cybersecurity
-
Technology

HP Virus Throttler Worm Annihilation?
HP claims virus throttler snuffs out worms, promising a revolutionary approach to cybersecurity. This technology, if proven effective, could significantly…
Read More » -
Cybersecurity

Ken Xie on Fortinet Content Threats
Ken Xie of Fortinet on fighting content threats dives deep into the world of cybersecurity, exploring how companies can protect…
Read More » -
Cybersecurity

Report Shows Uptick in Automated Phishing
Report shows uptick in automated phishing, revealing a concerning trend in cybercrime. This sophisticated form of attack uses scripts and…
Read More » -
Business Security

Mobile Devices A Security Challenge for Companies
Mobile devices create security challenge for companies, as businesses increasingly rely on smartphones and tablets for everyday operations. From email…
Read More » -
Cybersecurity

Yahoo EarthLink Build Bulwark Against Spoofing
Yahoo EarthLink build bulwark against spoofing, a critical endeavor in the evolving digital landscape. Spoofing, a technique that deceptively impersonates…
Read More » -
Technology
Computer Associates Fires Latest Spyware Battle
Computer Associates fires latest round in spyware battle, igniting a new chapter in the ongoing cyber warfare. This escalating conflict…
Read More » -
Cybersecurity
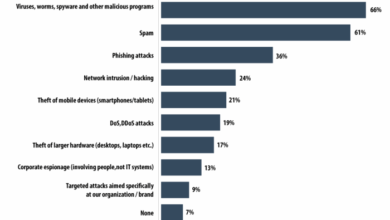
Enterprise Spyware Threats Reach All-Time High
Enterprise spyware threats reach all time high – Enterprise spyware threats reach all-time high, posing a significant and evolving danger…
Read More » -
Cybersecurity
Cybertrust TrusSecure & Betrusted Merge
Trusecure betrusted merge to create cybertrust – With TrusSecure and Betrusted merging to create CyberTrust, a new era of cybersecurity…
Read More » -
Business Compliance

Email and IM Compliance Navigating the Rules
e mail and instant messaging face compliance challenges, forcing businesses to navigate a complex landscape of regulations. From GDPR and…
Read More » -
Technology

Web Cam Worm Nets Seedy Side Exposed
Web cam worm highlights seedy side of net, revealing the underbelly of online interactions. This malicious software, often exploiting vulnerabilities…
Read More »

