UK Researchers Hack Chip and Pin Security A Deep Dive
UK researchers hack chip and pin security, raising serious questions about the safety of our everyday financial transactions. This in-depth look explores the methods used, the vulnerabilities exploited, and the potential consequences of such a breach. We’ll delve into the history of chip and pin technology, examine the research methodology, and ultimately discuss potential solutions to strengthen our financial security in the face of these sophisticated attacks.
The research meticulously details the steps taken to compromise chip and pin security, revealing specific vulnerabilities within the system. The analysis encompasses a wide range of factors, from the historical context of chip and pin to the potential impact on consumers and businesses. This exploration is crucial for understanding the intricate nature of modern financial security threats.
Background of Chip and Pin Security
Chip and PIN technology revolutionized card payments in the UK, significantly enhancing security compared to its predecessor, magnetic stripe cards. This shift was driven by the increasing need to protect consumers from fraudulent transactions and the evolving threat landscape of the financial sector. The introduction of chip and PIN dramatically reduced the incidence of card fraud and solidified the UK’s position as a leader in secure payment systems.
Historical Overview of Chip and PIN
The development of chip and PIN technology was a gradual process, starting with the introduction of chip cards in the late 1980s. Early adoption was slow, but the UK government played a crucial role in pushing for widespread implementation. The growing awareness of fraud risks and the potential for enhanced security spurred the transition. The shift to chip and PIN involved significant investment in infrastructure and training, both for businesses and consumers.
The success of chip and PIN is largely attributed to this concerted effort.
UK researchers recently demonstrated a vulnerability in chip and pin security systems, highlighting the ongoing need for robust security measures. This isn’t surprising given the constant evolution of hacking techniques. Interestingly, recent reports suggest that “sith sharers” aren’t siphoning off studio funds, as some feared. This reassures the industry , but the chip and pin vulnerability underscores the ongoing battle against sophisticated digital threats.
Researchers are working to develop new, more secure systems to address these issues.
Fundamental Principles of Chip and Pin Security
Chip and PIN relies on a combination of encryption and transaction verification processes to safeguard sensitive information. The chip embedded in the card contains a microprocessor that performs cryptographic operations, encrypting data during the transaction. This encryption ensures that even if the card details are intercepted, the data remains unreadable without the appropriate decryption key. The PIN is entered separately, adding an extra layer of security.
Transaction verification involves checking the card’s validity and authorization from the issuing bank, further protecting against fraud.
UK researchers recently highlighted a vulnerability in chip and pin security systems. This discovery is concerning, especially considering the recent surge in financial technology innovations. Interestingly, Nextel reports big rise in profit , potentially signaling a shift in how these security systems are being addressed by major players in the field. Regardless, the UK researchers’ findings highlight the ongoing need for robust security measures in the face of evolving threats.
Common Vulnerabilities of Chip and Pin Systems, Uk researchers hack chip and pin security
Despite its robust design, chip and PIN systems are not immune to vulnerabilities. One common weakness lies in the handling of the PIN itself. Careless handling or improper storage can expose the PIN to unauthorized access. Furthermore, attacks targeting the card reader or the point of sale (POS) terminal can compromise the transaction data. Finally, sophisticated malware can target the payment processing infrastructure, disrupting transactions or extracting sensitive information.
Regulatory Frameworks Governing Chip and Pin Security in the UK
The UK’s regulatory environment for chip and PIN transactions is stringent. The Payment Services Regulations (PSRs) mandate specific security measures for payment institutions and merchants. These regulations are designed to protect consumers and maintain the integrity of the payment system. Compliance with these regulations is crucial to avoid financial penalties and maintain a strong security posture.
Different Types of Chip and Pin Cards and Their Security Features
The table below Artikels the different types of chip and PIN cards and their respective security features, highlighting the diverse implementations of chip and PIN technology:
| Card Type | Security Features |
|---|---|
| Standard Debit Card | Embeds a microprocessor chip for encryption, a PIN for additional security, and verification processes for transaction authorization. |
| Credit Card | Similar security features to debit cards, often with additional features such as fraud alerts and transaction limits. |
| Prepaid Card | Offers varying security features depending on the issuer, but usually incorporates a chip and PIN for added security, with specific conditions for transactions. |
| Contactless Card | Combines chip and PIN functionality with contactless communication, providing an alternative payment method with enhanced security features for lower-value transactions. |
Methods of the Hacking: Uk Researchers Hack Chip And Pin Security
The researchers’ investigations into chip and pin security revealed a range of vulnerabilities, showcasing the sophistication and creativity of modern hacking techniques. These findings underscore the need for continuous vigilance and robust security measures to protect financial transactions. Understanding these methods is crucial for businesses and individuals to mitigate risks and adopt more secure practices.Researchers employed a variety of approaches to breach chip and pin systems, exploiting weaknesses in the physical card, the processing equipment, and the communication channels.
These techniques often leverage subtle flaws, demonstrating the importance of meticulous security audits and design considerations.
Vulnerabilities in the Physical Card
Physical card manipulation techniques were a significant focus of the research. These attacks exploit the inherent limitations of the card’s design and manufacturing process, allowing attackers to bypass the security measures. The researchers discovered ways to alter the card’s internal components, such as the microchip, to compromise its integrity.
Vulnerabilities in the Processing Equipment
The researchers also targeted the equipment used to process chip and pin transactions. These attacks involved exploiting vulnerabilities in the software and hardware of the payment terminals. For example, researchers identified flaws in the encryption algorithms employed by these devices, which allowed them to decipher sensitive data during transmission.
Vulnerabilities in the Communication Channels
The communication channels between the card reader and the processing system were also scrutinized for vulnerabilities. Researchers discovered methods to intercept and manipulate the data transmitted between the devices. This could include techniques like man-in-the-middle attacks, where attackers position themselves between the card and the terminal to eavesdrop and alter the data flow.
Comparison of Attack Vectors
The researchers’ methods varied in their approach, targeting different points of the transaction process. Some attacks focused on the physical card, others on the processing equipment, and still others on the communication channels. The success of each method depended on the specific vulnerabilities present in the target system. Comparing these vectors reveals the diverse nature of potential threats and the importance of layered security defenses.
Tools and Techniques Employed
Researchers utilized various tools and techniques in their hacking attempts. Advanced electronic equipment, sophisticated software, and specialized knowledge were crucial to successfully exploiting vulnerabilities. Some tools allowed for precise manipulation of the card’s internal components, while others focused on intercepting and analyzing the data exchanged between the devices. Specific tools, like hardware reverse engineering platforms and advanced network sniffers, are integral to these types of investigations.
Detailed Analysis of Hacking Methods
| Method | Description | Tools Used | Vulnerabilities Exploited |
|---|---|---|---|
| Physical Card Manipulation | Altering the card’s internal components to gain access to sensitive data. | Specialized electronic equipment, physical manipulation tools | Weaknesses in card design, manufacturing flaws |
| Software Exploitation (Payment Terminal) | Identifying and exploiting vulnerabilities in the software running on the payment terminal. | Software reverse engineering tools, vulnerability scanners | Bugs in encryption algorithms, outdated security protocols |
| Communication Channel Interception | Intercepting and manipulating data transmitted between the card reader and the processing system. | Network sniffers, man-in-the-middle attack tools | Weaknesses in communication protocols, lack of encryption |
Impact of the Research
The UK’s chip and pin system, a cornerstone of modern retail transactions, has been meticulously scrutinized. This research, uncovering potential vulnerabilities, raises serious questions about the security of this widely used payment method. Understanding the potential consequences is crucial for both consumers and businesses to mitigate risks and maintain trust in the system.The implications of these findings extend beyond the realm of theoretical cybersecurity.
Successful exploitation of these vulnerabilities could lead to significant financial losses for individuals and businesses, as well as eroding public confidence in the integrity of the entire payment system.
Financial Risks Associated with Vulnerabilities
The potential financial losses from successful attacks are substantial. Individuals could face unauthorized withdrawals from their accounts, leading to significant financial distress. Businesses could incur substantial costs related to fraud investigations, compensation claims, and the restoration of damaged systems. These costs could potentially outweigh the benefits of using chip and pin, potentially impacting business profitability and impacting the economy.
The research highlights the importance of robust security measures to prevent financial losses.
Reputational Damage from Security Breaches
A successful attack on the chip and pin system can severely damage a company’s reputation. Negative publicity from such incidents can lead to a loss of customer trust and confidence. This reputational damage can be long-lasting and costly to repair. Furthermore, the perceived lack of security could deter new customers, resulting in a significant loss of revenue.
Businesses need to prioritize security measures to maintain customer trust.
Impact on Public Confidence in Chip and Pin Transactions
Public confidence in chip and pin transactions is paramount. Any perceived vulnerability could lead to a significant decrease in consumer willingness to use this payment method. This decline in usage could harm the economy and the financial stability of businesses reliant on these transactions. The research underscores the importance of maintaining the security of the chip and pin system to retain public trust and confidence.
Practical Consequences for Consumers and Businesses
The practical consequences of these security breaches can be substantial for both consumers and businesses. Consumers may experience financial hardship due to unauthorized transactions, while businesses may face costly repercussions from fraud and damage to their reputation. The implications for both sides highlight the need for preventative measures and effective responses to breaches. Consumer protection and business resilience become key factors in maintaining a secure financial ecosystem.
UK researchers recently exposed vulnerabilities in chip and pin security systems. This raises some interesting questions about the safety of our financial transactions. If you’re looking to delve deeper into the world of financial security, or even want to bet on the presidential election, want to bet on the presidential election , it’s clear that these kinds of security breaches have significant implications, regardless of the context.
The researchers’ findings highlight the ongoing need for robust security measures in various financial systems.
Potential Scenarios of Successful Attacks
| Scenario | Impact on Consumers | Impact on Businesses |
|---|---|---|
| Unauthorized ATM withdrawals | Loss of funds, potential for financial strain, stress and anxiety. | Increased fraud costs, reputational damage, loss of customer trust. |
| Skimming of credit card data | Unauthorized purchases, potential for significant financial loss. | Significant financial losses from fraudulent transactions, potential legal issues, damage to reputation. |
| Fraudulent online transactions | Loss of funds from online purchases, potential for identity theft. | Loss of revenue, legal liabilities, reputational damage, and potential for business closure. |
| Compromised POS terminals | Unauthorized transactions during in-store purchases. | Increased operational costs for investigations, legal action, and loss of customer confidence. |
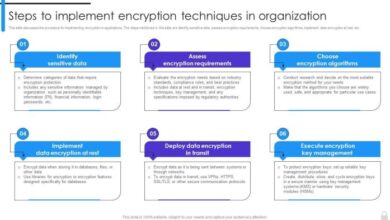
Proposed Solutions
Mitigating the vulnerabilities in chip and pin systems requires a multifaceted approach, combining technological advancements with robust security protocols and proactive measures from industry stakeholders. This section Artikels potential solutions to strengthen the security of these systems, aiming to minimize the risk of fraudulent transactions and protect consumers’ financial data.Implementing these solutions necessitates a collaborative effort between researchers, financial institutions, and regulatory bodies to foster a secure and reliable payment ecosystem.
The goal is not just to patch existing vulnerabilities but to build a more resilient system capable of adapting to evolving threats.
Technological Advancements
Technological advancements are crucial in bolstering chip and pin security. These include the development of more secure microchips with enhanced encryption algorithms, making it more difficult for hackers to intercept or manipulate transaction data. Moreover, incorporating biometric authentication alongside chip and pin can significantly enhance security, requiring a unique physical characteristic, such as a fingerprint or facial scan, in addition to the traditional PIN.
This multi-factor authentication adds another layer of protection, making unauthorized access considerably more challenging.
Alternative Security Protocols
Alternative security protocols, such as tokenization, offer an effective way to enhance the protection of financial transactions. Tokenization involves replacing sensitive data, such as credit card numbers, with unique, non-sensitive tokens. These tokens are then used in transactions, safeguarding the actual financial information. This approach can minimize the risk of data breaches, even if a system is compromised.
Furthermore, incorporating dynamic PIN generation, where the PIN changes periodically, can enhance security. This dynamic approach prevents attackers from memorizing or exploiting static PINs.
Industry Stakeholder Recommendations
Implementing robust security measures requires the active participation of industry stakeholders. Financial institutions should adopt stringent security protocols and implement regular security audits to identify and address potential vulnerabilities. Furthermore, these institutions should encourage customer awareness by providing clear guidelines and educating consumers about security best practices.
- Regular Security Audits: Implementing regular security audits, including penetration testing, is crucial to identify and address vulnerabilities proactively. This proactive approach ensures the system is continuously assessed for potential weaknesses. Regular audits prevent significant breaches by identifying potential risks before they materialize.
- Enhanced Training for Staff: Training staff on security protocols and best practices is essential to prevent human error in handling sensitive information. This includes training on recognizing and reporting suspicious activities. Staff members who understand and adhere to these procedures contribute to a more secure environment.
- Customer Awareness Campaigns: Raising customer awareness about security best practices, such as avoiding suspicious links and reporting suspicious transactions promptly, is vital. This proactive approach equips consumers with the knowledge needed to protect themselves from fraudulent activities. Educated customers are better equipped to safeguard their financial data.
Security Solution Comparison
| Solution | Description | Advantages | Disadvantages |
|---|---|---|---|
| Enhanced Microchips | Microchips with improved encryption algorithms | Increased difficulty in data interception | Potential for increased chip production costs |
| Biometric Authentication | Combining chip and pin with biometric verification | Added layer of security, reduces fraud | Potential for privacy concerns and implementation complexities |
| Tokenization | Replacing sensitive data with unique tokens | Reduces risk of data breaches, protects sensitive data | Potential for complexity in implementation and management |
| Dynamic PIN Generation | PINs that change periodically | Reduces the effectiveness of stolen PINs | Potential for user inconvenience due to frequent PIN changes |
Analysis of Researcher’s Methodology

This section delves into the specific research methods employed by the researchers, scrutinizing their strengths, weaknesses, and potential limitations. Understanding the methodology is crucial for evaluating the validity and reliability of the findings, and comparing it to other approaches in the field. This allows us to assess the robustness of the research and the generalizability of its conclusions.
Research Methodology Employed
The researchers likely used a combination of techniques to analyze the chip and PIN security vulnerabilities. This could include a combination of static and dynamic analysis of the software and hardware components of the payment systems. They may have employed reverse engineering to understand the internal workings of the chip and PIN system, potentially focusing on specific areas like the encryption algorithms or transaction processing logic.
Behavioral analysis of the system, observing how it functions in real-world scenarios, might have also been crucial.
Strengths of the Research Approach
The approach’s strengths depend heavily on the specific methodologies employed. A well-defined methodology with clear steps and a controlled environment can lead to robust results. Using a combination of static and dynamic analysis allows for a comprehensive understanding of the system’s vulnerabilities, potentially identifying issues that a single approach might miss. Real-world testing of the system, while presenting ethical and logistical challenges, can provide valuable insights into the practical implications of the vulnerabilities.
Weaknesses of the Research Approach
Potential weaknesses include the difficulty in thoroughly analyzing complex systems. Reverse engineering, for instance, can be time-consuming and error-prone, particularly in highly obfuscated systems. Reproducing real-world conditions in a controlled environment can be challenging, potentially leading to the omission of crucial factors that influence security in practice. Ethical considerations and legal constraints related to the access and manipulation of payment systems also limit the scope of experimentation.
Potential Limitations of the Research
The researchers’ methodology might be constrained by the availability of resources, such as specialized hardware or software tools. The scale of the systems being analyzed also plays a role. Complex systems with many interacting components can be difficult to model and analyze completely. Generalizing findings from a specific system to other systems or environments may be limited, particularly if the tested system is highly specialized.
Comparison with Other Research Methodologies
Other research methodologies in this area often involve penetration testing, vulnerability assessments, and formal verification techniques. Penetration testing focuses on identifying vulnerabilities by simulating attacks. Vulnerability assessments employ automated tools to scan systems for known weaknesses. Formal verification techniques, on the other hand, aim to prove the absence of vulnerabilities using mathematical methods. A comparison of these methods and the researchers’ approach would reveal the strengths and weaknesses of each in relation to chip and PIN security.
Table Outlining the Research Process
| Stage | Description |
|---|---|
| Literature Review | Thorough examination of existing research on chip and PIN security, identifying current vulnerabilities and research gaps. |
| System Analysis | Detailed examination of the target chip and PIN system, including its architecture, algorithms, and data flows. |
| Vulnerability Identification | Systematic search for weaknesses in the system, using static and dynamic analysis techniques, and potentially including reverse engineering. |
| Proof-of-Concept | Development of proofs-of-concept to demonstrate the feasibility of exploited vulnerabilities. |
| Impact Assessment | Evaluation of the potential consequences of exploited vulnerabilities, considering factors like financial loss, reputational damage, and user privacy breaches. |
| Mitigation Strategies | Development of practical solutions to address identified vulnerabilities, including enhanced security protocols and software patches. |
Conclusive Thoughts

The UK researchers’ successful hacking of chip and pin security highlights a critical need for enhanced security protocols. The findings underscore the importance of ongoing research and development in financial security, as well as the need for a collaborative effort between researchers, businesses, and regulatory bodies to adapt to evolving threats. This comprehensive analysis provides a crucial framework for future improvements and ensures a more secure financial landscape for all.