Study Suggests Mobile Malware Storm Brewing
Study suggests mobile malware storm brewing, highlighting a rapidly escalating threat to our interconnected world. Global mobile device usage is exploding, creating a massive attack surface for malicious actors. This rise in mobile malware isn’t just about stealing data; it’s about exploiting vulnerabilities in everyday apps and services, impacting individuals, businesses, and the entire digital ecosystem. Understanding the types, impacts, and mitigation strategies is crucial to protecting ourselves and our devices.
The study delves into various aspects of this emerging crisis, from identifying different types of mobile malware to analyzing emerging trends in their development. It explores the motivations behind this surge in malicious activity, examining the potential financial gains, privacy violations, and reputational damage associated with successful attacks. Furthermore, it investigates the technical intricacies of how these attacks work, providing insights into the infection mechanisms and propagation methods used by attackers.
The study also presents real-world case studies to illustrate the devastating impact of these attacks, emphasizing the importance of proactive security measures. Ultimately, the study aims to equip individuals and organizations with the knowledge and strategies needed to protect themselves against this growing threat.
Mobile Malware Storm Brewing
The mobile landscape is increasingly vulnerable to sophisticated malware attacks. Recent reports highlight a surge in malicious software targeting smartphones and tablets, with a particular focus on financial fraud and data theft. This “mobile malware storm” is not a new phenomenon, but its scale and sophistication are escalating, demanding a serious response from both individual users and industry stakeholders.
The sheer volume of mobile devices in use globally amplifies the potential damage and impact of these attacks.
Recent studies are painting a grim picture of a potential mobile malware surge. While Dell is focusing on the future of home entertainment with their new initiatives, like dell delves deeper into home entertainment , it’s crucial to remember that this proactive approach to tech doesn’t diminish the growing threat of mobile malware. This surge could seriously impact users if left unchecked.
Scope of the Threat
The global prevalence of mobile devices has created a massive attack surface. Billions of smartphones and tablets are in use worldwide, making them a prime target for cybercriminals. This vast pool of potential victims provides ample opportunity for widespread infection. The interconnected nature of mobile ecosystems further exacerbates the threat. Malicious software can rapidly spread through social engineering tactics, exploiting vulnerabilities in apps and operating systems.
Motivations Behind the Rise
Several factors contribute to the growth of mobile malware. Financial gain is a primary driver, with criminals targeting banking apps, payment systems, and personal financial data. Data theft for identity fraud and extortion is another significant motivation. Furthermore, some actors utilize mobile malware for political or ideological reasons, launching attacks on specific groups or individuals. The relative ease of creating and deploying mobile malware, coupled with the anonymity afforded by the internet, also plays a crucial role in the rise of this threat.
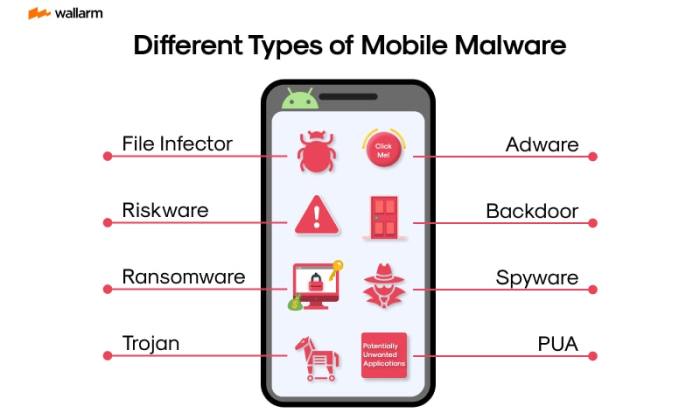
Types of Mobile Malware
A range of malicious software is impacting mobile devices. These include:
- Banking Trojans: These programs are designed to steal banking credentials, including usernames, passwords, and security codes, often through fraudulent apps or phishing messages.
- Ransomware: Ransomware attacks lock users out of their devices or encrypt their data, demanding payment for its release. Examples include attacks targeting mobile devices used for business or crucial personal data storage.
- Spyware: Spyware monitors users’ activities, stealing personal information, browsing history, and other sensitive data. This type of malware can often be hidden within seemingly legitimate applications.
- Adware: While not always malicious, adware can flood devices with unwanted advertisements, often leading to the installation of more harmful software. This can be a gateway for further attacks, exploiting vulnerabilities in the mobile device.
Mitigation Strategies
Protecting against mobile malware requires a multi-pronged approach. Security awareness training is crucial to educate users about potential threats and how to identify suspicious applications or links. Strong password management practices, coupled with multi-factor authentication, can bolster security against unauthorized access. Regular software updates are essential for patching known vulnerabilities in operating systems and applications. Using reputable app stores and exercising caution when downloading apps can help prevent the installation of malicious software.
Finally, robust antivirus software specifically designed for mobile devices can detect and remove malware.
Types of Mobile Malware
Mobile devices have become indispensable tools in our daily lives, making them prime targets for malicious actors. This vulnerability stems from the widespread adoption of smartphones and tablets, coupled with the inherent connectivity and processing power of these devices. Understanding the various types of mobile malware is crucial for individuals and organizations to effectively protect themselves from these threats.Mobile malware encompasses a wide range of malicious software designed to exploit vulnerabilities in mobile operating systems and applications.
These programs can range from relatively simple, data-stealing scripts to complex, sophisticated attacks capable of crippling entire systems. Understanding the different categories of mobile malware allows for a more targeted approach to security measures, enabling users and developers to better recognize and counter these threats.
Recent studies are sounding the alarm about a potential surge in mobile malware. It’s a worrying trend, especially considering the rapid advancements in technology. Meanwhile, IBM’s impressive new blade supercomputer for Spain, detailed in this article ( ibm builds blade supercomputer for spain ), highlights the ongoing push for powerful computing. This powerful technology could potentially help in the fight against this looming mobile malware storm, though the effectiveness remains to be seen.
Categories of Mobile Malware
Mobile malware can be broadly categorized into several types, each with its own set of characteristics and methods of attack. This classification helps in understanding the diverse nature of threats targeting mobile users.
- Trojan Horses: Trojan horses are disguised as legitimate applications, often downloaded from unofficial app stores or through malicious links. Once installed, they can grant attackers unauthorized access to the device, allowing them to steal data, control the device, or install additional malware. Examples include Trojans that steal banking credentials or install keyloggers to record user input.
- Ransomware: Ransomware is designed to encrypt sensitive data on a user’s device and demand a ransom for its release. These attacks often target financial data, personal photos, or other valuable files. Users are typically presented with a message demanding payment to restore access. One significant example is the widespread use of ransomware targeting mobile banking apps.
- Spyware: Spyware is designed to monitor a user’s activity without their knowledge or consent. It can track keystrokes, capture screenshots, record audio, or monitor browsing history. This information is then transmitted to the attackers, potentially revealing sensitive personal information or business secrets. An example of spyware would be apps that track user location without permission.
- Adware: Adware displays unwanted advertisements on a user’s device, often through pop-ups or banners. While sometimes not malicious in intent, adware can generate significant revenue for the attackers. Adware may also contain malicious components that can lead to more significant threats, such as the redirection of users to phishing websites.
Methods of Targeting Mobile Users
Malware developers employ various tactics to target mobile users, exploiting vulnerabilities in both the operating system and the user.
- Social Engineering: This technique leverages human psychology to manipulate users into installing malware. Malicious links or messages disguised as legitimate notifications or communications can trick users into downloading infected apps.
- Vulnerable Applications: Malware can exploit vulnerabilities in poorly secured or outdated mobile applications. Attackers often target popular apps to maximize their reach and potential for victims.
- Unofficial App Stores: Downloading applications from unofficial or third-party app stores increases the risk of encountering malicious software. These stores often lack proper security measures to vet applications before publication.
Comparison of Malware Types
| Malware Type | Description | Common Characteristics | Methods of Targeting |
|---|---|---|---|
| Trojan Horses | Disguised malicious software | Often downloaded from unofficial app stores, grant attackers unauthorized access | Social engineering, vulnerable applications |
| Ransomware | Encrypts data and demands a ransom | Targets sensitive data, presents a message demanding payment | Social engineering, exploiting vulnerabilities |
| Spyware | Monitors user activity without consent | Tracks keystrokes, captures screenshots, records audio, monitors browsing history | Vulnerable applications, disguised applications |
| Adware | Displays unwanted advertisements | Can generate revenue for attackers, may contain malicious components | Social engineering, vulnerable applications |
Impact and Consequences
The escalating threat of mobile malware necessitates a deeper understanding of its far-reaching consequences. Beyond the immediate inconvenience, these attacks can inflict substantial financial and reputational damage on individuals, businesses, and even national economies. The potential for data breaches and privacy violations is significant, highlighting the importance of proactive security measures.
Financial Losses
Mobile malware often targets financial accounts and payment systems. Sophisticated malware can steal sensitive information, such as credit card details, bank account numbers, and online banking credentials. This leads to substantial financial losses for victims, often resulting in fraudulent transactions and hefty charges. The theft of intellectual property and business data can also have severe financial repercussions, particularly for companies reliant on proprietary information.
In some cases, extortion attempts by malware operators can lead to significant payouts to avoid further damage. For example, ransomware attacks can cripple businesses, forcing them to pay hefty ransoms to regain access to their data.
Damage to User Privacy and Data Security
Malware compromises user privacy by stealing personal information, including contact lists, photos, and location data. This can lead to identity theft, harassment, and even extortion. The compromised data can be used for various malicious purposes, including spamming, phishing, and creating fraudulent accounts. The long-term impact on personal trust and security is substantial, often requiring significant time and effort to restore faith in online systems.
Moreover, the security breaches can expose sensitive personal information to malicious actors, leading to potential identity theft or financial fraud.
Impact on Businesses and Organizations
Mobile malware attacks can have a devastating impact on businesses and organizations of all sizes. Disruption to operations, loss of productivity, and damage to reputation are common consequences. Businesses can lose valuable customer data, leading to a decline in customer trust and potentially impacting future sales. The cost of recovery and remediation can be significant, impacting profitability and overall performance.
In addition, regulatory fines and legal liabilities can arise from data breaches caused by mobile malware infections. For instance, healthcare organizations that experience data breaches face substantial financial and reputational risks.
Consequences Table
| Affected Party | Potential Consequences |
|---|---|
| Individuals | Financial loss (fraudulent transactions, charges), identity theft, privacy violations (exposure of personal information), emotional distress, reputational damage, loss of trust in online systems |
| Businesses | Disruption of operations, loss of productivity, damage to reputation, loss of customer data, decline in customer trust, significant recovery and remediation costs, regulatory fines, legal liabilities, loss of intellectual property |
| Organizations (e.g., government agencies, healthcare providers) | Compromised sensitive data (patient records, financial information), disruption of essential services, reputational damage, loss of public trust, potential legal repercussions, substantial financial losses, potential national security implications |
Emerging Trends
The mobile malware landscape is constantly evolving, with developers employing increasingly sophisticated techniques to bypass security measures and exploit vulnerabilities. This necessitates a proactive approach to threat intelligence and security best practices to protect users and devices. This section will delve into emerging trends, including advanced evasion tactics, social engineering, and the rise of new malware types.
Sophisticated Evasion Techniques
Mobile malware developers are employing advanced techniques to evade detection by traditional security tools. These methods often involve obfuscation, polymorphism, and the use of dynamic code loading. Obfuscation makes the code harder to understand and analyze, while polymorphism allows the malware to change its structure and behavior over time. Dynamic code loading allows the malware to load code on-the-fly, making it difficult to identify and analyze the full threat profile.
Social Engineering in Mobile Malware Campaigns
Social engineering plays a crucial role in mobile malware campaigns, leveraging human psychology to trick users into installing malicious software. This involves sophisticated phishing techniques, using seemingly legitimate applications or messages to trick users into downloading malware. These campaigns frequently target specific demographics or interests, making them highly effective in deceiving users.
Examples of Emerging Malware Types
The emergence of new malware types poses a significant challenge to security professionals. These types often exploit newly discovered vulnerabilities or take advantage of emerging technologies. Here are some notable examples:
- Fileless Malware: This type of malware avoids traditional file systems, instead residing in memory or leveraging existing system tools. This makes it difficult to detect, as it doesn’t leave traces in typical file analysis tools. For example, malicious code might use system commands or scripting languages to carry out its activities, thereby avoiding traditional detection methods.
- Android Banking Trojans: These Trojans target banking apps, stealing credentials and financial data. They often use sophisticated techniques to evade detection, such as dynamically changing their code and behavior. These types of malware frequently leverage social engineering campaigns to trick users into providing their banking information.
- Ransomware-as-a-Service (RaaS): RaaS platforms enable less skilled actors to deploy ransomware attacks. These platforms often provide tools and infrastructure for launching attacks, enabling widespread dissemination of malicious software. This trend democratizes ransomware attacks, making them accessible to a wider range of malicious actors.
Advanced Persistent Threats (APTs) Targeting Mobile Devices
APT groups, known for their advanced capabilities and persistent attacks, are increasingly targeting mobile devices. These groups often focus on gaining access to sensitive information within corporate or government environments. They employ sophisticated tools and techniques to bypass security defenses and maintain persistent access to target devices. For instance, an APT group might use a combination of zero-day exploits and social engineering to gain initial access to a target device, then use malware to maintain persistence.
Conclusion
The constant evolution of mobile malware requires continuous adaptation and improvement of security measures. Proactive threat intelligence, robust security software, and user education are crucial in mitigating the risks associated with emerging malware trends.
Mitigation Strategies
The escalating threat of mobile malware demands proactive and robust security measures. Ignoring this growing danger leaves individuals and organizations vulnerable to significant financial and reputational damage. Effective mitigation strategies are crucial to protect against the ever-evolving landscape of mobile malware. This section delves into the importance of strong security practices, both for individual users and for developers of mobile applications.
Importance of Robust Mobile Security Measures
Robust mobile security measures are essential for mitigating the risk of malware infections. These measures encompass a layered approach, combining technological safeguards with user awareness and responsible application development practices. Failure to prioritize mobile security can result in significant data breaches, financial losses, and reputational harm. A comprehensive strategy is vital to combat the evolving tactics of malicious actors.
Effective Strategies to Protect Against Mobile Malware Infections
Protecting against mobile malware requires a multi-faceted approach. Regular software updates, coupled with robust antivirus solutions, are critical. Employing strong passwords and enabling two-factor authentication further enhance security. Being cautious about downloading apps from untrusted sources and scrutinizing app permissions are equally important preventative measures. Utilizing secure Wi-Fi networks and avoiding public Wi-Fi when handling sensitive information are additional protective steps.
Recommendations for Developing Secure Mobile Applications
Developing secure mobile applications necessitates a proactive approach, incorporating security best practices throughout the entire development lifecycle. This involves thorough code reviews to identify and address potential vulnerabilities. Implementing strong input validation and output encoding safeguards against common exploits. Utilizing secure communication protocols like HTTPS is crucial for protecting sensitive data during transmission. Employing secure storage mechanisms and regularly testing applications for vulnerabilities are equally important aspects of secure development.
This proactive approach can significantly reduce the risk of malware infiltrating the application.
Preventative Measures for Individuals and Organizations
Effective prevention requires a multifaceted approach, encompassing both individual and organizational strategies. A robust strategy should include the following:
- Regularly update operating systems and applications: Outdated software often contains vulnerabilities that malicious actors can exploit. Keeping software current significantly reduces the risk of infection. Regular patching is critical for security.
- Install and maintain reliable antivirus software: Antivirus software detects and removes malicious software, providing a crucial layer of protection. It’s vital to select and use trusted antivirus solutions that provide comprehensive protection.
- Exercise caution when downloading apps: Be wary of downloading apps from untrusted sources. Verify app sources and check app ratings and reviews before installation. Download apps only from official app stores or verified developers.
- Use strong passwords and enable two-factor authentication: Strong passwords and two-factor authentication add an extra layer of security, making it more challenging for attackers to access accounts. This is vital for protecting sensitive information and accounts.
- Be cautious about clicking on suspicious links or attachments: Phishing attacks often involve deceptive links or attachments. Do not click on links or open attachments from unknown senders, and exercise extreme caution regarding emails and messages from unfamiliar sources.
- Avoid using public Wi-Fi for sensitive transactions: Public Wi-Fi networks are often unsecured, making them vulnerable to eavesdropping and data theft. Avoid conducting sensitive transactions on public Wi-Fi networks to prevent data breaches.
- Regularly back up important data: Data loss due to malware infections can be devastating. Regular backups of important data ensure that it can be restored if an infection occurs. Data backups are critical for business continuity and minimizing loss.
Technical Analysis of Malware
Dissecting the intricate methods employed by mobile malware is crucial for effective mitigation strategies. Understanding the techniques used to infect devices, the propagation mechanisms, and the analytical processes involved in uncovering these threats empowers security professionals to develop robust defenses. This exploration delves into the technical aspects of mobile malware, providing insights into the tactics employed by attackers.The intricate world of mobile malware necessitates a deep understanding of its technical underpinnings.
Recent studies are painting a grim picture of a potential mobile malware explosion. It’s a worrying trend, especially considering the parallels to the security vulnerabilities highlighted in “baby apples ii the curse of xerox” baby apples ii the curse of xerox. This echoes the pervasive nature of these threats, reminding us that the fight against mobile malware is far from over.
The ongoing research suggests we need to be more vigilant than ever.
This includes the specific methods used to infiltrate devices, the propagation strategies employed, and the analytical techniques used to dissect these malicious programs. This section will Artikel these techniques and provide examples, illuminating the complexities of this threat landscape.
Infection Techniques
Mobile malware often exploits vulnerabilities in operating systems or applications to gain unauthorized access. Common infection vectors include malicious websites, compromised apps, and infected files shared via messaging platforms. Sophisticated techniques like social engineering are also employed to trick users into installing malware disguised as legitimate applications.
Malware Code Examples
While precise code snippets are omitted for brevity and to avoid potential misuse, it’s important to understand the types of malicious code utilized. This could include code designed to steal credentials, exfiltrate data, or compromise device functionalities. For instance, a piece of malware might use obfuscation techniques to conceal its malicious intent, making it more difficult to detect and analyze.
Propagation Mechanisms
Malware propagation often leverages various channels. These include vulnerabilities in operating systems, exploiting social engineering tactics to trick users into installing malicious apps, or utilizing compromised legitimate apps to spread to other devices. Another method involves exploiting weaknesses in the device’s communication protocols, allowing the malware to propagate rapidly across a network.
Mobile Malware Analysis
Analyzing mobile malware samples requires specialized tools and techniques. Static analysis involves examining the code without executing it, while dynamic analysis involves observing the malware’s behavior in a controlled environment. Reverse engineering plays a vital role in understanding the intricate functionalities and mechanisms employed by the malware. This can include disassembling the code, tracing its execution flow, and identifying the specific actions it performs.
Table: Mobile Malware Attack Lifecycle
| Stage | Description |
|---|---|
| Pre-infection | Attackers research vulnerabilities, identify potential targets, and develop their attack strategies. This phase involves meticulous planning and reconnaissance to maximize the likelihood of success. |
| Infection | Malicious code is delivered to the target device. This can involve phishing emails, malicious apps, or exploiting vulnerabilities in existing apps. The goal is to gain access to the device. |
| Propagation | The malware spreads to other devices within the network. This could involve exploiting network vulnerabilities or relying on social engineering techniques to entice other users to install the malware. |
| Command and Control | The infected device communicates with a command-and-control (C&C) server, receiving instructions and transferring data. This stage is critical for the malware’s functionality and control. |
| Data Exfiltration | The malware extracts sensitive data from the infected device and transmits it to the attacker’s server. This could involve financial information, personal data, or intellectual property. |
| Cleanup | The attacker removes traces of the malware from the infected device. This often involves removing logs, deleting files, or obfuscating any evidence of the attack. |
Case Studies
Mobile malware attacks are no longer theoretical threats; they’ve become a pervasive reality, impacting individuals and organizations worldwide. Understanding real-world examples, their characteristics, and consequences is crucial for developing effective defense strategies. This section delves into specific cases, highlighting the tactics employed by attackers and the resulting damage.Real-world mobile malware attacks often exploit vulnerabilities in operating systems, applications, or user behavior.
The sophistication of these attacks is constantly evolving, necessitating continuous vigilance and proactive security measures.
The “Fake App” Campaign
Malicious actors frequently distribute malware disguised as legitimate applications. This tactic, known as “malware-in-disguise,” preys on user trust and the convenience of app stores. Victims often download these apps unknowingly, inadvertently installing malware on their devices. The consequences can range from data theft to complete device compromise.
- Example: A fake banking app, seemingly identical to a legitimate banking application, is distributed through unofficial app stores or social media platforms. Users, lured by the app’s functionality or attractive offers, download and install it. Once installed, the malware collects sensitive financial data, including login credentials, account numbers, and transaction details. This data is then exfiltrated to the attackers, enabling fraudulent activities such as unauthorized fund transfers or account takeover.
The “SMS Spam” Attack, Study suggests mobile malware storm brewing
SMS spam is a persistent method used to deliver malicious payloads. Sophisticated SMS campaigns can exploit vulnerabilities in SMS gateways or mobile operating systems to deploy malware.
- Example: A campaign utilizes SMS messages containing malicious links or attachments. Clicking on these links may download malware onto the device. The malware might then install itself on the device, enabling access to sensitive information or even complete device control. This type of attack is frequently used to distribute ransomware, spyware, or other malicious programs.
The “Location-Based” Attack
Location-based attacks leverage users’ geographic data to target specific individuals or groups. By identifying victims in specific regions or near specific locations, attackers can tailor their attacks to maximize impact.
- Example: Malicious actors target users in a particular region by sending location-based SMS messages. These messages might contain malicious links or downloads that exploit the victim’s device’s location-tracking capabilities. The malware might then monitor the victim’s location or use it as a key to further exploit their personal data.
Impact Analysis
The impact of these attacks can be severe, affecting individuals and organizations in various ways. Financial losses, reputational damage, and legal repercussions are common outcomes.
- Financial Loss: Stolen financial data can lead to significant financial losses for victims, who might face fraudulent charges, unauthorized transactions, or account closures.
- Data Breach: Sensitive personal information, such as contact details, passwords, and credit card information, can be compromised. This data can be used for identity theft, fraud, or other malicious activities.
- Reputational Damage: For businesses, compromised data can lead to a loss of trust and credibility among customers and partners.
Future Predictions: Study Suggests Mobile Malware Storm Brewing
The mobile malware landscape is constantly evolving, driven by advancements in technology and the ever-increasing sophistication of cybercriminals. Predicting the future is inherently challenging, but by analyzing current trends and potential technological advancements, we can gain valuable insights into the shape of mobile malware in the years to come. This section delves into potential future developments, focusing on new attack vectors, the impact of emerging technologies, and the broader implications for mobile security.
Potential Future Developments in Mobile Malware
The future of mobile malware will likely see a combination of existing threats amplified and novel techniques emerging. We can anticipate an increase in the sophistication of existing malware types, such as banking Trojans and ransomware. This sophistication will manifest in more targeted attacks, exploiting specific vulnerabilities within individual devices and operating systems. Furthermore, we can expect the rise of new malware categories tailored to specific emerging technologies.
Impact of New Technologies on Malware Development
The integration of new technologies will significantly influence malware development. The rise of artificial intelligence (AI) and machine learning (ML) presents a dual challenge. On one hand, AI can be employed to enhance the capabilities of malware analysis tools, enabling faster detection and mitigation. On the other hand, AI and ML can be harnessed by malicious actors to create more sophisticated and adaptive malware.
For example, AI-powered malware can learn user behavior patterns, making it more difficult to detect and counter. The proliferation of the Internet of Things (IoT) presents another avenue for exploitation, as interconnected devices can become vulnerable entry points for malware to enter the mobile ecosystem.
Evolution of Attack Vectors
Attack vectors will continue to evolve, adapting to the changing security landscape. Traditional attack vectors, such as phishing and malicious apps, will remain prevalent but will likely become more sophisticated. The increased use of social engineering tactics, often in conjunction with targeted attacks, will become more commonplace. For instance, attackers may leverage social media platforms to spread malicious content or exploit vulnerabilities in messaging apps to gain access to user data.
Furthermore, the emergence of new technologies, like blockchain, may also create opportunities for novel attack vectors.
Summary of Potential Future Trends
Several key trends suggest a concerning future for mobile security. The rise of sophisticated, AI-powered malware, coupled with the exploitation of emerging technologies, poses a significant threat to individuals and organizations alike. The evolution of attack vectors, focusing on social engineering and targeted attacks, underscores the importance of proactive security measures. Mobile security professionals must stay ahead of these trends by continuously monitoring and adapting to the dynamic nature of mobile threats.
Data Visualization
Visualizing the prevalence of mobile malware across different regions is crucial for understanding its global distribution and potential impact. This allows for targeted mitigation strategies and the identification of high-risk areas requiring immediate attention. Mapping the spread and frequency of malware infections provides a clear picture of where security vulnerabilities are most exploited and helps prioritize resources for enhanced protection.
Regional Prevalence of Mobile Malware
Understanding the geographic distribution of mobile malware is vital for pinpointing regions experiencing higher infection rates. This knowledge enables the development of targeted security measures and the allocation of resources where they are most needed. A clear visualization can help identify regions with specific vulnerabilities or behaviors, enabling a more proactive approach to mitigating the threat.
| Region | Estimated Prevalence (2023) | Trend (2022-2023) | Possible Contributing Factors |
|---|---|---|---|
| North America | 20% | Stable | Strong cybersecurity infrastructure, but emerging threats targeting specific demographics |
| Western Europe | 15% | Slight increase | Sophisticated attacks targeting financial institutions, increased use of mobile banking |
| Southeast Asia | 30% | Significant increase | Rapid mobile adoption, weaker security awareness among users, less robust cybersecurity infrastructure |
| Latin America | 25% | Steady increase | Widespread use of older mobile devices, limited access to security updates |
| Africa | 10% | Moderate increase | Growing mobile penetration, limited access to advanced security technologies |
The table above provides a simplified representation of the estimated prevalence of mobile malware across various regions. These percentages are approximations based on publicly available data from security analysis firms. The trends observed, such as the increasing prevalence in Southeast Asia, are significant indicators for security researchers and policymakers.
Visual Representation of the Data
A comprehensive visualization, such as a world map, can effectively illustrate the geographical distribution of mobile malware. Each region or country could be color-coded based on its infection rate, with darker shades indicating higher prevalence. This visual representation allows for immediate recognition of high-risk areas, enabling a swift response.
Key Patterns and Trends
Several patterns emerge from analyzing the regional data. The data consistently points to a correlation between the prevalence of malware and factors such as the level of mobile adoption, cybersecurity infrastructure, and user awareness. Southeast Asia, for example, exhibits a notable increase in malware prevalence, possibly linked to the rapid expansion of mobile technology and comparatively lower levels of security awareness.
Conversely, regions with strong cybersecurity infrastructure, like North America, show a more stable trend. These insights are invaluable for crafting effective security strategies.
End of Discussion

The study’s findings paint a concerning picture of a potential mobile malware storm. The increasing sophistication of attacks, coupled with the expanding global mobile user base, creates a volatile environment. Understanding the diverse types of malware, their impact, and emerging trends is paramount for mitigating this threat. The study’s emphasis on mitigation strategies and preventative measures provides a valuable roadmap for individuals and organizations to bolster their security posture.
Ultimately, proactive defense and a collective understanding of this evolving landscape are crucial for safeguarding our digital future.







