network security
-
Network Security

Patrolling Network Security with Nettrooper
Patrolling network security with Nettrooper is crucial in today’s interconnected world. Nettrooper proactively monitors and protects your network infrastructure, identifying…
Read More » -
Technology

Checkpoint Expands Security Reach with Acquisitions
Check point expands security reach with three acquisitions – Checkpoint expands security reach with three acquisitions, marking a significant move…
Read More » -
Business Management

Companies Not Keeping Up Network Security Needs
Companies not keeping up with network security needs is a serious issue. Many companies are falling behind in protecting their…
Read More » -
Cybersecurity

Evil Twins A Wireless Security Nightmare
Evil twins a menace to wireless security pose a significant threat to the security of wireless networks. They are a…
Read More » -
Network Security
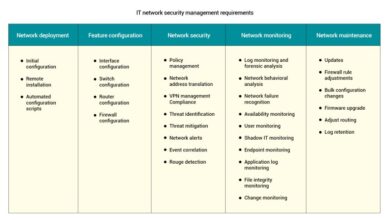
Network Security Evolving to Unified Management Approach
Network security evolving to unified management approach is reshaping how we safeguard our digital infrastructure. The fragmented, siloed systems of…
Read More » -
Software Reviews
Imlogic Releases Free IM and P2P Blocking Software
Imlogic releases free IM and P2P blocking software, offering a powerful new tool for users seeking to enhance their online…
Read More » -
Network Security

Closing Up Wireless Security Holes A Deep Dive
Closing up wireless security holes is crucial in today’s interconnected world. This deep dive explores the vulnerabilities lurking in our…
Read More » -
Technology

Microsoft Cisco Sharing Network Security Tech
Microsoft Cisco to share network security technologies promises a powerful synergy in the cybersecurity landscape. This collaboration combines Microsoft’s robust…
Read More » -
Virus Outbreak Filters New Tool to Block Infections
Virus outbreak filters new tool to block infections are rapidly becoming a critical component of modern cybersecurity. These sophisticated systems…
Read More » -
Technology History

PacketHop, Nortel & Homeland Security A Look Back
PacketHop Nortel join on homeland security, offering a fascinating glimpse into the past and potential future of network security. This…
Read More »

