cybersecurity
-
Cybersecurity Threats

Xombe Trojan Microsoft Patch Spoofing
Xombe trojan spoofs Microsoft patch to steal personal info, posing as legitimate updates to gain unauthorized access. This malicious software…
Read More » -
Technology

Microsoft Security A Future Outlook
Microsoft security and the road ahead sets the stage for this exploration, diving deep into Microsoft’s current security posture, emerging…
Read More » -
Technology
Microsoft Sues Spammers Details & Tactics
Microsoft sues spammers details tactics, diving deep into the complexities of this ongoing legal battle. This in-depth look explores Microsoft’s…
Read More » -
Cybersecurity

Windows Cash Machine Worm Generates Concern A Deep Dive
Windows Cash Machine worm generates concern. This insidious malware poses a significant threat to financial systems, potentially causing widespread disruption…
Read More » -
Technology

U.S. Officials Warn Lax Cyber Defenses
U s officials warn of lax cyber defense – With U.S. officials warn of lax cyber defense, a critical issue…
Read More » -
Technology & Security

WiFi Security Complexity and Future Debated
WiFi security complexity and future debated, a topic brimming with challenges and opportunities. From the evolution of security protocols like…
Read More » -
Technology Trends
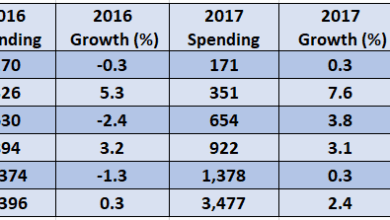
IT Spending Growth Direction Predicted
IT spending growth direction predicted, a comprehensive analysis of global trends, economic impacts, and technological advancements. This deep dive explores…
Read More » -
Technology

Software Security An Interview with ISSs Chris Klaus
The state of software security an interview with ISS founder and CTO Chris Klaus dives deep into the ever-evolving landscape…
Read More » -
Cybersecurity

Computer Viruses and Organized Crime A Deep Dive
Computer viruses and organized crime are intertwined in a dangerous dance. From sophisticated financial fraud to targeted infrastructure attacks, criminal…
Read More » -
Technology

Spam Threats Earn US Programmer Arrest
Spam threats earn u s programmer arrest, highlighting a disturbing trend in online activity. This case underscores the real-world consequences…
Read More »

