Email Security The Human Factor
Security with e mail the human factor – Security with email, the human factor, is a critical aspect of online safety. This blog post explores the vulnerabilities inherent in email security, focusing on the role of human error. We’ll delve into common mistakes, the psychology behind phishing scams, and the importance of user education and awareness in combating these threats. From recognizing suspicious emails to implementing robust security policies, we’ll provide practical strategies for bolstering your email security posture.
This deep dive into the human element of email security will equip you with the knowledge and tools needed to protect yourself and your organization from potential attacks. We’ll analyze various types of phishing attempts, examine common user errors, and Artikel effective countermeasures. The importance of a strong security culture and the role of multi-factor authentication (MFA) will also be highlighted.
Email Security Risks: Security With E Mail The Human Factor
Email, a ubiquitous communication tool, unfortunately, presents a significant vulnerability in the digital landscape. Its ease of use and wide adoption make it a prime target for malicious actors seeking to exploit human weaknesses and gain unauthorized access to sensitive information. Understanding the various security risks associated with email is crucial for individuals and organizations to safeguard their data and maintain a secure online presence.
Common Email Security Vulnerabilities
Email security vulnerabilities encompass a range of weaknesses that malicious actors leverage to compromise systems and gain access to sensitive information. These vulnerabilities often exploit the human element, relying on social engineering techniques to trick recipients into performing actions that compromise security. Common vulnerabilities include weak passwords, insufficient security protocols, and outdated software. These vulnerabilities can be exploited in numerous ways, such as through phishing attacks, malware distribution, and the compromise of email accounts.
Email Phishing Attacks
Phishing attacks, a common email security risk, are characterized by fraudulent communications that attempt to trick recipients into revealing sensitive information, such as usernames, passwords, credit card details, or social security numbers. These attacks often mimic legitimate organizations or individuals to gain the recipient’s trust. Different types of phishing attacks exist, each with unique characteristics.
- Spear Phishing: Targeted attacks against specific individuals or organizations, often leveraging personal information to appear more legitimate. These attacks are highly personalized and tailored to the victim, making them more difficult to detect.
- Whaling: A sophisticated phishing attack targeting high-profile individuals, such as CEOs or executives, to gain access to sensitive corporate data. These attacks often mimic legitimate business communications.
- Clone Phishing: Involves creating a nearly identical copy of a legitimate email message, usually from a trusted sender, to deceive the recipient into clicking a malicious link or opening a harmful attachment.
Recognizing Suspicious Emails and Attachments
Recognizing suspicious emails and attachments is crucial to prevent falling victim to phishing attacks. Look for inconsistencies in the email’s content, sender’s address, or request. Pay close attention to grammar, spelling, and punctuation errors.
- Unexpected Requests: Be wary of emails requesting urgent action or personal information. Legitimate organizations typically do not ask for sensitive data via email.
- Suspicious Links and Attachments: Hover over links to check their destination before clicking. Avoid opening attachments from unknown senders. Malicious attachments can contain malware or viruses.
- Generic Greetings: Emails with generic greetings or addresses (“Dear User”) should raise suspicion. Legitimate organizations typically address recipients by name.
Social Engineering Tactics in Email Attacks
Social engineering tactics in email attacks exploit human psychology to manipulate individuals into performing actions that compromise security. These tactics aim to create a sense of urgency, trust, or fear to trick the recipient.
Email security often hinges on the human element, making it surprisingly vulnerable. Recent discussions about the state of telephony, like in voip inc s rodriguez discusses state of telephony , highlight the importance of secure communication protocols. Ultimately, user training and awareness remain critical components in bolstering email security.
- Urgency: Creating a sense of urgency by implying that the recipient needs to take immediate action. For example, a phishing email might claim that an account will be suspended unless a user updates their password immediately.
- Authority: Impersonating a legitimate authority figure, such as a bank or government agency, to instill trust and encourage compliance.
- Scarcity: Creating a sense of scarcity, implying that a limited-time offer or opportunity is available. This is often used to encourage immediate action without careful consideration.
Email Security Threats Table
| Threat | Impact | Preventative Measures | Example |
|---|---|---|---|
| Phishing | Data breaches, financial loss, reputational damage | Verify sender’s identity, be cautious of suspicious links and attachments, use strong passwords, report suspicious emails | Receiving an email claiming to be from a bank asking for account details |
| Malware | System compromise, data theft, operational disruption | Use antivirus software, update software regularly, be cautious of downloading files, avoid suspicious links | Opening an email attachment containing a virus |
| Spear Phishing | Compromised sensitive information, financial loss | Verify sender’s identity, be cautious of suspicious requests, educate employees about social engineering techniques, use multi-factor authentication | A tailored email from a company executive requesting sensitive information |
| Spam | Email overload, decreased productivity, potential malware | Use spam filters, report spam emails, do not respond to unsolicited messages | Receiving numerous promotional emails from unknown senders |
Human Error in Email Security
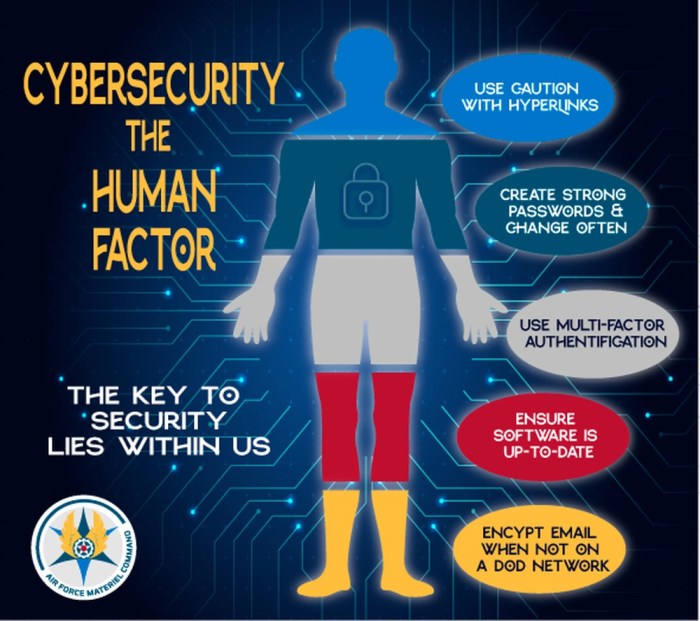
Email security relies heavily on user vigilance. While robust technical measures are essential, human error often represents a significant vulnerability. Users, inadvertently or due to various psychological factors, frequently compromise security protocols. Understanding these errors and the underlying psychology is crucial for developing effective countermeasures.The human element is often the weakest link in email security. This vulnerability stems from a combination of cognitive biases, lack of awareness, and sometimes, even malicious intent.
Addressing this issue requires a multifaceted approach that goes beyond simply providing technical solutions.
Common User Mistakes in Email Security
User errors in email security range from simple oversights to more complex misjudgments. These errors often exploit inherent human tendencies, such as trust, curiosity, and a desire to avoid inconveniences. Many users lack a deep understanding of email security risks and fail to recognize subtle signs of phishing attempts.
- Failing to scrutinize sender addresses and email content: Users often overlook suspicious sender addresses, typos in email addresses, or inconsistencies in the email’s content. This lack of critical evaluation can lead to the opening of malicious attachments or clicking on harmful links.
- Clicking on suspicious links: Users may be lured by enticing subject lines or the promise of valuable content. A simple click on a seemingly innocuous link can lead to malware infections or data breaches.
- Opening suspicious attachments: Users may unintentionally open malicious attachments masquerading as legitimate files. This can result in the installation of viruses, ransomware, or spyware on their systems.
- Ignoring security warnings: Users may ignore security warnings or pop-ups from their email clients or operating systems. This lack of attention to security alerts can expose them to security threats.
Psychology Behind Email Scams
Several psychological factors contribute to the effectiveness of email scams. Understanding these factors is crucial for developing targeted countermeasures. Scammers leverage human emotions, such as greed, fear, and a desire for immediate gratification.
- Social Engineering Tactics: Scammers often use social engineering tactics to manipulate users into revealing sensitive information. These tactics exploit human trust and vulnerability.
- Sense of Urgency: Many scams create a sense of urgency, pressuring users into making quick decisions without proper consideration. Examples include limited-time offers or threats of account suspension.
- Authority and Trust: Scammers may impersonate legitimate organizations or individuals in positions of authority to gain the user’s trust and encourage compliance.
Examples of User Security Errors
Numerous real-world examples demonstrate the impact of human error in email security.
- A user receives an email claiming to be from their bank, requesting account details. They provide the information without verifying the email’s authenticity.
- A user clicks on a link in an email that redirects them to a fake website that looks identical to their bank’s website. They enter their login credentials, unknowingly compromising their account.
- A user receives an email attachment purportedly containing a document. They open the attachment, unwittingly installing malware on their computer.
User Errors vs. Countermeasures
| User Error | Description | Effective Countermeasure | Rationale |
|---|---|---|---|
| Clicking on suspicious links | Users click on links in emails without verifying their authenticity. | Verify sender and content; hover over links before clicking. | Hovering and checking the link’s destination helps identify spoofing. |
| Opening suspicious attachments | Users open attachments without checking their source. | Verify sender and file type; use antivirus software. | Verification and antivirus scans can prevent malware infection. |
| Ignoring security warnings | Users disregard security warnings from email clients or systems. | Read and understand security alerts; report suspicious activity. | Understanding and responding to alerts enhances security awareness. |
| Trusting unsolicited emails | Users trust emails without verifying their source. | Verify sender authenticity; contact organizations directly. | Direct verification and contacting legitimate entities confirm email legitimacy. |
User Awareness and Training
User awareness is paramount in email security. Educating users about common threats and best practices is the first line of defense against sophisticated attacks. A well-trained user is less likely to fall victim to phishing scams and other email-borne threats. This proactive approach is far more cost-effective than reactive measures after a breach.
Effective Strategies for Educating Users
Effective user education programs should cover various aspects of email security. These programs should incorporate interactive elements and real-world examples to make the training engaging and memorable. The goal is not just to impart knowledge, but also to instill a security-conscious mindset. Training should be ongoing and updated regularly to reflect evolving threats.
Methods to Improve User Awareness of Phishing Techniques
Phishing attacks often rely on social engineering tactics to trick users into revealing sensitive information. To improve user awareness, training programs should highlight common phishing tactics, such as spoofing, urgency, and bait. Examples of phishing emails should be presented, with clear explanations of the deceptive techniques used. Users should be taught to recognize red flags in email communications, such as poor grammar, suspicious links, and unusual requests.
Interactive Training Modules
Interactive training modules significantly enhance user engagement and comprehension. These modules can include quizzes, simulations, and scenarios that put users in the shoes of potential victims. For instance, a module might present a phishing email and ask users to identify the red flags. Another module could simulate a compromised account and demonstrate the importance of strong passwords and two-factor authentication.
These interactive elements reinforce the learning process and make the training more impactful. Role-playing exercises can also be valuable in simulating real-world scenarios, strengthening user preparedness.
Email Security Tips for Users
Following these practical tips can significantly reduce the risk of email security breaches:
- Verify sender authenticity: Carefully scrutinize the sender’s email address and domain name for inconsistencies. Look for subtle clues that might indicate spoofing.
- Avoid suspicious links: Never click on links in emails from unknown senders. Hover over links to see the actual destination URL before clicking.
- Be wary of urgent requests: Emails demanding immediate action or containing threats often indicate phishing attempts. Verify the request through a separate, trusted channel.
- Report suspicious emails: Report any suspicious emails to the appropriate IT department or security team.
- Practice strong password management: Use unique, strong passwords for each account and consider using two-factor authentication whenever available.
Comparison of Email Security Training Methods
Different methods of training can have varying levels of effectiveness.
| Training Method | Description | Effectiveness | Considerations |
|---|---|---|---|
| Interactive Simulations | Mimicking real-world scenarios | High | Requires dedicated development and resources |
| Short Videos | Concise explanations of security threats | Moderate | May not cover complex topics adequately |
| Webinars | Live sessions with Q&A | High | Requires user availability and active participation |
| Email Newsletters | Periodic reminders of best practices | Low | Can be easily overlooked or ignored |
Email Security Policies and Procedures
Robust email security isn’t just about technology; it’s fundamentally about establishing clear policies and procedures that empower users to make informed decisions and effectively manage risks. A well-defined email security framework reduces vulnerabilities, minimizes the potential for data breaches, and fosters a culture of security awareness within the organization. A well-structured framework also ensures consistent response to threats and incidents.Clear policies and procedures provide a roadmap for employees, outlining acceptable email behavior and expectations for handling sensitive information.
This not only safeguards the organization’s data but also builds trust and confidence in the security measures in place.
Importance of Clear Email Security Policies
Email security policies are crucial for establishing a baseline of acceptable use, defining roles and responsibilities, and providing a framework for consistent action in case of security incidents. They provide a common understanding of the risks associated with email and the measures required to mitigate them. Without clear guidelines, employees may unknowingly compromise the organization’s security.
Comprehensive Email Security Guidelines
A comprehensive email security policy should encompass various aspects of email usage, including:
- Acceptable Use Policy (AUP): This policy Artikels acceptable and unacceptable email practices. It should specify guidelines for sending sensitive information, using company email for personal purposes, and the consequences for non-compliance.
- Password Management: Strong password policies are essential. Guidelines should mandate password complexity, frequency of changes, and the prohibition of sharing passwords.
- Attachment Handling: Policies should detail the protocols for opening attachments, particularly from unknown senders. Guidance on file types to avoid, and procedures for scanning attachments, are critical.
- External Communication: This section should Artikel guidelines for communicating with external parties via email, including the use of secure channels for sensitive data and the avoidance of publicly sharing confidential information.
Procedures for Handling Suspected Phishing Emails
Suspected phishing emails should be treated with extreme caution. Immediate action is critical to prevent potential harm.
Email security often hinges on the human element, and that’s where things can get tricky. Think about how a tightly integrated search tool like Microsoft toolbar tightly integrated with desktop search streamlines information access. That same principle applies to email; a user-friendly interface and intuitive security protocols are key to preventing accidental breaches. Users need to be able to navigate their inboxes with ease and recognize phishing attempts, which often depend on social engineering tactics.
Ultimately, email security boils down to educating and empowering the user.
- Do Not Click: Never click on links or open attachments from suspicious emails. Hovering over links can reveal the true destination URL.
- Report to IT: Immediately report suspected phishing attempts to the IT department or designated security team. Detailed descriptions of the email are essential.
- Verify Authenticity: If unsure about the email’s legitimacy, contact the sender through a known, verified channel (e.g., phone call). Never reply directly to the email.
Reporting and Investigating Email Security Incidents
Establishing clear channels and procedures for reporting and investigating email security incidents is paramount.
- Designated Reporting Channels: The organization should establish clear channels for reporting incidents, ensuring that employees understand how to report suspicious emails or other security breaches.
- Incident Response Plan: A comprehensive incident response plan is vital for managing security breaches. It should Artikel the steps to be taken when an incident occurs, including containment, eradication, recovery, and lessons learned.
- Investigation Procedures: The plan should detail how incidents will be investigated, including data collection, analysis, and reporting.
Best Practices for Email Security Policies and Procedures
| Category | Best Practice | Description | Example |
|---|---|---|---|
| Policy Scope | Comprehensive coverage | Policies should address various aspects of email use, from acceptable use to incident response. | A policy covering password management, attachment handling, and external communication. |
| User Awareness | Regular training | Train employees on identifying phishing attempts, safe email practices, and incident reporting procedures. | Regular webinars or online modules on email security. |
| Incident Response | Clear escalation paths | Establish clear communication channels and escalation procedures for reporting and handling email security incidents. | A dedicated email address for reporting incidents, with clear instructions on how to escalate issues. |
| Policy Enforcement | Regular review and update | Policies should be reviewed and updated periodically to reflect evolving threats and best practices. | Annual reviews of the email security policy and procedure document. |
Multi-Factor Authentication and Email Security
Multi-factor authentication (MFA) is a crucial layer of defense against email security breaches. It adds an extra layer of verification beyond a simple password, making it significantly harder for attackers to gain unauthorized access to email accounts, even if they manage to compromise a password. This enhanced security is essential in today’s digital landscape, where email is a primary communication and data exchange tool.MFA significantly strengthens email security by requiring multiple authentication factors.
This means an attacker needs not only the password but also another form of verification, making unauthorized access far more difficult. This additional hurdle substantially reduces the risk of successful attacks and protects sensitive information exchanged through emails.
Integration of MFA with Email Accounts
MFA integration with email accounts typically involves linking the account to a trusted device or application. This often involves a setup process that guides the user through the required steps to connect their email account with their chosen authentication method. Once configured, the user will be prompted for multiple authentication factors when logging in. This approach adds an additional security measure that significantly reduces the risk of unauthorized access to the account.
Examples of MFA Methods Applicable to Email Accounts
Several methods can be used for MFA for email accounts. These methods range from simple to complex, each with its own security strengths and weaknesses.
- One-time passwords (OTPs): OTPs are temporary codes sent to a registered mobile device or email address. These codes are valid for a short period, enhancing security against password-guessing attacks.
- Security keys: These physical devices, often small USB-like devices, generate unique codes. They provide a strong, hardware-based authentication method, effectively preventing unauthorized access.
- Biometrics: This method leverages unique biological traits, such as fingerprints or facial recognition, to verify the user’s identity. The technology is highly accurate and can be convenient for users, though potential concerns about privacy must be addressed.
Benefits and Challenges of Implementing MFA for Email Security
Implementing MFA offers numerous benefits for email security, but also presents some challenges.
- Enhanced Security: MFA significantly increases the security posture of email accounts by adding an additional layer of protection. This makes it substantially harder for attackers to gain unauthorized access.
- Reduced Risk of Phishing: By requiring more than just a password, MFA mitigates the risk of phishing attacks, as attackers need more than just stolen credentials to gain access.
- Improved Compliance: Many organizations require MFA for compliance reasons, such as industry regulations or internal policies. This is a crucial aspect for organizations handling sensitive data.
- User Experience Concerns: Users might find the extra steps involved in MFA cumbersome or inconvenient, especially if they’re not accustomed to multi-factor authentication.
- Technical Integration Challenges: Integrating MFA with existing email systems can be complex, requiring technical expertise and careful planning.
Comparison of MFA Methods
The following table compares various MFA methods based on their security strengths:
| Method | Security Strength | Ease of Use | Cost |
|---|---|---|---|
| One-time passwords (OTPs) | Good; relies on secure communication channels | Moderate; requires a device to receive the codes | Low; often integrated into existing systems |
| Security keys | High; hardware-based authentication | High; simple to use once configured | Medium; requires purchasing the device |
| Biometrics | High; based on unique biological traits | High; convenient for frequent users | High; often requires specialized infrastructure |
Email Encryption and Security
Email encryption is a crucial component of a robust email security strategy. It safeguards sensitive information transmitted through emails, protecting against unauthorized access and disclosure. By converting readable text into an unreadable format, encryption renders intercepted emails useless to malicious actors. This practice is paramount in today’s digital landscape where sensitive data, including financial transactions, personal information, and confidential business communications, frequently travels via email.
Email Encryption Methods
Various methods exist for encrypting emails, each with its own strengths and weaknesses. Understanding these different approaches is key to selecting the appropriate method for specific needs. Different levels of security and complexity are associated with these methods, allowing for tailored solutions.
- Symmetric-key encryption: This method uses the same secret key for both encryption and decryption. It’s relatively fast and efficient for large volumes of data. However, securely sharing the secret key between sender and recipient is a critical challenge.
- Asymmetric-key encryption: This method employs a pair of keys: a public key for encryption and a private key for decryption. Public keys can be freely shared, while private keys must remain confidential. This approach addresses the key distribution problem of symmetric encryption, making it suitable for secure communication over less secure channels.
- End-to-End Encryption (E2EE): This approach ensures that only the sender and recipient can access the content of an email. Intermediate parties, such as email providers, cannot decrypt the messages. This is particularly valuable for sensitive communication where complete confidentiality is paramount.
Effectiveness of Email Encryption Methods
The effectiveness of an email encryption method hinges on several factors. The security of the chosen encryption algorithm, the strength of the encryption keys, and the integrity of the key management system all contribute to its effectiveness. The complexity and computational resources required to break the encryption also play a crucial role.
- Algorithm strength: Robust encryption algorithms, like AES-256, are more resistant to cryptanalysis compared to weaker algorithms. This resistance directly impacts the level of security provided.
- Key management: Securely storing and managing encryption keys is critical. Compromised keys render the entire encryption process ineffective. This is a critical factor in securing sensitive data.
- User awareness: Users need to understand the encryption process and follow procedures correctly. Lack of user awareness can create vulnerabilities.
Email Encryption Tools and Technologies
Various tools and technologies are available to facilitate email encryption. These tools vary in complexity and features, catering to different needs and budgets.
- Microsoft Outlook: Provides built-in encryption capabilities for sending and receiving secure emails. The Outlook client supports encryption protocols for secure data exchange.
- Third-party encryption solutions: Several providers offer specialized email encryption solutions, often with additional features like secure file sharing and audit trails. These tools are commonly utilized by organizations handling sensitive data.
- S/MIME: A standard for securing email messages using public-key cryptography. S/MIME is a widely adopted standard, allowing for digital signatures and encryption.
Impact of Encryption on Reducing Email Security Risks
Email encryption significantly mitigates email security risks. By rendering intercepted emails unintelligible, encryption protects sensitive data from unauthorized access. It also prevents message tampering and ensures message integrity.
Email security often hinges on the human factor, making it a constant challenge. Vendors are now striving to automate WLAN deployment planning, which could significantly improve network security by streamlining configurations and reducing vulnerabilities. However, even with automated solutions, remembering the importance of employee training and awareness in email security remains paramount. Ultimately, a multi-pronged approach, including both technological advancements like those found in vendors striving to automate wlan deployment planning and robust human security protocols, is crucial for a truly effective security posture.
Comparison of Email Encryption Protocols
| Protocol | Advantages | Disadvantages | Use Cases |
|---|---|---|---|
| S/MIME | Widely supported, integrated into email clients | Can be complex to implement, requires certificate management | Secure internal communications, sensitive business documents |
| PGP/GPG | Strong encryption, open-source, versatile | Requires user configuration, potentially less user-friendly | Secure personal communication, sensitive personal data |
| TLS/SSL | Industry standard, widely supported | Does not offer end-to-end encryption, vulnerable to man-in-the-middle attacks if not implemented correctly | General secure email communication, secure webmail |
Security Culture and Email Practices
A strong security culture is paramount in mitigating email risks. It’s not just about implementing technical controls; it’s about fostering a mindset where employees actively prioritize security in their daily email interactions. This proactive approach reduces the likelihood of human error and strengthens the overall security posture.A security-conscious environment is built on shared understanding and consistent practice. It empowers employees to recognize and report suspicious emails, ultimately preventing potential breaches and data loss.
This culture of vigilance significantly reduces the impact of phishing attacks and other malicious activities.
Influence of Security Culture on Email Practices
A robust security culture deeply influences email practices by instilling a sense of responsibility and awareness among employees. Employees are more likely to adhere to established policies and procedures, scrutinize emails for suspicious elements, and report potentially harmful communications when they understand the importance of their role in maintaining security. This proactive approach, fostered by a strong security culture, minimizes the risks associated with human error in email security.
Fostering a Security-Conscious Environment
Building a security-conscious environment requires a multi-faceted approach that encompasses education, engagement, and reinforcement. Clear communication of policies and procedures, coupled with regular training sessions, equips employees with the knowledge and skills needed to identify and respond to potential threats.
Examples of Promoting Email Security Vigilance
Regular security awareness campaigns, simulated phishing exercises, and feedback mechanisms are crucial for maintaining vigilance. These activities help employees identify potential threats in real-world scenarios, reinforcing the importance of email security. Providing easily accessible resources, such as FAQs and contact information for security inquiries, can empower employees to seek assistance and address concerns promptly.
Role of Leadership in Shaping Email Security Awareness
Leadership plays a critical role in establishing and reinforcing a security-conscious culture. Leaders must demonstrate a commitment to email security by actively participating in training programs, promoting the importance of security awareness, and incorporating security into company communications and procedures. Their visible engagement creates a ripple effect, encouraging employees to take email security seriously.
Strategies to Build a Security-Conscious Email Culture
| Strategy | Implementation | Measurement | Example |
|---|---|---|---|
| Education and Training | Regular workshops, online modules, and simulated phishing exercises | Tracking completion rates, employee feedback, and improvement in phishing test results. | Develop a comprehensive training program on email security best practices, including how to identify phishing emails, and secure password management. |
| Policy Reinforcement | Clear communication of email security policies and procedures. | Monitor policy adherence through email analysis and incident reports. | Regularly update and disseminate email security policies, ensuring clarity and accessibility. |
| Incentivize Safe Practices | Reward employees for adhering to security protocols and reporting suspicious activities. | Track the number of reported incidents and the successful prevention of potential threats. | Implement a reward system for employees who consistently demonstrate vigilance and identify malicious emails. |
| Continuous Monitoring and Feedback | Regularly review email security practices and provide feedback to employees. | Gather employee feedback on security awareness training and policies, and address any identified weaknesses. | Establish a feedback mechanism for employees to report concerns or suggest improvements to email security protocols. |
Advanced Email Threat Protection
Advanced email security is no longer just about filtering spam and viruses. Today’s threat landscape demands sophisticated solutions capable of identifying and mitigating a wider range of attacks, including sophisticated phishing campaigns, zero-day exploits, and advanced malware disguised as legitimate emails. These advanced solutions often leverage cutting-edge technologies to stay ahead of evolving threats.Advanced email threat protection systems go beyond basic anti-spam and antivirus filters.
They employ a layered approach, combining multiple techniques to detect and block malicious emails before they reach inboxes. These systems analyze emails at various levels, including content, sender reputation, and user behavior, to identify potential threats.
Capabilities of Advanced Email Threat Protection Systems
Advanced email threat protection systems possess a diverse range of capabilities, significantly enhancing the overall security posture of an organization. These systems actively monitor email traffic, identifying and blocking potentially malicious content, thus safeguarding users from various email-borne threats. They leverage a multitude of techniques to achieve this. These include deep content analysis, machine learning-based threat detection, and real-time threat intelligence feeds.
Role of Machine Learning and AI in Email Security
Machine learning (ML) and artificial intelligence (AI) are transforming email security. These technologies enable systems to learn from past threats, identify patterns indicative of malicious activity, and adapt to new and evolving threats in real time. AI algorithms can analyze vast amounts of email data to identify subtle indicators of phishing attempts, malware, and other malicious activities. By identifying patterns in emails, AI-powered systems can automatically classify and categorize emails, improving accuracy and efficiency in email security.
Importance of Regular Updates to Email Security Solutions
The threat landscape is constantly evolving. Email security solutions must be regularly updated to stay ahead of new threats. Security vendors continuously release updates that incorporate new threat intelligence, enhance detection capabilities, and improve overall performance. Failure to keep email security solutions updated leaves organizations vulnerable to emerging threats, jeopardizing sensitive data and disrupting business operations. Regular updates are essential to maintain an effective security posture.
Advanced Email Threat Protection Features and Benefits, Security with e mail the human factor
Regularly updated email security solutions incorporate a variety of features that protect users and the organization from cyberattacks. Below is a table outlining some of these features and their benefits:
| Feature | Description | Benefit | Example |
|---|---|---|---|
| Deep Content Analysis | Examines the content of emails for malicious code, suspicious links, and harmful attachments. This involves scrutinizing the structure and content of the email for potentially malicious patterns and indicators. | Improved detection of sophisticated phishing attempts and malware disguised as legitimate emails. | Identifying malicious macros embedded in seemingly harmless documents. |
| Sender Reputation Analysis | Evaluates the sender’s reputation based on past interactions and known malicious activity. | Reduces the likelihood of receiving spam and phishing emails from known bad actors. | Blocking emails from IPs known to send spam. |
| User Behavior Analytics (UBA) | Identifies unusual user behavior that could indicate a compromised account or malicious activity. | Detects suspicious login attempts, unusual email sending patterns, or unexpected file downloads, providing a layer of protection against insider threats. | Recognizing unusual email volume from a specific user. |
| Real-time Threat Intelligence | Provides up-to-date information on emerging threats and known malicious actors. | Enables rapid responses to new threats, keeping security solutions up-to-date. | Blocking emails from known phishing campaigns. |
Wrap-Up
In conclusion, email security hinges heavily on understanding the human factor. While advanced technologies and security solutions are crucial, ultimately, human awareness and vigilance play a vital role in preventing breaches. By educating users about phishing tactics, implementing robust policies, and fostering a security-conscious culture, organizations can significantly reduce their risk. The combination of technological safeguards and human understanding is essential to effective email security.