Toward Federated Identity Management A Deep Dive
Toward federated identity management, a crucial aspect of modern digital interactions, enables seamless user experiences across diverse platforms. This system allows users to access multiple services using a single identity, fostering a more secure and user-friendly environment. This detailed exploration dives into the core concepts, benefits, and practical applications of federated identity management, from its architectural underpinnings to the security considerations.
This post will Artikel the fundamentals of federated identity management, including its core principles, technological underpinnings, and various use cases. It will also discuss security and privacy concerns and highlight emerging trends in the field. We will explore the benefits of adopting federated identity management over traditional centralized systems, illustrated with clear comparisons and real-world examples. Expect a deep dive into the topic, complete with diagrams and tables.
Introduction to Federated Identity Management
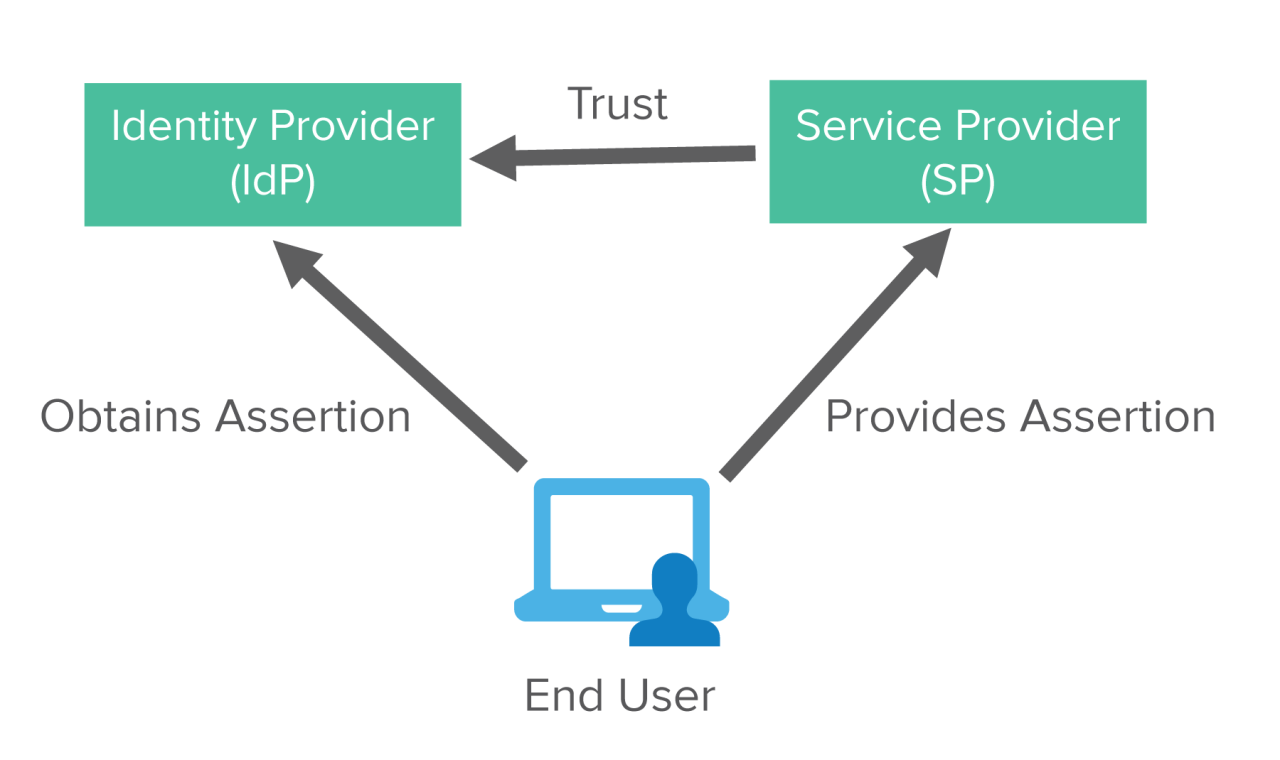
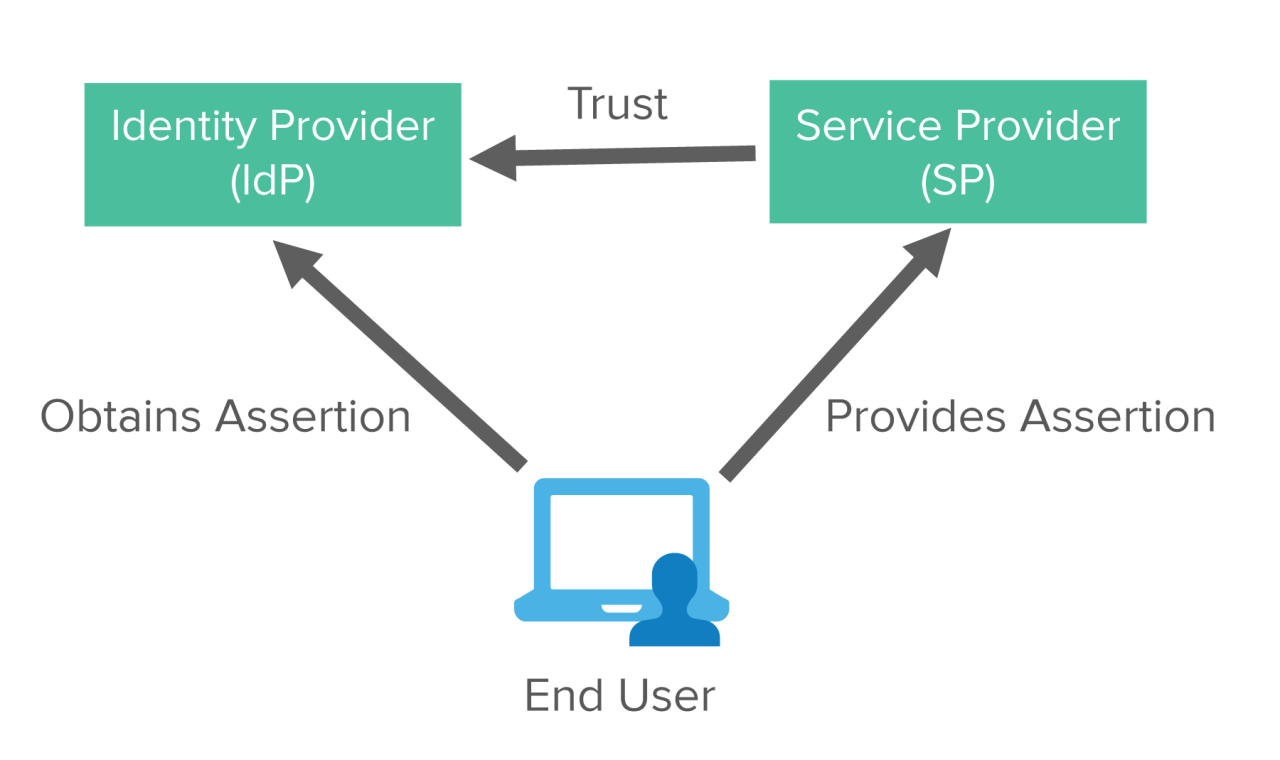
Federated Identity Management (FIM) is a system for securely verifying users’ identities across multiple organizations or platforms without requiring them to create and manage separate accounts for each service. It leverages a trust framework, allowing users to log in once and access multiple applications and resources, greatly enhancing user experience and simplifying IT management. This approach contrasts with traditional centralized identity systems, which often involve a single, overarching authority managing all user accounts.Federated identity relies on the principle of trust between different entities.
This trust is established through predefined agreements and protocols, allowing one entity to recognize and validate the identity of a user verified by another entity. This trust relationship is crucial for enabling seamless access across various systems. The core concepts behind federated identity include identity providers (IdPs), service providers (SPs), and identity assertions. IdPs are responsible for authenticating users, while SPs are the applications or services that users wish to access.
Identity assertions contain verifiable information about a user, allowing SPs to verify the user’s identity without needing to maintain their own authentication systems.The benefits of adopting federated identity management are numerous. Increased user convenience, simplified access to multiple applications, and reduced administrative overhead are key advantages. By reducing the need for users to remember multiple passwords and manage various accounts, federated identity systems enhance user experience and improve security.
Moreover, federated identity management streamlines IT administration by reducing the complexity of managing user accounts across disparate systems.Several organizations are already leveraging federated identity. For instance, many educational institutions use federated identity to allow students and faculty to access various university resources and services with a single login. Similarly, businesses often use federated identity to enable employees to access company applications and data from different locations and devices.
Even online communities and forums sometimes employ federated identity to facilitate user authentication and streamline access to their platforms.
Comparison of Federated and Centralized Identity Systems
Federated identity management offers a flexible and scalable approach to managing user identities, while centralized identity systems provide a more unified and controlled environment. The table below Artikels a comparison of these two models.
| Feature | Federated | Centralized |
|---|---|---|
| Identity Provider | Multiple organizations manage user identities | Single organization manages all user identities |
| Trust Model | Based on pre-established trust agreements between entities | Relies on a single authority’s trust model |
| Scalability | Highly scalable, accommodating a large number of users and organizations | Scalability depends on the capacity of the central system |
| Flexibility | Highly flexible, adaptable to different organizational structures and needs | Less flexible, potentially hindering adaptation to changing requirements |
| Cost | Potentially higher initial setup cost, but long-term costs can be lower due to reduced maintenance and management overhead. | Lower initial setup cost, but ongoing maintenance and management costs can be higher due to central system upkeep. |
Key Technologies and Standards
Federated identity management relies on a network of interconnected systems, each with its own identity store. This interoperability hinges on well-defined technologies and standards, enabling seamless user authentication and authorization across different platforms and organizations. Without these, federated systems risk fragmentation and user confusion.The success of federated identity management depends critically on the ability of different systems to communicate and trust each other.
This necessitates a common language and agreed-upon procedures, which are precisely what standards provide. They ensure that diverse systems can interact without requiring significant custom integrations.
Key Enabling Technologies
Federated identity management leverages several key technologies. These include secure communication protocols like HTTPS for secure transmission of user credentials, authentication protocols like OAuth 2.0 and OpenID Connect for authorizing access to resources, and identity providers (IdPs) to manage user identities and authorization. A robust infrastructure of these components is essential for a functional federated identity system.
Role of Standards in Federated Identity Systems
Standards play a crucial role in federated identity systems. They establish common protocols and data formats that ensure interoperability between different identity providers and service providers. This facilitates the smooth flow of user authentication and authorization data, preventing issues that might arise from different systems using incompatible technologies. Standards also enhance security by providing a baseline for secure communication and data handling practices.
Prominent Industry Standards for Federated Identity
Several prominent standards are instrumental in federated identity management. These include:
- SAML (Security Assertion Markup Language): A widely used standard for exchanging authentication and authorization assertions between different parties. It uses XML to define the assertions and is frequently used for single sign-on (SSO) across multiple applications.
- OpenID Connect (OIDC): A modern, open standard built upon OAuth 2.0. It provides a framework for user authentication and authorization, enabling users to access resources from various service providers without re-authentication. OIDC is well-suited for web and mobile applications, especially in modern applications needing user identity management.
- OAuth 2.0: A framework for authorization that allows users to grant limited access to their resources to third-party applications without compromising their credentials. It provides a mechanism for securely granting access tokens for specific applications, which is essential for federated identity systems.
Interoperability Challenges in Federated Identity
Despite the existence of these standards, interoperability challenges persist in federated identity systems. Different implementations of standards, varying security requirements across organizations, and the sheer complexity of managing identities across diverse systems can create obstacles. Migrating to a federated identity system can be complex and costly, necessitating careful planning and a phased implementation approach.
Security Considerations for Federated Identity Systems
Security is paramount in federated identity systems. Considerations include securing communication channels, protecting user data, and managing access rights to sensitive information. Implementing robust authentication mechanisms and regularly reviewing and updating security protocols are essential for safeguarding user identities and preventing breaches. Strong password policies, multi-factor authentication (MFA), and data encryption are all critical security measures.
Popular Identity Providers and Their Features
The following table showcases popular identity providers and their key features:
| Provider | Feature 1 | Feature 2 | Feature 3 |
|---|---|---|---|
| Okta | Multi-factor authentication | Single sign-on (SSO) | Scalable identity management |
| Auth0 | OpenID Connect support | API-first approach | Customizable user interfaces |
| Azure Active Directory | Hybrid identity support | Integration with Microsoft services | Strong security features |
Architecture and Design Considerations
Federated Identity Management (FIM) systems are crucial for enabling seamless access to resources across different organizations and platforms. Understanding the architectural models, components, and security considerations is vital for designing robust and maintainable FIM solutions. This section delves into the specifics of architecture, highlighting key design principles and practical implementation strategies.Designing a federated identity system requires careful consideration of its architecture, components, and interaction patterns.
The system needs to be adaptable, secure, and scalable to meet evolving user needs and organizational requirements.
Architectural Models for Federated Identity Systems
Federated identity systems employ various architectural models, each with unique characteristics and trade-offs. The most common models include the decentralized model, where each organization maintains its own identity infrastructure, and the centralized model, where a central authority manages identities for multiple organizations. Hybrid models combine elements of both decentralized and centralized approaches.
Components and Interactions in a Federated Identity System, Toward federated identity management
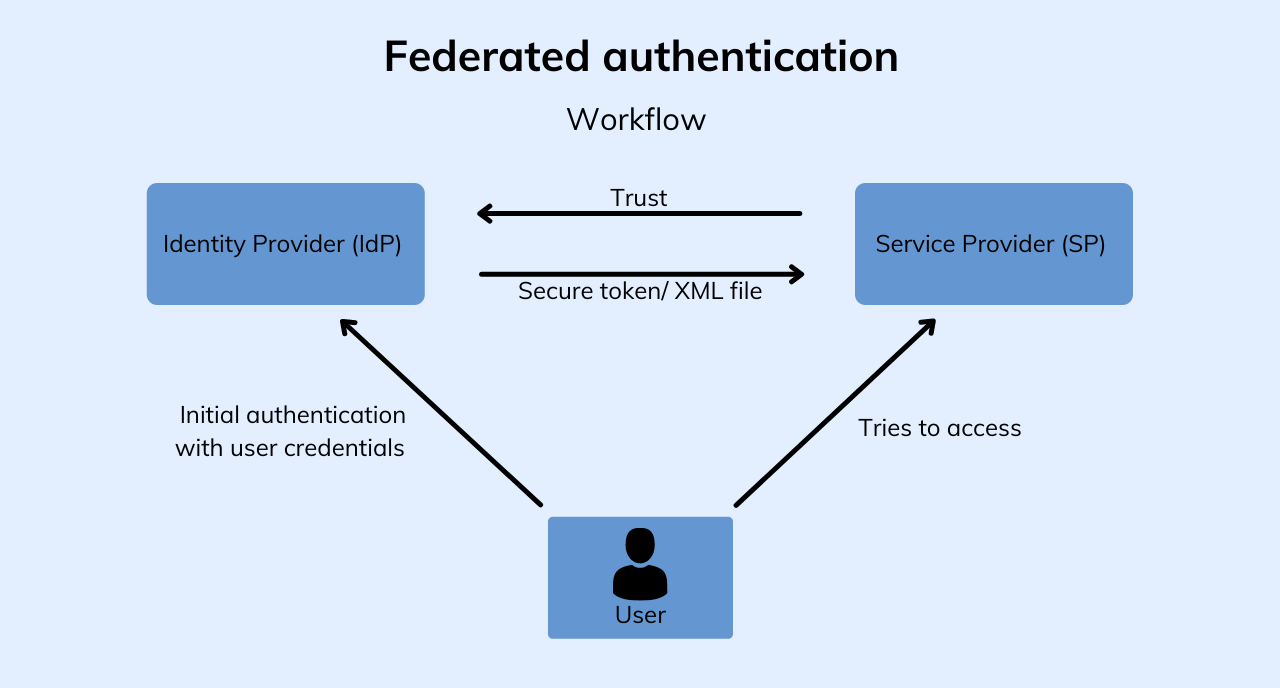
A typical federated identity system comprises several key components. These include Identity Providers (IdPs), which manage user identities within an organization; Service Providers (SPs), which require user authentication to grant access to their resources; and a central authority or federation, responsible for facilitating interactions between IdPs and SPs. The interaction between these components involves secure communication protocols, such as SAML (Security Assertion Markup Language) or OAuth 2.0, for exchanging authentication and authorization information.
User Authentication and Authorization in a Federated Environment
User authentication in a federated environment involves a series of steps. First, a user attempts to access a resource managed by an SP. The SP then redirects the user to the IdP for authentication. Upon successful authentication at the IdP, the IdP issues an assertion containing the user’s identity information to the SP. The SP validates the assertion and grants access to the resource if the user is authorized.
Authorization checks are performed based on roles, permissions, or other criteria defined by the SP.
Scalability and Maintainability Considerations
Federated identity systems must be designed for scalability to handle increasing numbers of users and resources. Scalability strategies include distributing the load across multiple servers and utilizing caching mechanisms. Maintaining a federated system requires careful documentation, modular design, and regular updates to address security vulnerabilities and enhance functionality. Regular audits and adherence to best practices for system maintenance are essential.
Security Best Practices for Implementing Federated Identity
Security is paramount in federated identity systems. Best practices include employing strong encryption for data transmission, implementing multi-factor authentication (MFA) for enhanced security, and regularly auditing the system for vulnerabilities. Implementing least privilege access controls, rigorous access management, and incident response plans are also crucial to safeguard the system against malicious activities.
Diagram of User Authentication Flow
| Step | Description |
|---|---|
| 1. User Request | User initiates access request to a service provider (SP) resource. |
| 2. SP Redirect | SP redirects the user to the Identity Provider (IdP). |
| 3. IdP Authentication | User authenticates with the IdP using their credentials. |
| 4. Assertion Issuance | IdP issues an authentication assertion containing user information to the SP. |
| 5. Assertion Validation | SP validates the assertion from the IdP. |
| 6. Resource Access | If validation succeeds, SP grants access to the requested resource. |
Use Cases and Applications
Federated identity management isn’t just a theoretical concept; it’s a powerful tool with real-world applications across various sectors. Its ability to seamlessly connect different systems while maintaining user privacy and security makes it invaluable for modern organizations. From streamlining employee access to facilitating secure data sharing, federated identity is revolutionizing how we interact with digital services.
Diverse Use Cases
Federated identity finds its footing in a wide range of applications. It empowers organizations to grant secure access to resources without the need for complex, individualized credentials for each platform. This allows users to leverage their existing identities to access various services, streamlining the authentication process and significantly improving the user experience.
Examples in Specific Industries
Federated identity is particularly beneficial in industries where collaboration and data sharing are crucial. In the healthcare sector, for example, it allows patients to securely access their medical records across different providers. This eliminates the need for multiple logins and passwords, enhancing patient convenience and care coordination. Similarly, in the financial sector, it supports secure transactions and account access across various institutions, fostering trust and confidence among users.
Educational institutions also benefit from federated identity, enabling seamless access to various learning platforms and resources.
Moving toward federated identity management is crucial for streamlining access and security in today’s interconnected world. This approach promises to make authentication simpler and more secure. Interestingly, SGI’s recent introduction of the quad processor workstation, as detailed in this article ( sgi introduces quad processor workstation ), highlights the need for robust computing power to handle the complexities of a federated system.
This advanced hardware underscores the importance of efficient identity management for future technological advancements.
Supporting Collaboration and Data Sharing
Federated identity is the bedrock for effective collaboration and data sharing. By allowing users to access resources from multiple systems using a single identity, it simplifies the process and encourages data exchange across organizations. This is particularly important in scenarios where multiple entities need to collaborate, such as research projects, joint ventures, or inter-agency initiatives.
Moving toward federated identity management is crucial for seamless access control, but it’s also about broader infrastructure improvements. IBM and Cisco’s recent work on widening SAN coverage, as detailed in ibm and cisco sync widen san coverage , is a perfect example. This kind of strategic partnership helps pave the way for more secure and efficient identity management solutions across distributed environments.
Ultimately, it all contributes to a more robust and reliable approach to federated identity management.
Improving User Experience
Federated identity streamlines the user experience by reducing the burden of managing multiple accounts and passwords. Users can seamlessly transition between different platforms, benefiting from a single sign-on (SSO) experience. This ease of access, combined with the security provided by federated identity, leads to a significant enhancement in the overall user experience.
Practical Applications in the Cloud
In the cloud environment, federated identity management plays a pivotal role in securing access to applications and data. Cloud services often rely on multiple platforms and applications, and federated identity ensures a unified approach to authentication and authorization. This simplifies the user experience and strengthens the overall security posture of the cloud infrastructure. Furthermore, it facilitates seamless integration with existing on-premises systems, enabling a smooth transition to a cloud-based environment.
Table of Use Cases and Benefits
| Use Case | Benefit 1 | Benefit 2 | Benefit 3 |
|---|---|---|---|
| Secure Access to Healthcare Records | Streamlined access for patients | Improved care coordination | Enhanced patient experience |
| Financial Transactions Across Institutions | Secure transactions | Enhanced user trust | Improved customer satisfaction |
| Educational Resource Access | Simplified access to learning platforms | Reduced administrative burden | Enhanced student experience |
| Collaboration in Research Projects | Facilitated data sharing | Streamlined access to resources | Enhanced efficiency |
Security and Privacy in Federated Identity: Toward Federated Identity Management
Federated identity management, while offering significant benefits in terms of user experience and scalability, introduces new security and privacy concerns. Careful consideration of these issues is paramount for successful implementation and user trust. This section explores the potential vulnerabilities and Artikels proactive measures to safeguard user data and maintain privacy.Federated identity relies on multiple parties sharing user data, creating a complex network of potential entry points for malicious actors.
Therefore, robust security protocols and comprehensive privacy policies are essential for ensuring the integrity and confidentiality of user information.
Potential Security Risks
Federated identity systems are vulnerable to various attacks, including man-in-the-middle (MitM) attacks, phishing, and compromised identity providers. Malicious actors can intercept authentication tokens or manipulate data flowing between different organizations. Data breaches at any participating identity provider can compromise user data across the entire federation. Insufficient access controls and weak authentication mechanisms also pose significant security risks.
Mitigation Measures
Several strategies can mitigate these risks and strengthen the security of federated identity systems. Implementing strong encryption throughout the communication channels is critical. This ensures that intercepted data remains unreadable to unauthorized parties. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to gain access even with compromised credentials. Regular security audits and penetration testing help identify vulnerabilities and address them proactively.
User Privacy Concerns
Federated identity systems raise user privacy concerns due to the sharing of data across different organizations. Users need assurance that their data is being handled responsibly and that their privacy rights are respected. Clear and transparent privacy policies, outlining how data is collected, used, and protected, are essential. Users should have control over their data and the ability to access, modify, or delete it as needed.
Data Encryption and Access Controls
Data encryption plays a crucial role in safeguarding sensitive information. Encryption ensures that even if data is intercepted, it remains unintelligible without the appropriate decryption key. Robust access controls are equally important, restricting access to user data only to authorized personnel and systems. Implementing role-based access control (RBAC) can help achieve this, granting different levels of access based on user roles and responsibilities.
Secure User Authentication
Implementing secure user authentication in a federated environment requires careful consideration of various factors. Strong password policies, regular password updates, and phishing awareness training for users can significantly reduce the risk of credential compromise. Employing a strong password hashing algorithm is also critical. Using a robust authentication framework, like OAuth 2.0, and ensuring compliance with industry best practices further enhance the security posture.
Multi-Factor Authentication Implementation
Multi-factor authentication (MFA) is a critical component of securing user accounts in a federated identity system. MFA requires users to provide multiple forms of verification, such as a password, a one-time code sent to their phone, or a biometric scan. This adds an extra layer of security, making it significantly more difficult for attackers to gain access to accounts even if they have compromised passwords.
Different MFA methods, such as time-based one-time passwords (TOTP) or hardware tokens, offer various levels of security and convenience.
Moving toward federated identity management is crucial for a more secure digital future. Imagine a world where seamless access to services is the norm, and the need for multiple logins becomes a relic of the past. This could be facilitated by advancements like Broadcom’s new all-in-one Wi-Fi chip, which promises to simplify networking infrastructure. Ultimately, a more unified approach to network security and access management will be essential for truly federated identity management to flourish.
Emerging Trends and Future Directions
Federated Identity Management (FIM) is rapidly evolving, driven by the increasing need for secure and seamless access to digital resources. Emerging trends highlight a shift towards more user-centric, flexible, and robust systems. The future of FIM promises significant advancements, potentially revolutionizing how we manage and authenticate identities across diverse platforms.
Emerging Trends in Federated Identity Management
The field of federated identity management is experiencing several key trends. These include the growing adoption of decentralized identity solutions, increased focus on security and privacy, and the integration of emerging technologies like AI and machine learning. The future of FIM is moving beyond traditional approaches to leverage new possibilities and address evolving security needs.
Innovative Solutions and Technologies
Several innovative solutions are emerging to address the complexities of federated identity. Self-sovereign identity (SSI) models, where individuals control their digital identities and data, are gaining traction. Blockchain technology is being explored for enhanced security and immutability in identity management systems. These approaches offer significant advantages in terms of user control and data privacy, although scalability and interoperability challenges remain.
Decentralized identity platforms, allowing individuals to manage their identities across various services without a central authority, are another example.
Role of AI and Machine Learning in Federated Identity
AI and machine learning (ML) are poised to play a significant role in enhancing federated identity management. AI can be used to improve authentication methods by detecting anomalies and preventing fraudulent access attempts. ML algorithms can analyze user behavior patterns to identify potential security risks and adjust security protocols dynamically. For example, AI can be used to create more sophisticated risk assessment models for access approvals, enabling a more granular and personalized approach to security.
Another example involves using machine learning to identify potentially malicious actors by analyzing their interaction patterns with the system.
Summary of Emerging Trends
- Increased adoption of decentralized identity solutions, empowering users with greater control over their data.
- Focus on enhancing security and privacy through advanced authentication methods and data protection measures.
- Integration of emerging technologies like AI and machine learning for improved security and user experience.
- Exploration of blockchain technology for enhanced security and immutability in identity management systems.
- Development of self-sovereign identity (SSI) models, granting users greater control over their digital identities.
Comparison of Identity Federation Approaches
The table below highlights the strengths and weaknesses of various approaches to identity federation.
| Approach | Strengths | Weaknesses |
|---|---|---|
| Centralized Identity | Simplified management, established standards, potentially lower initial setup costs. | Potential single point of failure, less user control, security concerns if the central authority is compromised. |
| Decentralized Identity | Greater user control, enhanced security through data decentralization, improved privacy. | Complexity in management, interoperability issues across different platforms, scalability challenges. |
| Federated Identity | Balance of control and management, leveraging existing infrastructure, improved security through multiple layers. | Complexity in managing multiple identities and systems, potential for inconsistencies across federated systems. |
Last Word
In conclusion, federated identity management is rapidly evolving to meet the needs of a connected world. By streamlining authentication and authorization processes, it fosters collaboration, enhances security, and provides a positive user experience. While security and privacy remain paramount concerns, the potential benefits of this approach are significant, paving the way for a more secure and efficient digital ecosystem.
The future looks bright for federated identity management, with ongoing innovation driving its evolution.