Symantec Blended Attacks on the Rise
Symantec more computer attacks use blended tactics, highlighting a disturbing trend in cybersecurity. These attacks combine various methods, from social engineering to malware, making them incredibly difficult to detect and defend against. Understanding the intricacies of these blended attacks is crucial for organizations to bolster their defenses and mitigate the potential damage.
This comprehensive exploration dives into the different facets of blended threats, examining Symantec’s observations, the impact on businesses, and strategies for countering these sophisticated attacks. We’ll delve into the technical aspects, real-world case studies, and future predictions, ultimately equipping you with a deeper understanding of this evolving threat landscape.
Defining Blended Threats
The cybersecurity landscape is constantly evolving, and attackers are becoming increasingly sophisticated in their methods. One particularly concerning trend is the rise of blended threats, which combine multiple attack vectors to maximize their impact and evade detection. Understanding these multifaceted attacks is crucial for organizations to effectively protect their systems and data.Blended threats are not simply the sum of their individual parts; they represent a coordinated attack strategy where different attack vectors work in concert to achieve a larger objective.
This synergy allows attackers to bypass traditional security measures designed to counter single attack vectors. The complexity of blended threats often makes them difficult to detect and mitigate, requiring a multifaceted security approach.
Attack Vector Combinations
Blended attacks leverage a combination of techniques, including malware, social engineering, exploit kits, and vulnerabilities in software. Attackers meticulously choose these vectors to maximize their chances of success. This often involves exploiting human weaknesses alongside technical vulnerabilities, creating a powerful attack surface.
Motivations Behind Blended Tactics
Attackers employ blended tactics for several reasons. Financial gain is a primary motivator, with attackers targeting sensitive data for ransom or selling it on the dark web. Political motivations, espionage, and disrupting critical infrastructure are also driving factors. The sheer complexity and difficulty in attribution of blended attacks make them attractive for various actors, whether nation-states or criminal organizations.
Symantec’s recent report highlights a worrying trend: more computer attacks are using blended tactics. This means cybercriminals are combining various attack vectors, making it harder for security software to detect and defend against. Interestingly, this complex threat landscape contrasts with the simpler, CD-based approach of early internet PCs, like the one launched by Lindows.com. While the initial simplicity of internet access was a step forward, the evolution of attacks now demands sophisticated defensive strategies, highlighting the need for proactive security measures in today’s digital world.
Examples of Successful Blended Attacks
Several high-profile blended attacks have demonstrated the effectiveness of this approach in recent years. One notable example involved a sophisticated campaign targeting government agencies, utilizing spear-phishing emails containing malicious attachments to gain initial access. Once inside, attackers deployed malware to steal sensitive data and subsequently used exploit kits to move laterally across the network. These attacks often demonstrate the ability of attackers to adapt and refine their methods, making detection and mitigation challenging.
Comparison of Blended Attack Types
| Attack Type | Description | Common Techniques | Example |
|---|---|---|---|
| Social Engineering | Manipulating individuals to gain access to sensitive information or systems. | Phishing, spear-phishing, baiting | A targeted phishing email containing a malicious link to download malware. |
| Malware | Malicious software designed to damage, disable, or gain unauthorized access to a system. | Trojans, ransomware, viruses | Ransomware encrypting a victim’s data and demanding payment for its release. |
| Exploit Kits | Pre-packaged sets of tools for exploiting software vulnerabilities. | Automated exploits, vulnerability scanners | An exploit kit used to automatically exploit a known vulnerability in a web application. |
Symantec’s Perspective on Evolving Tactics
Symantec’s ongoing research consistently reveals a disturbing trend: cybercriminals are increasingly employing sophisticated, blended attack strategies. These attacks, combining multiple techniques to evade detection and maximize impact, pose a significant threat to organizations across industries. This shift underscores the critical need for robust, multi-layered security defenses.Symantec’s research methodology involves a combination of threat intelligence gathering, analysis of malware samples, and real-world incident response data.
Symantec’s recent report highlights a concerning trend of blended attacks in computer security. This increasing complexity is a significant concern, especially as evidenced by the recent Linux milestones in supercomputing deals, like the Los Alamos National Laboratory’s advancements. linux hits landmarks in los alamos supercomputer deals shows a shift towards more powerful, and potentially vulnerable, systems.
Ultimately, these intertwined trends underscore the evolving nature of cyber threats and the ongoing need for robust security measures.
The company employs a global network of threat researchers who meticulously dissect malicious code, identify attack patterns, and analyze the motivations behind these sophisticated campaigns. This holistic approach allows Symantec to identify emerging threats and provide proactive insights into evolving attack vectors.
Symantec’s recent report highlights a concerning trend of more computer attacks employing blended tactics. This means attackers are combining various techniques to bypass security measures, making it harder to detect and defend against them. Meanwhile, Intel’s advancements in mobile processor technology, like intel speeds mobile phones with single chip processor , showcase the ongoing arms race between innovation and malicious intent.
Ultimately, these sophisticated blended attacks require proactive security measures to stay ahead of the curve.
Symantec’s Observations on Increasing Blended Attacks
Symantec’s observations highlight a clear escalation in the use of blended attacks. These attacks are no longer isolated incidents; they are a pervasive tactic employed by various threat actors. The sophisticated nature of these attacks requires organizations to move beyond basic security measures and embrace proactive threat intelligence.
Types of Blended Attacks Observed by Symantec
Symantec has documented a rise in several types of blended attacks. These include:
- Malicious email campaigns combined with exploit kits: This approach leverages the widespread use of email to deliver malicious attachments or links. These attachments or links then exploit vulnerabilities in software to install malware on compromised systems. The sophistication of these kits often includes evasion techniques, making them harder to detect.
- Supply chain attacks incorporating ransomware: Cybercriminals are increasingly targeting software and hardware supply chains to introduce ransomware. This approach allows for widespread infection and disruption, impacting not only the immediate target but also downstream organizations.
- Phishing attacks leading to credential theft and data exfiltration: Criminals often employ sophisticated phishing campaigns that lead to the compromise of user credentials. These credentials are then used to access sensitive data and exfiltrate it for financial gain or other malicious purposes.
- Malware disguised as legitimate software updates: This technique exploits the natural process of software updates to introduce malicious code. Users, unaware of the malicious intent, may unwittingly download and execute the malicious software.
Key Characteristics of Evolving Blended Attacks
The key characteristics of these evolving blended attacks include:
- Polymorphism and obfuscation: Malicious code is often designed to change its form (polymorphism) or hide its true nature (obfuscation) to evade detection by traditional security tools.
- Exploiting multiple vulnerabilities: Attackers frequently combine multiple exploits to compromise systems. This increases the likelihood of successful penetration and limits the effectiveness of single-point defenses.
- Persistence mechanisms: Malicious actors often employ persistence mechanisms to ensure ongoing access to compromised systems, enabling further actions like data exfiltration or command and control operations.
- Lateral movement: Once inside a network, attackers leverage lateral movement techniques to traverse the network and access additional sensitive resources. This often involves exploiting weak or misconfigured systems.
Comparison to Other Security Reports
| Characteristic | Symantec Findings | Other Security Reports |
|---|---|---|
| Prevalence of Blended Attacks | Increasingly common, across various attack vectors | Consistent reporting of rising blended attack prevalence across multiple sources |
| Sophistication of Techniques | Advanced polymorphism, obfuscation, and exploitation of multiple vulnerabilities | Growing sophistication of tactics observed, often combining multiple attack vectors |
| Impact of Attacks | Significant financial losses and reputational damage to organizations | Reports consistently highlight the detrimental effects of blended attacks on businesses and critical infrastructure |
Impact of Blended Attacks
Blended attacks, leveraging multiple attack vectors, pose a significant threat to businesses. These sophisticated attacks are no longer isolated incidents but a pervasive reality in the digital landscape. Understanding the multifaceted impacts of these attacks is crucial for developing effective defense strategies. The financial, reputational, and operational repercussions can be devastating, demanding proactive measures to mitigate risks.
Financial Implications
Businesses face substantial financial losses from blended attacks. Direct costs include incident response, forensic analysis, data recovery, and regulatory fines. Indirect costs, often more significant, encompass lost productivity, customer churn, and damage to brand reputation, leading to decreased sales and diminished market share. The ripple effect of these losses can extend throughout the supply chain, impacting various stakeholders.
A compromised payment system, for instance, can result in substantial financial losses to customers and businesses alike. Furthermore, the ongoing maintenance and updates needed to secure systems against evolving threats add to the overall financial burden.
Reputational Damage
The reputational damage caused by a blended attack can be catastrophic, often lasting far longer than the immediate impact of the breach. Customers lose trust in the organization’s ability to protect their sensitive information, leading to significant churn and loss of future business. Negative media coverage, lawsuits, and public scrutiny can tarnish the brand image and make it challenging to attract and retain talent.
The perception of vulnerability can discourage investors and partners, further exacerbating the negative consequences. For example, a major data breach involving a retailer could lead to a significant drop in consumer confidence, affecting future sales and profitability.
Data Breaches
Blended attacks often result in significant data breaches, exposing sensitive customer information. This data includes financial details, personally identifiable information (PII), and intellectual property, all of which can be used for fraudulent activities. The potential for identity theft, financial fraud, and reputational harm to victims is significant. One well-known example is the Sony Pictures Entertainment hack in 2014, which involved a combination of phishing and malware attacks, leading to the release of sensitive data.
The subsequent reputational damage and financial losses for Sony were considerable.
Operational Disruptions
Blended attacks can cause significant operational disruptions, impacting critical business functions. Systems can be crippled, services suspended, and productivity severely hampered. These disruptions can lead to lost revenue, delays in projects, and difficulty in meeting customer demands. Furthermore, the recovery process itself can be lengthy and complex, further prolonging the operational disruptions. The cascading effect of a blended attack can disrupt the entire workflow and hinder the smooth operation of a business.
Potential Impact of Attack Vectors
| Attack Vector | Financial Impact | Reputational Impact | Operational Impact |
|---|---|---|---|
| Phishing | Loss of customer trust, data breaches | Negative brand image | Decreased productivity, loss of customers |
| Malware | System downtime, data loss | Negative media coverage | Operational delays, recovery costs |
| Social Engineering | Financial losses, data breaches | Loss of customer trust | Security vulnerabilities, legal issues |
| Exploit Kits | Data breaches, system compromise | Loss of customer trust, regulatory fines | Downtime, operational disruption |
Countermeasures and Mitigation Strategies
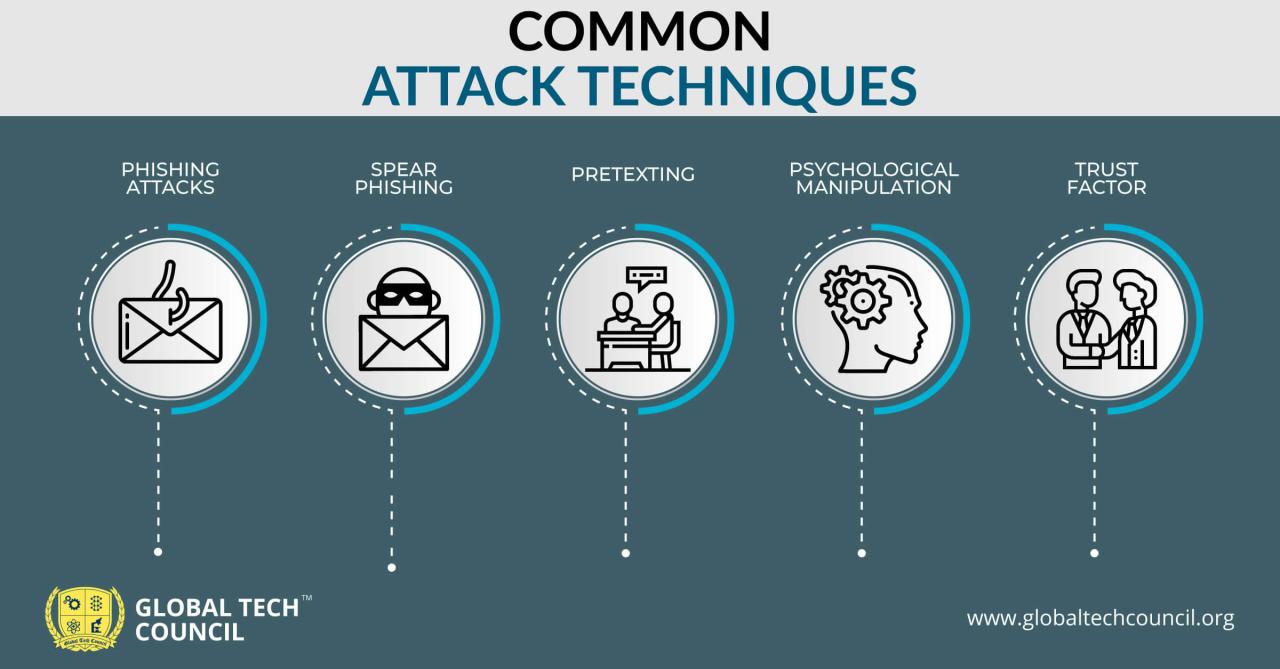
Defending against blended threats requires a multifaceted approach that goes beyond traditional security measures. These attacks exploit vulnerabilities across multiple vectors, demanding a layered defense strategy and proactive threat intelligence. Effective countermeasures must address the unique characteristics of each attack component to effectively neutralize the combined threat.
Layered Security Approaches
A layered security approach is crucial in mitigating blended threats. This strategy involves implementing multiple security controls at different points in the attack lifecycle, creating multiple barriers to impede the attacker. Each layer provides a different level of defense, and their combined effect strengthens the overall security posture. This approach is crucial because blended threats attempt to bypass single points of failure.
For example, a malicious email might be used to deploy malware, which then leverages system vulnerabilities to gain access to sensitive data. A layered approach could involve email filtering, endpoint detection and response (EDR), and intrusion detection systems (IDS) to counteract these distinct attack stages.
Specific Security Measures
Implementing robust security measures across different layers is paramount. Security information and event management (SIEM) systems are crucial for aggregating and analyzing security logs from various sources. This allows for real-time threat detection and response. Endpoint security solutions, such as antivirus and anti-malware software, are essential to protect individual devices from infection. Network security controls, including firewalls and intrusion prevention systems (IPS), are vital for monitoring and controlling network traffic.
Furthermore, implementing strong access controls, including multi-factor authentication (MFA), limits potential damage if an attacker gains access to a compromised account. Regular software updates and patching are essential to close known vulnerabilities exploited in blended attacks.
Threat Intelligence
Effective threat intelligence is indispensable for identifying and responding to blended threats. Organizations need to proactively gather and analyze information about emerging threats, attack patterns, and tactics. This allows them to tailor security defenses to specific threats, rather than relying on generic solutions. For instance, if threat intelligence indicates a new type of blended attack targeting specific software, organizations can immediately adjust their security posture and proactively block or mitigate the attack vector.
Defense Mechanisms Against Blended Attacks, Symantec more computer attacks use blended tactics
| Defense Mechanism | Effectiveness Against Blended Attack Types |
|---|---|
| Firewall | Blocks network-based attacks. Less effective against attacks that leverage internal exploits or social engineering. |
| Intrusion Prevention System (IPS) | Detects and blocks malicious network traffic. Can be less effective against polymorphic malware or attacks that evade signature-based detection. |
| Antivirus/Anti-malware | Detects and removes known malware. May not be effective against zero-day exploits or advanced persistent threats. |
| Endpoint Detection and Response (EDR) | Provides real-time threat detection and response on endpoints. Highly effective against attacks targeting specific endpoints. |
| Security Information and Event Management (SIEM) | Aggregates security logs and analyzes for anomalies. Provides a comprehensive view of the attack and helps correlate events from multiple sources. |
| Multi-Factor Authentication (MFA) | Adds an extra layer of security to accounts. Reduces the impact of compromised credentials. |
Technical Aspects of Blended Threats
Blended threats represent a sophisticated evolution in cyberattacks, leveraging multiple attack vectors to bypass traditional security defenses. Understanding the technical components and their interplay is crucial for effective mitigation. This section delves into the technical underpinnings of these attacks, highlighting the tactics used by malicious actors.
Malware Components in Blended Threats
Malware, a core element of blended attacks, often comes in various forms. Understanding the different types and their functionalities is essential to recognizing and countering these attacks. Different malware types exhibit unique behaviors, each designed to achieve a specific objective within the overall attack strategy.
- Exploit Kits: These kits are pre-packaged tools that automate the exploitation of vulnerabilities in software applications. They provide attackers with a ready-made arsenal for exploiting weaknesses in systems, making them incredibly efficient. These kits often target popular applications, allowing for widespread infection.
- Rootkits: These are designed to hide malicious activities from detection by security software. They gain control over a system without being easily detected, enabling attackers to maintain persistence and execute various malicious actions without raising suspicion. Rootkits often work by altering the operating system’s core functions.
- Keyloggers: Keyloggers are malware that records every keystroke made on an infected system. This data can include passwords, credit card details, and other sensitive information. They are often used in conjunction with other malware to gather intelligence or steal sensitive data.
- Ransomware: Ransomware encrypts the victim’s data, rendering it inaccessible. Attackers demand payment in exchange for the decryption key. The sophistication of ransomware has increased significantly, with attacks often targeting specific organizations or industries.
Exploits and Vulnerability Targeting
Exploits are crucial in enabling blended threats to gain initial access to systems. They leverage vulnerabilities in software or hardware to execute malicious code.
- Zero-Day Exploits: These exploit vulnerabilities that are unknown to the software vendor. They are highly dangerous as there are no patches available to defend against them. These exploits often appear in the wild, allowing attackers to swiftly exploit weaknesses before a fix can be implemented.
- Known Vulnerability Exploits: These exploit vulnerabilities that are publicly known, but for which a fix has not been implemented. Attackers leverage these vulnerabilities, recognizing that a lack of patching leaves systems exposed. This underscores the criticality of regular security updates.
Social Engineering Techniques
Social engineering techniques are used to manipulate individuals into performing actions that compromise security. This can involve tricking users into clicking malicious links or revealing sensitive information.
- Phishing: Phishing involves sending deceptive emails or messages that appear legitimate. These messages are designed to trick users into revealing sensitive information or downloading malware.
- Spear Phishing: This is a targeted phishing attack where attackers tailor their messages to specific individuals or organizations. The more personalized the message, the higher the chance of success. Spear phishing attacks are often used to target high-value targets.
- Baiting: Baiting involves enticing victims with something of value to lure them into downloading malware or clicking malicious links. This can include tempting offers, attractive software, or other seemingly harmless enticements.
Interaction of Components in a Blended Attack
A blended attack typically involves a coordinated use of multiple components. The attackers combine malware, exploits, and social engineering techniques to maximize their impact.
| Phase | Description |
|---|---|
| Initial Access | Attackers use social engineering to gain initial access, followed by exploit kits to exploit vulnerabilities. |
| Persistence | Rootkits maintain persistent access to the system. |
| Data Collection | Keyloggers collect sensitive information. |
| Delivery | Malware delivers additional payloads, spreading to other systems. |
| Data Exfiltration | Stolen data is exfiltrated from the compromised system. |
Different Malware Types in Blended Attacks
Various malware types are used in blended attacks. The choice depends on the attacker’s objectives and the target environment.
- Polymorphic Malware: This malware changes its code structure each time it replicates. This makes it difficult for security software to detect. It can be a significant challenge to identify and neutralize this type of malware.
- Metamorphic Malware: This malware modifies its code’s structure and functionality each time it replicates. This makes it even harder to detect than polymorphic malware.
Case Studies and Real-World Examples: Symantec More Computer Attacks Use Blended Tactics
Blended attacks are no longer a theoretical threat; they’re a harsh reality for organizations worldwide. Understanding how these attacks unfold, their methods, and their consequences is crucial for developing effective defense strategies. This section delves into real-world case studies, highlighting the diverse tactics employed and the significant impact they can have.Real-world examples of blended attacks illustrate the sophistication and multifaceted nature of these threats.
Analyzing these incidents provides invaluable insights into the evolving tactics used by attackers, enabling organizations to better anticipate and mitigate future threats.
Stuxnet Worm (2010)
The Stuxnet worm, a highly sophisticated piece of malware, stands as a prime example of a blended threat. Its attack vector combined a worm-like propagation mechanism with targeted exploits against industrial control systems (ICS). This resulted in significant damage to Iranian nuclear facilities.
- The attack leveraged multiple vulnerabilities in industrial control systems software.
- Stuxnet exploited previously unknown vulnerabilities to gain unauthorized access.
- The malware’s payload included components designed to disrupt the centrifuges used in uranium enrichment.
- The infection chain involved both network and physical components, demonstrating the blended nature of the attack.
The outcome of the Stuxnet attack was substantial disruption to Iranian nuclear programs. The incident highlighted the potential for cyberattacks to cause physical damage and have real-world consequences.
WannaCry Ransomware (2017)
The WannaCry ransomware outbreak showcased the rapid propagation capabilities of malware. The attack employed a worm-like mechanism, exploiting a vulnerability in Microsoft’s SMB protocol. It spread globally, affecting numerous organizations, including hospitals and government agencies.
- The attack relied on the EternalBlue exploit, a vulnerability in the Windows Server Message Block (SMB) protocol.
- The rapid spread was facilitated by the worm-like nature of the malware, leveraging automated network scanning and propagation.
- The ransomware encrypted critical data, demanding payment in cryptocurrency for its release.
- The attack’s global reach underscored the importance of patching vulnerabilities in a timely manner.
The consequences of WannaCry were widespread data loss and significant financial burdens for affected organizations. The incident highlighted the vulnerability of critical infrastructure to ransomware attacks.
NotPetya (2017)
The NotPetya attack differed significantly from other blended threats, demonstrating the potential for supply chain attacks. It initially presented as ransomware, but its destructive payload led to data wiping across numerous systems. This attack leveraged a compromised software update.
- The attack initially appeared as ransomware but ultimately caused data wiping across numerous systems.
- NotPetya utilized a supply chain compromise to distribute the malware, effectively exploiting a software update.
- The destructive nature of NotPetya demonstrated the potential for cyberattacks to have far-reaching and irreversible effects.
- The attack exploited a vulnerability in the Windows operating system.
The outcome of the NotPetya attack was devastating, with substantial data loss and operational disruption across affected organizations. The attack also highlighted the risk of attacks leveraging compromised software updates.
Summary Table of Case Studies
| Case Study | Attack Methodology | Outcomes/Consequences | Common Patterns |
|---|---|---|---|
| Stuxnet | Exploiting ICS vulnerabilities, worm-like propagation | Disruption of Iranian nuclear facilities | Targeting critical infrastructure, combining network and physical attacks |
| WannaCry | Exploiting SMB vulnerability, worm-like propagation | Global ransomware outbreak, widespread data loss | Leveraging known vulnerabilities, rapid propagation |
| NotPetya | Supply chain compromise, data wiping payload | Devastating data loss, operational disruption | Exploiting software updates, potentially irreversible damage |
Future Trends and Predictions
The landscape of cyber threats is constantly evolving, with blended attacks becoming increasingly sophisticated. Understanding the future trajectory of these attacks is crucial for proactively adapting security measures. Predicting the precise form of future threats is challenging, but analyzing current trends and emerging technologies provides valuable insights into potential avenues of attack. This section delves into potential future trends, highlighting the importance of adapting security measures to combat the evolving nature of blended threats.
Future Evolution of Blended Threats
Blended attacks are likely to become even more intricate, combining multiple attack vectors to bypass traditional security defenses. This complexity will involve a deeper integration of attack stages, making detection and mitigation more difficult. Instead of a single point of failure, attackers will likely exploit vulnerabilities across multiple systems and applications, often leveraging social engineering and human error as entry points.
Potential New Attack Vectors and Tactics
The rise of Internet of Things (IoT) devices presents a significant new attack vector. Attackers may exploit vulnerabilities in these devices to gain access to corporate networks or critical infrastructure. Further, advancements in artificial intelligence (AI) will enable more sophisticated and personalized attacks. AI-powered tools will allow attackers to create highly targeted and effective attacks tailored to specific vulnerabilities in a particular organization’s infrastructure.
Sophisticated phishing campaigns, utilizing deepfakes and AI-generated content, will likely become more common, exploiting psychological vulnerabilities and social engineering tactics.
Importance of Adapting Security Measures
Proactive adaptation is essential to maintain a strong security posture. Organizations must adopt a layered approach to security, combining robust technical controls with human-centric security awareness training. The focus should shift from simply reacting to attacks to anticipating and mitigating them. This involves continuous monitoring, threat intelligence gathering, and adapting security tools to detect and respond to emerging attack patterns.
Role of Artificial Intelligence in Detection and Response
AI is poised to play a significant role in detecting and responding to blended attacks. AI-powered systems can analyze vast amounts of data to identify anomalies and potential threats in real-time. Machine learning algorithms can be trained to recognize patterns and behaviors associated with blended attacks, allowing for early detection and rapid response. This capability will be crucial in combating the complexity and speed of future blended threats.
Potential Future Trends in Blended Attacks
- Increased Use of AI-powered Attacks: Sophisticated attacks will utilize AI to tailor attacks to specific vulnerabilities in individual organizations. This includes more targeted phishing campaigns, utilizing AI-generated content to manipulate victims and increase success rates.
- Exploitation of IoT Devices: The expanding network of IoT devices will create more potential attack surfaces. Vulnerabilities in these devices will be exploited to gain access to corporate networks or critical infrastructure.
- Multi-stage Attacks with Advanced Persistence: Attacks will likely involve multiple stages, potentially involving malware, ransomware, and data exfiltration, with increased efforts to maintain persistence within the compromised systems.
- Advanced Social Engineering Techniques: Phishing and other social engineering attacks will become increasingly sophisticated, utilizing deepfakes, AI-generated content, and personalized messages to exploit human psychology.
- Supply Chain Attacks: Attackers will likely target the supply chain to gain access to sensitive information or critical infrastructure. Compromising trusted vendors or suppliers can provide a pathway into organizations.
Final Review

In conclusion, Symantec’s report underscores the escalating sophistication of cyberattacks, with blended tactics becoming a dominant force. The increasing use of combined attack vectors necessitates a proactive and layered security approach. Businesses must prioritize threat intelligence, invest in advanced security tools, and train employees to recognize and respond to these evolving threats. Adapting to the future of blended attacks is paramount to protecting valuable data and systems.