security
-
Tech Security

Malware Renders PSP Useless A Deep Dive
Malware renders PSP useless, crippling this once-popular handheld gaming device. This comprehensive guide explores the various types of malware, their…
Read More » -
Cybersecurity

Firms Come Together to Fight Phishing Attacks A Collaborative Approach
Firms come together to fight phishing attacks, recognizing the escalating threat of these sophisticated scams. This collaborative approach underscores the…
Read More » -
Cybersecurity

Security Attacks on Software Increasing Report
Report suggests security software attacks increasing, highlighting a concerning trend in the digital landscape. Malicious actors are increasingly targeting software…
Read More » -
Technology

Hackers Break In to Sony PSP A Deep Dive
Hackers break in to sony psp, exploiting vulnerabilities in the popular Sony PlayStation Portable (PSP). This exploration delves into the…
Read More » -
Technology

Researchers Aim to Protect DVDs with RFID
Researchers aim to protect DVDs with RFID, a fascinating new approach to securing physical media. RFID technology, already prevalent in…
Read More » -
Technology
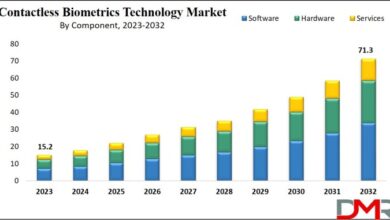
Biometric Cell Phones US Market Lag
Biometric cell phones on slow track to us market are a fascinating area of tech development. While other regions are…
Read More » -
Technology & Security

Google Plugs Desktop Search Security Gap A Deep Dive
Google Plugs Desktop Search Security Gap: This exploration delves into the potential vulnerabilities within Google’s desktop search functionality. From its…
Read More » -
Technology

Microsoft Adds Spyware Weapon to Arsenal A Dangerous Trend
Microsoft adds spyware weapon to arsenal, a move that has sent ripples through the tech world. This isn’t just about…
Read More » -
History of Technology

Netscape Prototype Browser More Secure?
Netscape prototype browser more secure says analyst, sparking debate about the early web’s security measures. This analysis delves into the…
Read More »


