cybersecurity
-
Network Security

Closing Up Wireless Security Holes A Deep Dive
Closing up wireless security holes is crucial in today’s interconnected world. This deep dive explores the vulnerabilities lurking in our…
Read More » -
Cybersecurity

Spyware the Next Spam A Growing Threat
Spyware the next spam, a silent menace lurking in the digital shadows, is evolving at an alarming rate. It’s not…
Read More » -
Security & Defense

Fighting Terrorism Through Technology A Comprehensive Approach
Fighting terrorism through technology is a complex and multifaceted endeavor. It involves leveraging surveillance technologies, data analytics, and social media…
Read More » -
Cybersecurity
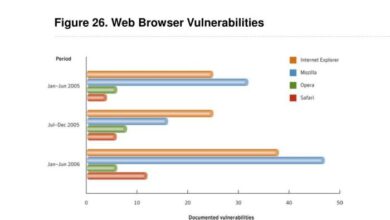
Browser-Based Attacks on the Rise A Growing Threat
Browser based attacks on the rise – Browser-based attacks on the rise are becoming a significant concern for users and…
Read More » -
Cybersecurity

NCSP Task Force Security Recommendations Unveiled
NCSP task force makes security recommendations, outlining crucial steps to bolster digital defenses. This report delves into the rationale behind…
Read More » -
Cybersecurity

Cybersecurity Must Be Priority A Crucial Imperative
Cybersecurity must be priority, a critical concern for individuals, businesses, and nations alike. From the ever-evolving landscape of cyber threats,…
Read More » -
Technology

UC Berkeley Hack Not Unusual, Analyst Says
UC Berkeley hack not unusual analyst says, prompting a look at the frequency of such incidents at the prestigious university.…
Read More » -
Technology

Microsoft Cisco Sharing Network Security Tech
Microsoft Cisco to share network security technologies promises a powerful synergy in the cybersecurity landscape. This collaboration combines Microsoft’s robust…
Read More » -
Technology
Cisco IBM Security Alliance A Powerful Duo
Cisco IBM team up on security, forging a powerful alliance that promises to reshape the cybersecurity landscape. This strategic partnership…
Read More »


