires a comprehensive strategy that addresses these elements in a coordinated manner.
Role of a CEO in Establishing a Secure Computing Environment
The CEO plays a pivotal role in establishing a secure computing environment within an organization. They are responsible for setting the tone and establishing the necessary policies and procedures to ensure that all employees understand and adhere to security protocols. This includes implementing robust security training programs and fostering a culture of security awareness. Effective leadership commitment translates to resource allocation, prioritization, and the development of a comprehensive security strategy.
Aspects of Secure Computing
Secure computing encompasses several critical aspects. Data protection involves safeguarding sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. System security focuses on protecting the hardware and software components of the computing infrastructure from malicious attacks. User authentication is the process of verifying the identity of a user attempting to access a system or resource.
These three aspects are interconnected and essential for achieving a robust security posture.
Historical Context of Secure Computing
The need for secure computing has evolved alongside the development of computing technologies. Early computing systems had limited security measures, but as the reliance on digital systems grew, the need for more sophisticated security mechanisms became apparent. The emergence of the internet and the rise of cyber threats have further accelerated the evolution of secure computing, leading to the development of advanced encryption techniques, intrusion detection systems, and security information and event management (SIEM) solutions.
Security Threats and Their Impact
| Security Threat | Potential Impact on Organizations |
|---|---|
| Malware (viruses, worms, Trojans) | Data breaches, system disruptions, financial losses, reputational damage. |
| Phishing attacks | Compromised accounts, sensitive data theft, financial fraud, operational disruptions. |
| Denial-of-service (DoS) attacks | System unavailability, loss of revenue, reputational damage, disruption of critical services. |
| Social engineering | Data breaches, unauthorized access, financial losses, operational disruptions, reputational damage. |
| Insider threats | Data breaches, system compromises, financial losses, reputational damage. |
Understanding the Malware Industry
The malware industry, a shadowy realm of illicit activity, thrives on exploiting vulnerabilities in software and systems. Motivated by financial gain, malicious actors employ sophisticated techniques to infiltrate and compromise networks, often with devastating consequences. Understanding the intricate dynamics of this industry is crucial for developing robust security measures and mitigating the risks associated with cyberattacks.
Motivations and Incentives
Malicious actors are driven by a complex interplay of motivations, ranging from financial gain to political or ideological agendas. Financial incentives often take precedence, fueling the development and distribution of malware for profit. This includes extortion through ransomware, theft of sensitive data for sale on the dark web, or the generation of revenue through fraudulent advertising schemes. Beyond financial gain, some actors are motivated by a desire to disrupt operations, damage reputations, or achieve political objectives.
The perceived anonymity and relative ease of access to resources often embolden malicious actors, contributing to the persistence of this criminal enterprise.
Business Models
Malware developers utilize various business models, each tailored to exploit specific vulnerabilities and target specific user groups. Ransomware, a particularly prevalent business model, involves encrypting a victim’s data and demanding a ransom for its release. Spyware, designed to surreptitiously collect sensitive information like login credentials or financial details, often operates on a subscription or pay-per-use basis. Adware, while not as directly malicious as ransomware or spyware, generates revenue by displaying unwanted advertisements to the user, often through bundling with legitimate software.
Supply Chains and Networks
The malware industry relies on intricate supply chains and networks to facilitate the development, distribution, and support of malicious software. These networks often involve a division of labor, with specialized individuals or groups handling different stages of the process. This includes malware developers, distributors, marketers, and support staff, who often operate in different locations, obfuscating their identities and making attribution difficult.
The use of proxy servers, encrypted communication channels, and virtual private networks further masks the true nature of these interactions.
Distribution Methods, Secure computing ceo mcnulty what drives the malware industry
Malware is distributed through a variety of channels, exploiting weaknesses in human behavior and technological systems. Phishing emails, masquerading as legitimate communications, lure victims into downloading malicious attachments or clicking on harmful links. Malicious software downloads often masquerade as legitimate software or updates, tricking users into installing harmful code. Exploit kits, pre-packaged tools for exploiting vulnerabilities in software, are frequently employed to automate the infection process.
The accessibility and sophistication of these methods allow malicious actors to reach a broad range of targets.
McNulty’s insights into the malware industry are fascinating, but understanding the why behind its relentless evolution requires looking beyond just the financial incentives. Researchers are developing context-specific software languages here , which could potentially revolutionize how we approach security vulnerabilities. Ultimately, these advancements will be crucial in combating the sophisticated and ever-evolving threats highlighted by McNulty.
Malware Type Comparison
| Malware Type | Characteristics | Objectives |
|---|---|---|
| Ransomware | Encrypts victim’s data; demands ransom for decryption | Financial gain through extortion |
| Spyware | Collects sensitive information; often targeted at specific individuals or organizations | Data theft, espionage, or identity theft |
| Adware | Displays unwanted advertisements; often bundled with legitimate software | Revenue generation through advertising |
Factors Driving the Malware Industry
The malware industry, a shadowy realm of illicit activity, thrives on a complex interplay of economic incentives, technological advancements, and vulnerabilities in software and systems. Understanding these driving forces is crucial for developing effective defense strategies and mitigating the ever-present threat. The industry’s resilience stems from a potent combination of motivations, constantly adapting to exploit weaknesses in security protocols.The malware industry, a sophisticated and evolving criminal enterprise, is not a static entity.
It adapts and refines its techniques to maximize profitability and minimize risk. This adaptation is fueled by the relentless pursuit of financial gain and the continuous development of sophisticated attack methods.
Economic Factors Fueling Growth
The malware industry operates on a business model driven by financial gain. Cybercriminals seek to monetize their malicious software through various methods, including ransomware attacks, data breaches, and the deployment of spyware for identity theft. The potential for high returns, combined with the relative ease of entry into the market (compared to traditional criminal activities), attracts individuals and groups seeking quick profits.
This economic incentive creates a significant motivator for continued innovation and expansion within the malware industry. The industry’s structure resembles that of a supply chain, with various actors specializing in different stages, such as malware development, distribution, and support. This organized approach allows for specialization and efficiency, enhancing the overall effectiveness of the operation.
Technical Advancements Empowering Malware Creation and Distribution
Technological advancements, particularly in areas like artificial intelligence (AI) and machine learning (ML), have significantly empowered malware creation and distribution. AI-powered tools automate the process of generating malicious code, making it faster and more efficient for attackers. These tools can adapt to evolving security measures, rendering traditional security solutions less effective. Furthermore, the increasing sophistication of social engineering techniques, combined with the proliferation of sophisticated malware, poses a significant threat.
The ease of access to tools and resources required for malware creation, combined with the anonymity afforded by the internet, further exacerbates the issue.
Vulnerabilities in Software and Systems: Facilitating Malware Attacks
Software and system vulnerabilities are crucial pathways for malware attacks. These vulnerabilities, often stemming from programming errors or design flaws, can be exploited by attackers to gain unauthorized access to systems and data. The constant evolution of software and systems necessitates a proactive approach to vulnerability management. This constant cycle of patching and updating is vital in preventing successful exploits.
The lack of adequate security measures in many systems leaves them exposed to malicious actors, creating a critical opportunity for malicious actors to gain access and control.
Social and Political Factors Contributing to Demand
Social and political factors also contribute to the demand for malicious software. Political motivations, such as state-sponsored attacks, can fuel the development and deployment of advanced malware. Additionally, the prevalence of online crime, including financial fraud and identity theft, creates a market for malware designed to target individuals and organizations. Social factors, such as a lack of awareness regarding online security and the perception of limited consequences for criminal activities, also play a significant role.
Vulnerability Types and Associated Risks
| Vulnerability Type | Description | Associated Risk |
|---|---|---|
| SQL Injection | Exploiting vulnerabilities in SQL databases to execute malicious code. | Data breaches, unauthorized access, and system compromise. |
| Cross-Site Scripting (XSS) | Injecting malicious scripts into websites to steal user data or perform malicious actions. | Session hijacking, data theft, and website defacement. |
| Cross-Site Request Forgery (CSRF) | Tricking users into performing unwanted actions on a website. | Unauthorized actions, data breaches, and financial fraud. |
| Buffer Overflow | Overfilling a buffer in memory, allowing attackers to execute arbitrary code. | System compromise, data breaches, and denial-of-service attacks. |
CEO McNulty’s Perspective
CEO McNulty brings a wealth of experience to Secure Computing, having spent over two decades navigating the complex landscape of cybersecurity threats. His deep understanding of malware development and the evolving tactics of cybercriminals provides invaluable insight into the challenges facing businesses today. His perspective is shaped not just by theoretical knowledge, but by direct experience in the field.McNulty’s perspective on the malware industry is one of profound concern, recognizing the escalating sophistication and destructive potential of malicious software.
He emphasizes the need for proactive and robust security measures to protect against these threats. His insights highlight the urgent need for businesses to adapt to the ever-changing cyber landscape, understanding that security is not a one-time investment but an ongoing commitment.
CEO McNulty’s Background and Experience
McNulty’s career began with a focus on network security, working in various roles at a major telecommunications company. He gained significant experience in threat detection, vulnerability analysis, and incident response. His transition to a cybersecurity leadership position involved overseeing the development and implementation of security policies and procedures, managing teams, and establishing a culture of proactive security. This experience has given him a comprehensive understanding of the challenges and opportunities in the modern cybersecurity arena.
His experience encompasses everything from the technical aspects of security to the strategic implications of cyber threats.
McNulty’s Perspective on Malware Threats
McNulty views the malware industry as a highly organized and sophisticated criminal enterprise. He highlights the constant evolution of malware techniques, noting that cybercriminals are always seeking new ways to exploit vulnerabilities. He stresses that the sophistication of modern malware is reaching a point where even advanced security systems can be compromised. This necessitates continuous adaptation and innovation in security strategies.
The financial incentives behind malware development are also significant, driving the relentless pursuit of new attack vectors.
McNulty’s Insights on Secure Computing Importance
In today’s interconnected world, secure computing is no longer a luxury but a necessity for businesses of all sizes. McNulty emphasizes the critical role of secure computing in protecting sensitive data, maintaining operational continuity, and preserving a company’s reputation. He sees secure computing as a foundation for business success in the digital age, enabling businesses to confidently embrace technology and innovation.
Loss of data, system downtime, and reputational damage can have severe consequences, underscoring the importance of proactive security measures.
McNulty’s Views on Combating the Malware Industry
Combating the malware industry requires a multi-faceted approach. McNulty stresses the importance of collaboration among businesses, security researchers, and law enforcement agencies. He believes that sharing threat intelligence and best practices is crucial in effectively countering the spread of malicious software.
- International Cooperation: Effective collaboration between nations is essential to combatting the global nature of the malware industry. This involves information sharing and joint investigations, enabling law enforcement to track down and prosecute cybercriminals operating across borders.
- Proactive Security Measures: McNulty highlights the need for organizations to implement robust security measures that extend beyond traditional firewalls and antivirus software. This includes proactive threat hunting, vulnerability management, and regular security audits.
- Employee Training: Human error remains a significant factor in cyberattacks. McNulty stresses the importance of employee training programs to educate staff on identifying phishing attempts, social engineering tactics, and other common attack vectors. This can be a significant line of defense against malware.
Key Takeaways from McNulty’s Perspective
McNulty’s perspective provides valuable insights into the complexities of combating the malware industry. The following table summarizes the key takeaways:
| Area of Focus | Key Takeaway |
|---|---|
| International Cooperation | Collaborative efforts between nations are vital to tracking and prosecuting cybercriminals. |
| Proactive Security Measures | Implementing robust security measures beyond traditional antivirus software is crucial. |
| Employee Training | Educating employees about security threats and best practices is essential. |
Impact on Businesses: Secure Computing Ceo Mcnulty What Drives The Malware Industry

The malware industry’s relentless pursuit of profit has devastating consequences for businesses across all sectors. From the smallest startups to the largest corporations, the potential for financial and operational disruption is significant. Understanding the various ways malware attacks inflict harm is crucial for developing robust security strategies and mitigating the risks.
McNulty, CEO of Secure Computing, recently highlighted the lucrative nature of the malware industry. It’s a fascinating aspect of cybercrime, but the underlying motivation often boils down to pure profit. This echoes the potential for profit in other emerging technologies, like the use of nanotechnology in various applications. For example, companies are actively exploring how to turn nanotech into profit, a field with the potential for both immense innovation and significant financial gain.
Ultimately, the core driver behind the malware industry, as pointed out by McNulty, remains the relentless pursuit of financial gain.
Financial Loss
Malware attacks inflict significant direct and indirect financial costs on businesses. Direct costs include the expenses of incident response, data recovery, and the cost of patching and upgrading security systems. Indirect costs, often more insidious, stem from lost productivity, reputational damage, and potential legal liabilities. These hidden costs can quickly escalate beyond the initial attack’s apparent financial impact.
- Direct Costs: These encompass the immediate financial burden associated with the attack. This includes the expenses for incident response teams, data recovery services, and the cost of upgrading security infrastructure to prevent future attacks. For example, a company might spend tens of thousands of dollars to restore compromised systems and recover lost data. The cost of lost revenue during downtime also falls under direct costs.
- Indirect Costs: Indirect costs are often harder to quantify but can significantly impact a business’s bottom line. These costs include lost productivity due to employees’ inability to work, disruption of supply chains, and the cost of complying with regulatory requirements following a breach. Consider a ransomware attack that halts production for several days; the lost revenue and the cost of restarting operations represent substantial indirect costs.
Operational Disruption
Malware attacks can severely disrupt business operations, leading to significant productivity losses and service interruptions. These disruptions often stem from data breaches, system compromises, or denial-of-service attacks.
- Data Breaches: Data breaches can expose sensitive customer information, leading to regulatory fines and reputational damage. They can also disrupt operations if crucial data is unavailable. For instance, a medical practice compromised by malware could lose access to patient records, halting treatment and impacting patient care.
- System Compromises: Malware can infiltrate and compromise critical business systems, disrupting workflows and hindering productivity. This can include crippling supply chains, halting online sales, and obstructing communication channels. An example is a manufacturing facility where malware disables production equipment, resulting in significant delays and loss of production.
- Denial-of-Service Attacks: These attacks flood systems with traffic, preventing legitimate users from accessing them. This can cause significant disruptions to online services, impacting e-commerce operations, customer support, and overall productivity. Imagine an online retailer experiencing a denial-of-service attack, preventing customers from purchasing products and incurring lost revenue.
Reputational Damage
Malware incidents can severely damage a company’s reputation, impacting its brand image and customer trust. This damage can be long-lasting and difficult to repair.
- Loss of Customer Trust: When a company experiences a malware attack, it can lose the trust of its customers, particularly if sensitive data is compromised. This can lead to a decline in sales, as customers might be hesitant to do business with a company that has demonstrated vulnerability.
- Damage to Brand Image: Malware incidents can significantly tarnish a company’s brand image, making it difficult to attract and retain customers. Negative publicity surrounding the incident can create a lasting perception of unreliability.
Legal and Regulatory Implications
Malware attacks often trigger legal and regulatory implications, including potential lawsuits, fines, and compliance requirements.
McNulty’s insights into the malware industry are fascinating, but the reality is that everyday tools like imlogic releases free im and p2p blocking software are crucial for personal protection. These simple tools highlight how crucial it is to block potential vectors for malware, ultimately aligning with McNulty’s concerns about the industry’s driving forces. So, while the big picture is important, simple steps can make a big difference in the fight against malware.
- Legal Liabilities: Businesses may face legal action from affected customers, partners, or regulatory bodies if a malware attack results in damages or breaches of privacy. This includes data protection regulations like GDPR, CCPA, and others.
- Regulatory Fines: Non-compliance with data protection regulations can lead to substantial fines, potentially crippling a company’s finances. These fines are often linked to the severity and duration of the breach.
Impact Summary Table
| Category | Description | Example |
|---|---|---|
| Financial Loss | Direct and indirect costs associated with the attack. | Lost revenue, incident response costs, data recovery, legal fees. |
| Operational Disruption | Interruption of business processes and workflows. | Data breaches, system compromises, denial-of-service attacks. |
| Reputational Damage | Loss of customer trust and damage to brand image. | Negative publicity, loss of sales, difficulty attracting new customers. |
| Legal Issues | Legal liabilities and regulatory fines. | Lawsuits, penalties for non-compliance with data protection regulations. |
Countermeasures and Mitigation Strategies

Protecting against malware requires a multifaceted approach that goes beyond simple reactive measures. Proactive strategies, robust security measures, and a culture of cybersecurity awareness are crucial to minimize the risk of attacks and ensure business continuity. This proactive approach emphasizes preventative measures, incident response planning, and continuous improvement to build a resilient security posture.
Security Measures to Enhance Protection
A layered security approach is essential to thwart malware attacks effectively. This entails implementing various security controls at different points within the IT infrastructure. Firewalls, intrusion detection systems, and anti-malware software form the core of this defense strategy.
- Firewalls: Firewalls act as gatekeepers, controlling network traffic and preventing unauthorized access. They filter incoming and outgoing data, blocking malicious traffic and known malware signatures. A robust firewall configuration, including the use of next-generation firewalls (NGFWs), can significantly reduce the risk of malware infections. Example: A properly configured firewall can prevent a malicious actor from gaining access to a network through an open port.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can either block or alert administrators to suspicious patterns. IDS/IPS continuously learn and adapt to emerging threats, providing real-time protection against known and unknown malware.
- Anti-malware Software: Anti-malware solutions, including antivirus and anti-spyware software, play a critical role in detecting and removing existing malware. These programs should be regularly updated to ensure they can recognize the latest threats. These programs often use heuristics and signature-based detection to identify malware.
Importance of Cybersecurity Awareness Training
Employee training is a critical component of a robust security posture. Educating employees about the various types of malware, common attack vectors, and safe computing practices empowers them to be the first line of defense. This training is not a one-time event but a continuous process to address emerging threats and best practices.
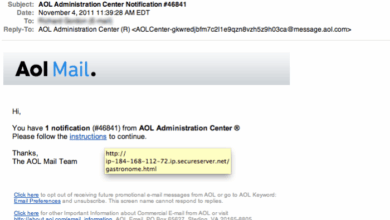
- Recognizing Phishing Attempts: Phishing emails and fraudulent websites are common attack vectors. Training equips employees to identify these attempts, which often exploit human error. This includes recognizing suspicious email addresses, hyperlinks, and attachments. Example: A phishing email claiming to be from a bank can trick employees into providing sensitive information, leading to data breaches.
- Safe Password Practices: Strong, unique passwords are essential to protect accounts from unauthorized access. Training should cover the creation and management of strong passwords, as well as the risks associated with weak passwords.
- Safe Browsing Practices: Employees need to be aware of the risks associated with visiting unverified websites or downloading files from untrusted sources. Training should emphasize the importance of verifying website security certificates and avoiding clicking on suspicious links or attachments. Example: Downloading a seemingly harmless file from an unknown source can expose the system to a malware infection.
Role of Incident Response Plans
A well-defined incident response plan is critical for effectively addressing malware incidents. It Artikels the steps to take in the event of a breach, including containment, eradication, recovery, and post-incident analysis. This planning helps to minimize the impact of a security incident and facilitates a swift and coordinated response.
- Containment: The plan should Artikel how to isolate infected systems and prevent the spread of malware to other parts of the network. Example: Immediately disconnecting a compromised machine from the network can contain the malware’s spread.
- Eradication: Procedures should detail how to remove the malware from infected systems without causing further damage. Example: Using anti-malware tools or employing specialized removal techniques can effectively eliminate malware.
- Recovery: The plan should Artikel the steps to restore systems and data to a pre-incident state. Example: Restoring from backups ensures the recovery of lost data.
- Post-Incident Analysis: The plan should emphasize the importance of analyzing the incident to identify weaknesses in the security posture and implement preventative measures to avoid future incidents. Example: Examining logs and network traffic can pinpoint vulnerabilities that attackers exploited.
Security Measures Effectiveness Table
| Security Measure | Effectiveness in Preventing Malware Attacks |
|---|---|
| Firewall | High – Blocks unauthorized access and malicious traffic |
| IDS/IPS | Medium to High – Detects and responds to suspicious activity |
| Anti-malware Software | Medium to High – Detects and removes existing malware |
| Employee Training | High – Educates employees to recognize and avoid threats |
| Incident Response Plan | High – Facilitates a coordinated response to minimize damage |
Future Trends in Secure Computing
The digital landscape is constantly evolving, and with it, the threats to our systems. Staying ahead of the curve requires a proactive approach to secure computing, anticipating emerging technologies and adapting to new attack vectors. This section explores the future of secure computing, highlighting the potential of AI, blockchain, and the need for constant adaptation to evolving threats.
Emerging Technologies and Their Impact
Advancements in technology are simultaneously creating new opportunities and new vulnerabilities. Quantum computing, for instance, presents a significant threat to current encryption methods. The increased processing power of these systems could break widely used encryption algorithms, potentially rendering sensitive data vulnerable. This necessitates the development of post-quantum cryptography, a field focused on creating algorithms resistant to attacks from quantum computers.
Other emerging technologies, like the Internet of Things (IoT), introduce a vast network of interconnected devices, increasing the attack surface. This requires innovative security measures to protect these devices and the data they handle.
Artificial Intelligence and Machine Learning in Malware Combat
AI and machine learning are proving to be powerful tools in the fight against malware. AI-powered systems can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, enabling quicker detection and response to emerging threats. Machine learning algorithms can also be trained to identify and classify new malware variants, adapting to evolving attack techniques in real time.
This proactive approach can significantly reduce the impact of cyberattacks. For example, Google’s Project Zero uses machine learning to detect vulnerabilities in software, helping to patch them before they can be exploited.
Blockchain Technology for Enhanced Security
Blockchain technology, known for its decentralized and immutable nature, can enhance security in several ways. By using blockchain for secure transactions and data storage, the risk of data breaches and tampering can be significantly reduced. Smart contracts, self-executing contracts with the terms of the agreement directly written into lines of code, can automate security processes and streamline compliance.
For example, supply chain security can be improved by using blockchain to track the movement of goods, ensuring authenticity and preventing counterfeiting.
Evolving Cyber Threats and Continuous Adaptation
The nature of cyber threats is constantly evolving, with attackers employing increasingly sophisticated techniques. The rise of ransomware attacks, targeted phishing campaigns, and the use of social engineering tactics highlight the need for continuous adaptation and improvement in security measures. Staying ahead of these threats requires a proactive and adaptive approach to cybersecurity, encompassing both technical solutions and employee training.
Companies must constantly update their security protocols to counter new attack vectors.
Potential Future Trends in Secure Computing
| Future Trend | Benefits | Challenges |
|---|---|---|
| Post-Quantum Cryptography | Provides encryption resistant to quantum computer attacks, ensuring data security in the future. | Requires significant investment in research and development, and the transition to new algorithms could be complex and costly. |
| AI-Powered Threat Detection | Enables faster identification and response to emerging threats, reducing downtime and data breaches. | Requires large datasets for training and ongoing maintenance to stay ahead of evolving attack techniques. |
| Blockchain for Data Integrity | Increases data security by preventing tampering and providing transparency in transactions. | Requires widespread adoption and standardization to maximize benefits, and issues of scalability can emerge. |
| Cybersecurity as a Service (CaaS) | Provides businesses with access to advanced security tools and expertise without significant upfront investment. | Requires trust in third-party providers and the management of security data. |
| Zero Trust Security Architecture | Enhances security by verifying every user and device before granting access, reducing the risk of breaches. | Implementing zero trust can be complex, requiring significant changes to existing infrastructure and processes. |
Ultimate Conclusion
In conclusion, the malware industry is a complex ecosystem driven by a mix of economic incentives, technical innovation, and social factors. CEO McNulty’s insights highlight the critical need for proactive security measures and a forward-thinking approach to secure computing. Businesses must understand the evolving nature of these threats and implement robust strategies to protect their operations, reputation, and financial well-being.
The future of secure computing hinges on understanding and adapting to these evolving challenges.