security
-
Technology
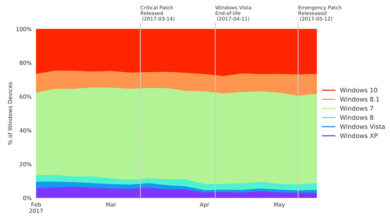
Microsoft Issues New Round of Critical Patches
Microsoft issues new round of critical patches, addressing serious vulnerabilities impacting various software components. These patches are crucial for maintaining…
Read More » -
Technology & Security
Instant Messaging New Security Holes Open
Instant messaging opens new security holes, exposing vulnerabilities in everyday communication. From the rise of ubiquitous platforms like WhatsApp and…
Read More » -
Technology

Federated Identity Standards Confused A Deep Dive
Federated identity standards confused are causing headaches for many organizations and developers. This complex topic involves various technologies like SAML…
Read More » -
Security
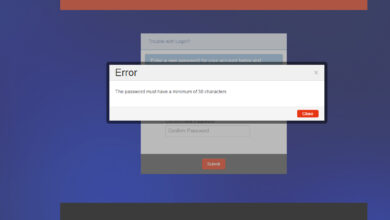
Passwords Fail the Security Test A Deep Dive
Passwords fail the security test, a disheartening reality for many online users. Weak passwords, predictable patterns, and easily guessed information…
Read More » -
Computer Security

Free Utilities to Annihilate Spyware A Comprehensive Guide
Free utilities to annihilate spyware are a crucial tool for safeguarding your digital life. This guide delves into the world…
Read More » -
Technology

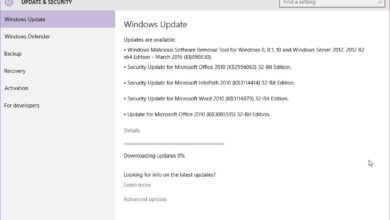
Microsoft Planning to Push Patches Harder
Microsoft planning to push patches harder is a significant shift in their approach to software security. This increased frequency is…
Read More » -
Technology

Parc Aims to Smarten Lockdown Mobile Tech
Parc aims to smarten lock down mobile tech – Parc aims to smarten lockdown mobile tech by developing innovative solutions…
Read More » -
Technology

Microsoft Locks Down Developer Tools Impact & Implications
Microsoft moves to lock down developer tools, a significant shift that’s stirring up debate and raising eyebrows in the tech…
Read More » -
Technology

What If Microsoft Got Security Right?
What if Microsoft got security right? This sets the stage for a fascinating exploration of the ripple effects such a…
Read More »