digital security
-
Technology
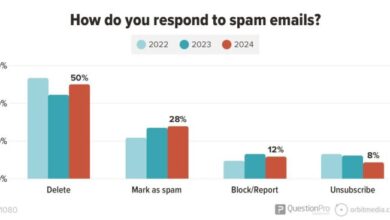
US Still the Ruling Land of Spam
US still the ruling land of spam, a disheartening truth that continues to plague our digital lives. From the early…
Read More » -
Technology

Spycatcher Deadly to Spyware, But Watch Out
Spycatcher deadly to spyware but watch out. This exploration delves into the fascinating world of digital security, examining the powerful…
Read More » -
Cybersecurity
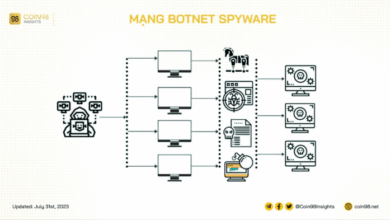
Phileas Project Bots vs. Spyware
Phileas project uses bots to ferret out spyware, a groundbreaking initiative designed to proactively identify and neutralize malicious software. This…
Read More » -
Technology & Society

Moral Dilemma Hackers for Hire A Dark Market
Moral dilemma hackers for hire represent a shadowy market, where individuals seeking to exploit vulnerabilities are connected with those skilled…
Read More » -
Technology
Spam Wars Fighting the Mass Mail Onslaught
Spam wars fighting the mass mail onslaught are a relentless battle against unwanted emails. From the early days of unsolicited…
Read More » -
Technology

Latest Worms New Troubling Tricks
Latest worms perform new troubling tricks, highlighting evolving tactics and posing significant threats to digital security. These newly discovered worms…
Read More » -
Cybersecurity

Convergence Quagmire Viruses & Spam
Convergence quagmire viruses with spam is a growing threat in the digital landscape. Malicious actors are increasingly combining viral and…
Read More » -
Digital Issues

Spam Proliferation Continues Despite Federal Law
Spam proliferation continues despite federal law, highlighting the ongoing struggle to combat this pervasive digital problem. From phishing scams targeting…
Read More » -
Computer Security

Free Utilities to Annihilate Spyware A Comprehensive Guide
Free utilities to annihilate spyware are a crucial tool for safeguarding your digital life. This guide delves into the world…
Read More » -
Technology Law

Compliance with Internet Wiretap Rule Debated A Deep Dive
Compliance with internet wiretap rule debated is a complex issue with a long history, sparking heated discussions about privacy, security,…
Read More »

